The principle of operation of a virus miner is to get into the system and begin to consume computer resources, loading the processor or video card to the maximum in order to generate income for the attacker. Profit is accrued in BTC.
The program developer makes money on the power of other users’ equipment. A virus can cause the loss of personal data, disable the Windows operating system and facilitate the penetration of new threats. In this article, we will look at different methods of fighting malware.
What is hidden mining and its features
The emergence of a large number of cryptocurrencies that can be obtained through mining has inevitably attracted the attention of scammers. Almost immediately with the advent of legal mining, carried out by the owner of computing equipment, people began to want to use other people’s computers to mine cryptocurrencies. In order to avoid unnecessary attention, attackers began to use various methods to use the computing resources of other people's computers without anyone noticing, running mining programs in the background. This is how a new way of illegally making a profit was born - hidden mining (cryptojacking).
How to detect a hidden miner
If you start to notice that your computer is starting to slow down and get hot, the first thing you should do is run an antivirus scan with the latest databases. In the case of simple miners there should be no problems. The threat will be detected and eliminated. You will have to tinker with viruses that hide their presence well.
Systematic monitoring of the Task Manager, which on Windows can be opened using the key combination Ctrl + Alt + Del or Ctrl + Shift + Esc, will allow you to track hidden miners. For 10–15 minutes, you just need to observe active processes with complete inactivity. Close all programs and don’t even move your mouse.
If, in such a scenario, one of the active or suddenly appeared processes continues to load the hardware, this is a good reason to think about it. The origin of such a process can be checked using the “Details” tab or through an Internet search.
Many hidden miners, which mainly use the PC’s video card, may not load the central processor, which means they will not appear in the Task Manager on older versions of Windows. That is why it is better to assess the load on the hardware using specialized utilities such as AnVir Task Manager or Process Explorer. They will show much more than the standard Windows tool.
Scale of the disaster
Such programs are distributed among criminals as a service - for example, in the Telegram messenger, in channels dedicated to making money on the Internet, you can find advertisements offering a trial version of such a collector-packer for distributing a hidden miner.
To give you an idea of the scale of what is happening: our experts recently discovered a botnet consisting, according to rough estimates, of several thousand computers on which the Minergate miner was secretly installed. With its help, attackers do not mine the popular Bitcoin, but mainly those cryptocurrencies that allow them to hide transactions and who owns the wallet. For example, these are Monero (XMR) and Zcash (ZEC). According to the most conservative estimates, the mining botnet brings its owners at least $30,000 a month. And more than $200,000 has already passed through the wallet into which the botnet discovered by our experts mines.
Monero wallet used by the aforementioned botnet owners. At the moment, 1 Monero costs about $120
Scanning
Checking your computer for hidden miners should start with a standard antivirus installed on the system. Immediately after it, you can proceed to the programs strictly in the order indicated above in the previous section.
If you do not want to start scanning using a Live CD, then boot into safe mode (to minimize threat activity) and start from the second point. If the effect is insufficient, you must use a rescue disk.
Upon completion of the scan, remove the found mining viruses, clean them using the CCleaner program and restart your computer.
What is CPU Miner
CPU Miner is a virus that belongs to the adware subclass. This virus is automatically installed on your computer, after which it changes the start page of your browser and installs all kinds of advertising ads into it. Due to the presence of malware in the system registry, getting rid of CPU Miner is a difficult task. In most cases, this virus enters the system when downloading free software, all kinds of torrents, unofficial patches for computer games and other content from unreliable sites. The creators of these portals begin monetizing the content by wrapping the virus in a download file. A downloader is a special software that transfers downloaded content to you, while at the same time installing viruses that change the home page, install ads in the browser, install various redirects, and the like. CPU Miner belongs to the list of such programs.
- Remove CPU Miner automatically:
- Using Spyhunter 4
- Remove CPU Miner manually:
- Firefox
- Chrome
Viruses for mining on computers
The goal of this type of malware is to make your computer part of a botnet that combines the power of relatively weak devices for mining and other tasks. This is doubly profitable: firstly, attackers do not need to buy expensive miners or video cards, and secondly, they also do not have to pay for electricity.
Often, attackers use legal miners. But they install them without the knowledge of the device owner, hide the work of the miner and indicate their wallet for the mined coins.
Usually the miner gets to the computer using a dropper. This malware is often included in pirated versions of popular programs or activation key generators. After launching the file, an installer is installed on the victim’s computer, which directly downloads the miner and a utility to disguise it in the system.
Often, the kit includes tools for autorunning the malware and configuring its operation. These services can pause the miner when the user launches a game or other resource-intensive application. This way, the miner will not give himself away and will spend maximum time on the victim’s computer.
Modern miners are capable of self-healing, stopping the antivirus, monitoring system activity and mining only during periods of low load.
Is it possible to mine from a phone?
You can do cloud mining using your phone, but this will not be “mining” from a smartphone in the literal sense of the word. With cloud mining, the user only rents remote equipment and uses it to mine crypto. In this case, a phone number is needed to log into your account on the cloud mining service.
Interesting materials:
How to obtain the title of international master of sports? How to get Starbucks stars? How to use IQOS 2.4 instructions? How to use acrylic varnish for paintings? How to use two WhatsApp accounts? How to use a gas grill? How to use Yandex navigator on foot? How to use the diamond embroidery tool? How to use the Marusya column? How to use a quilling ruler?
How to find and protect your PC from hidden mining?
To protect against malware, you must perform the following steps:
- Install a reliable antivirus and regularly update its antivirus databases and scan to identify threats.
- Install only necessary programs on the operating system and restore it when the first signs of infection appear or once every 2-3 months as a preventive action.
- Add to the hosts file blocking malicious sites according to lists available on the open resource GitHub using the algorithm described in the section on protection against browser mining.
- Prevent installation of software on the operating system. To do this, you can disable the launch of Windows Installer: press Win+R, run the gredit.msc program, follow the path “Local Computer” - “Computer Configuration” - “Administrative Templates” and in the “Windows Installer” directory activate the “Disable” option in the menu "Disable Windows Installer."
- Allow only verified programs to run. To do this, you can change the local security policy by running the secpol.msc program, and also activate the “Ignore certificate rules” option.
- Allow access to the computer only on trusted ports. This is done in the firewall and antivirus settings.
- Prohibit remote access from the Internet to your home router, and also change the default password set on it (according to its operating instructions).
Precautionary measures
Precautionary measures when working on a computer can reduce the risk of infection by hidden miners, as well as other viruses. Simple safety rules when working on a computer are as follows:
- Do not use or install pirated software, as well as programs downloaded from unknown resources;
- Limit the list of people who have access to the computer. Set passwords and limit the ability of third parties to install programs.
- Enable a firewall on your computer and router, as well as use other types of protection that are supported by your specific router model.
- Limit as much as possible visiting sites with questionable content, avoid sites without ssl (https) certificates.
- Install special add-ons in your browser that block mining script codes on websites.
- As little as possible, disseminate information online that could facilitate hacking. Try not to store passwords and personal information.
- Regularly update the antivirus program and its database with virus definitions, as well as critical operating system security updates.
How to detect a hidden mining bot on your computer
The first thing you need to do is scan your computer with an antivirus; perhaps a miner has “settled” on your PC, which is not hidden from programs such as malwarebites.
Some malware may:
- turn off when working with “heavy” programs;
- hide in the task manager under other program labels;
- work only when there is no user activity.
If it seems to you that your PC is not working as fast as usual, and the antivirus does not show anything, you should do the following:
- check the activity of the device under normal load (using simple programs or a browser);
- try working in more “heavy” programs that heavily load the video card and processor (games);
- download a program for monitoring PC operation (AIDA64 is the simplest) and test the load on the video card and processor;
- combine data and look at the big picture.
It is noteworthy that when you start the task manager (TD), hidden miners stop working and the computer’s performance indicators become the same.
Therefore, the remote control will not show the operation of a third-party program in any way.
There is also software that can independently deactivate the task manager after some time (about 5 minutes). If you walk away from your PC, leaving the remote control, and it turns off on its own, there is a possibility that a botnet is running on your computer.
go
How to remove malware from your browser?
There is a certain type of mining software called web-miner. Such programs work through a specific website: you can get rid of this problem by resetting your browser settings, during which the browser cache will be cleared. It is also recommended to install one of the available ad blockers like AdBlock Plus.
In order to remove the miner in the browser, you need to reset Google Chrome settings. To carry out this action you will need to follow the instructions:
- Tap on the three dots icon in the upper right corner of Chrome.
- Select the “Settings” section in the drop-down menu.
- Scroll down to More: Click this hyperlink.
- Go down again and tap on the “Restore default settings” option.
- Initialize “Reset settings” and confirm your action.
- Wait for the running process to complete and reboot the computer.
- After turning on the PC, go to Chrome and download AdBlock Plus or Adguard. To download one or another extension for neutralizing mining software, you need to call up the browser menu and go to “Additional tools”, in the “Extensions” subsection.
- Click on the three-bar icon in the upper left corner of the browser and follow the hyperlink “Open the Chrome Web Store.”
- In the tab that opens, in the search bar, which is located in the upper left corner of the display, enter the request “AdBlock Plus”, then tap “Enter”.
- Click on the blue “Install” button located opposite the first search result from the source “adblockplus”.
- An icon in the form of a “STOP” sign with the inscription “ABP” will appear to the right of the Google Chrome address bar. Click on it with the left mouse button and set the switch located opposite the “Block ads” option to the “On” position.
To perform a similar manipulation in Opera:
- Launch the browser.
- Tap on the Opera logo in the upper left corner of the monitor: select the “Settings” function.
- Scroll to the bottom of the display and click on the “Advanced” link.
- Click on “Restore default settings”. In the “Reset browser settings” window, tap on the “Reset” option and wait until the browser data is cleared.
- Click on the cube located at the bottom of Opera's side toolbar.
- Follow the “Add extensions” hyperlink.
- The “Opera addons” tab will open: in the “Search for addons” search line, enter the name of the desired blocker - AdGuard or AdBlock Plus and click on the magnifying glass icon.
- Click on the search result that appears and select the “Add to Opera” function.
- Enable the blocker using a method similar to Google Chrome.
How to check your computer for hidden mining and not damage the operating system
Even a regular antivirus will help you carry out a simple and quick scan: for example, standard Windows Security. But this option is suitable for fighting against not very advanced viruses.
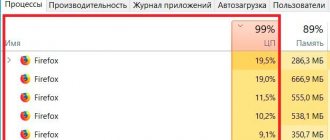
On the other hand, you can notice any miners yourself by simply paying attention to the following indicators in the task manager:
- CPU load;
- video card (graphics processor) load;
- memory load;
- disk space load;
- others.
How to detect a virus
All of the above indicators are conveniently sorted from largest to smallest in the form of a table and allow you to detect malware and get rid of it in the future. Unfamiliar processes (not games or your programs) that are clearly eating up PC resources too much will most likely turn out to be viruses or miners.
Popular miner detection methods
Specialists in service centers use the following effective methods for detecting hidden virus programs:
- monitoring the operation of processes in the Task Manager;
- using diagnostic software for the video card;
- diagnostics of browser operation.
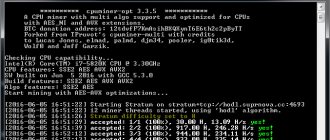
To open the Task Manager, press the key combination ctr+alt+del. In the window that opens, you need to press the more details button to display the information in a more informative way. In the Processes tab you can see all loaded elements. All this is provided to the user in the form of a table, by clicking on the tabs (CPU, Memory, Disk), which can be used to analyze the load on the element. Most miners use a lot of CPU and memory. When you click on these table columns, the malware items will be sorted at the top.
You can also analyze your performance in the Task Manager by clicking on the corresponding tab. The process occurs in real time, which allows the user to obtain reliable information about the current state of the system. In this case, you should also pay attention to the CPU and memory load. Even if the items do not appear in the Processes tab, the load on these items will be high.
If the hidden miner turns out to be complex and does not show itself in the Task Manager, you need to diagnose the load on the video card, processor and memory. This is done using specialized software. These are the following programs:
- AIDA64;
- AnVir Task Manager;
- Process Explorer.
These are just examples of specialized software for Windows. There are many more diagnostic programs. Each with its own characteristics, advantages and disadvantages. Using such tools, you can identify relationships and highlight system files that load the system. Most likely, these will be elements of a hidden miner in Windows 10, which should be removed.
Why is a hidden miner dangerous?
The miner forces your PC to operate at the maximum level of performance, which means that even when performing simple office tasks, the computer can be quite slow. Long-term work at the limit of its capabilities will sooner or later affect the hardware.
First of all, the video card, processor, RAM and even the cooling system may suffer, which simply cannot cope with daily stress tests.
The first sign of the presence of a miner is slowdown on simple tasks and a non-stop cooler.
Also, miners may well gain access to your personal data stored on your computer. Here, everything can be used: from simple photographs to data from various accounts and electronic wallets. And this is already very dangerous.
How to find and remove a miner virus on your computer
In most cases, you can find out about the presence of a miner on your computer by opening the task manager.
To detect a miner on a PC or laptop, you need to use one of the following methods:
- test the operation of the device under normal load conditions (try opening tabs in the browser or basic programs);
- run a game that increases the load on the processor and video card, then analyze the indicators;
- run AIDA64 to check the PC load before closing background programs and after
- conduct a comparative analysis of the information received.
Some viruses disable the Task Manager a few minutes after it starts working, while others disable themselves when the user enters it. If some time after launching the “Dispatcher” the window does not appear, this is a reason to think about it.
There are quite effective programs for monitoring the state of a PC that can detect a miner virus. One of the most popular is AnVirTask Manager.
Preparing to remove the miner
It is better to use software to find hidden miners.
You need to back up the information on your computer and save it to hardware media. It is not necessary that data will be lost during the removal of the virus miner, but it is better to be on the safe side. You should not duplicate absolutely all files, because then the virus will get onto the media. It makes sense to use auxiliary software like Spy Hanter and Cleaner, which will increase the chances of completely removing the bot.
Since miner viruses are Trojans, they can have a negative impact on the operating system. Sometimes after removing them, the computer starts to work incorrectly. Taking this into account, it is better to stock up on a disk with the OS installation file.
Before starting the search, you should close all background programs. Since hidden coin miners are often disguised as different software, disabling it will simplify the task of identifying viruses.
Removing the miner virus
Use an antivirus program to remove virus miners from your hard drive.
When deep cleaning your PC, an antivirus program may detect a virus, but it is unlikely to be able to remove it. Usually this has to be done manually.
Practice shows that most often malware can be picked up on torrent trackers when downloading unlicensed games, movies or other files. If the moment of downloading coincides with the onset of strange behavior on the computer, you can try to find the virus manually. In this case, you must first get rid of the suspicious program and only then proceed to uninstall Stealth mining.
If you're lucky and the virus turns out to be relatively simple, it won't be difficult to remove. To do this, you need to open the “Task Manager” using the key combination Ctrl + Alt + Del). If in the list that opens there is a task that uses the power of the processor or video card by 20% or more, this is probably a miner virus. It should be deleted after agreeing to the loss of unsaved data.
Unfortunately, you cannot get rid of most modern virus bots in this simple way. If the attempt does not bring results, you should move on to another option:
- check your PC for malware, and if it is detected, reboot;
- go to the BIOS menu to control bypassing the operating system: immediately when you turn on the computer, press F2 or Delete (depending on the firmware, but you can press both buttons at once), and then go to the Advanced Boot Options tab;
- select Safe Mode from the long list;
- launch the browser and log into the network;
- download an anti-spyware program that will help you get rid of the miner virus forever.
It is better to protect yourself from miners than to remove them from an infected computer.
To do this you need to use an antivirus. In Windows 10, there is no way to enter the Advanced Boot Options menu during a reboot, so the procedure is as follows:
- press the Win + R combination and enter msconfig$ in the window that appears
- select the “System Configuration” tab;
- In the “Boot” tab, select the required Safe Mode and restart the PC.
Next we proceed according to the above scheme. Anti-spyware programs, as a rule, remove Trojans automatically, and as a bonus, they correct browser settings and remove unnecessary entries from the OS. The Anti-Malware and Malwarebytes sites can be helpful when removing spyware.
Many of those who have encountered this problem recommend the Curelt program. Judging by the reviews, it effectively copes with any malware.
Task Manager
Using this program allows you not only to check whether there is malware for the production of cryptocurrency, but this software can also help you remove the mining script. Before operating in the registry, do not forget to create an OS restore point:
- We launch the dispatcher using the method discussed above;
- Now we just have to go to the “Details” menu;
- All we have to do is review each task. The virus you are looking for will most likely be different from others (it may have an incomprehensible appearance, similar to an incoherent set of elements);
- Also, we would like to find the element that triggers this pest from step 3;
- Now we need to enter the registry. To do this, press the Win+R keys and enter the word in the line that appears regedit and click OK;
- Our registry is opening. Now we need to click on the “Edit” tab and select the “Find” command from the drop-down menu;
- In the search bar that opens, we just need to enter the name of the element that we suspect of being involved in mining;
- So, we found a suspicious file (as you can see, it has a very strange name). Now all we have to do is right-click on it and select the “Delete” tab from the drop-down menu;
- The system warns us about the possible consequences of deletion. But, since we created a restore point, we click “Yes”.
It is advisable to remove other matches using a similar method. Otherwise, this pest will continue to function.
Legality of hidden mining
Mining in general, and especially its niche branches, is still an unexplored area that does not have a clear definition in the legal field. However, this does not mean that if there is no article for hidden mining, then responsibility for it will not follow. Installing software on other people's computers secretly from their owners, infiltrating networks - all this is enough to initiate a criminal case. It doesn’t matter at all for what purpose this happened. It’s better not to break the law and earn cryptocurrency honestly. In addition, stealth mining will not bring significant income and you will not earn as much as you can earn with more honest transactions with digital currency.
In conclusion, we can say that the emergence of new cyber threats associated with cryptocurrency is a very expected result of the popularization of this technology. However, the field of information security also does not stand still, and users can easily protect themselves from malicious software and scan their computer to detect infection in the early stages. It should also be noted that the constantly improving security algorithms in web browsers are already capable of blocking hidden mining and preventing malicious software from being downloaded.
#mining #guide
Why is a miner dangerous?
Miner is dangerous for your computer and can cause serious damage:
- Reduces the service life of components. During mining, the computer operates at maximum power for a long time. This shortens the life of the processor, video card, RAM, and cooling system.
- Limits performance. Miner takes away the main power from the infected computer. Only a small part of the productivity is left to solve the user's problems.
- Provides access to personal data . Since the miner is a Trojan virus, it can detect the user’s personal information and transfer it to attackers. As a result, fraudsters gain access not only to equipment capacity, but also to confidential information.
The actions of the malicious program are controlled by a special service, so they are invisible to the user. The same service controls the inclusion of system activity scanners in order to immediately remove the malicious object from the list of running processes when the scan begins. The most dangerous viruses can disable monitoring programs.
How does a miner manage to hide?
Typically, a separate service is responsible for the operation of the miner on your PC, which allows you to hide and disguise the threat. It is this satellite that controls the autorun and behavior of the virus, making it invisible to you.
For example, this service can pause the work of the miner when launching some heavy shooters. This allows you to free up computer resources and give them to the game so that the user does not experience slowdowns or drops in frame rate. Once the shooter is closed, the virus will start working again.
The same maintenance service is able to track the launch of system activity monitoring programs in order to quickly disable the miner by unloading it from the list of running processes. However, especially dangerous viruses may even try to disable scanning tools on your computer, eliminating detection.
Radical method
If none of the above tips helped remove the miner virus from your computer, you will have to reinstall Windows. But before that, you can try to use the recovery option (if the user managed to save a copy of the operating system before being infected with virus software). Before using the system recovery tool, it is recommended to move all important information saved since the last restore point was created to a safe place (for example, to a flash drive or to a cloud service). After backing up the necessary data, you can begin to roll back the system to the desired state.
In this case, you will need to follow the instructions below:
- Click on the magnifying glass icon built into the taskbar: enter the “Recovery” key in the search bar and tap “Enter”.
- Go to “Settings...” and click on the interactive button “Restore...”.
- Click on “Next>” and specify the path to the current version of recovery point.
- To check the list of changes that will be made to the PC after using the Windows rollback file, just click on the interactive button “Search for affected programs”.
- After the user analyzes the amount of work to be done, just click on the “Next>” button and follow the prompts of the PC “Recovery Wizard”.
- Upon system rollback, you will need to restart your PC: all miners will be deleted from the computer, incl. svchost.
How to deal with miners
In the browser
- Go to a site that will check if your browser is secure. The test is free, but the results are not always correct.
- Green inscription YOU'RE PROTECTED - your browser is protected.
- Red inscription YOU'RE NOT PROTECTED - your browser is vulnerable.
- Download browsers with built-in mining protection. Opera and Yandex.Browser support such features.
- Disable JavaScript in your browser. The solution is radical, because many sites require JavaScript to function properly.
- Chrome: “Settings” – “Advanced” – “Content Settings” – “JavaScript” – Move the switch to the “Blocked” position.
- Firefox: “Settings” – “Content” – uncheck “Use JavaScript”.
- Opera: “Settings” – “General settings” – “Advanced” (“Advanced”) – “Content” – uncheck “Enable JavaScript”.
- Anti-Web Miner application. Download from GitHub, install, use.
- Browser extensions. NoCoin, AntiMiner, MineControl, MineBlock, etc.
- AdBlock browser extension. You need to add to the filters:
- ||coin-hive.com^$third-party
- ||jsecoin.com^$third-party
- ||miner.pr0gramm.com^
- ||gus.host/coins.js$script
- ||cnhv.co^.
- Malwarebytes app. The premium version protects against new miners in real time. The free one finds everything you caught earlier and moves it to quarantine.
- On Windows, edit the file C:\Windows\System32\drivers\etc\ On macOS, enter the command sudo nano /etc/hosts/ in the terminal.
At the end of the hosts file you need to add the line 0.0.0.0 coin-hive.com - it will not allow the device to connect to the server on which the most famous mining script is located. You can redirect to 0.0.0.0 and other domains found to be distributing malware:
- 0.0.0
- 0.0.0 cnhv.co
- 0.0.0 gus.host
- 0.0.0
- 0.0.0 jsecoin.com
- 0.0.0
- 0.0.0
- 0.0.0
- 0.0.0
- 0.0.0 mataharirama.xyz
- 0.0.0 minecrunch.co
- 0.0.0 minemytraffic.com
- 0.0.0 miner.pr0gramm.com
- 0.0.0 reasedoper.pw
- 0.0.0
On PC (outside the browser)
- The already mentioned Malwarebytes application.
- Antivirus with a fresh database. For Windows users: the standard Windows Defender most often does not block the popular Coinhive, so it’s worth installing something more reliable.
- It would be a good idea to launch the task manager in Windows or another application to monitor the consumption of computer resources (AIDA64, AnVir Task Manager or analogs). For macOS, go to “Programs” – “Utilities” – “System Monitoring”. If activity increases sharply and remains stable, even if you have Notes and Calculator open, task manager or its equivalent, remove processes that are taking up too many resources. Then you clean everything with antivirus and Malwarebytes.
- TDSSKiller will help kill rootkits that mask traces of a miner in the system.
- AVZ utility. Download, update the database, click “Explore system”. You get avz_sysinfo.htm. You can post it on the Kaspersky Lab forum and ask for help. If you are successful, they will help you create a script that will disarm the miner. But before that, it is recommended to do everything we wrote about above.
On a smartphone
- First of all, do not download applications that promise crazy thousands of money from mining on a smartphone. And other suspicious applications. Especially from leftist sites. Battery replacement / specialist services cost more than you can mine.
- To combat browser mining, use browser extensions or browsers with anti-mining protection.
- Install a reliable antivirus and update the database regularly.
- Monitor the loading of smartphone resources.
- iOS: “Settings” – “Battery”.
- Android: “Settings” – “Battery” / “Battery”.
If you see processes and applications that are consuming more than they should, feel free to delete them.
Browser mining protection
The key signs of browser mining are a slow computer on some sites, high processor load when viewing certain sites. The following methods are used for protection:
- Blocking malicious sites used for hidden mining in the hosts service file.
- Using anti-mining programs that also remove mining viruses.
- Disabling support for running JavaScript scripts in the browser by deactivating the corresponding item in its settings. This avoids infection but limits your browsing experience on sites that use this technology to display content.
- Using special browser add-ons and add-ons. This allows you not to give up browsing the Internet. The most common add-ons and add-ons for protection against mining are NoScript, NoCoin, MinerBlock, Antiminer and others. Modern browsers have built-in support for mining protection, which is activated in the ad blocking settings (No Coin item).
- Using filters in uBlock, AdBlock and similar applications.
As a rule, add-ons that block ads have separate settings that allow you to activate lists that filter browser-based mining, or add your own domain filters that are used for hidden mining.
Yandex and Google have protection and anti-malware measures:
- Yandex protection. Since March 2022, Yandex has launched automatic protection against mining in the Yandex browser for all platforms. To do this, a special algorithm is used to monitor processor load when working on the Internet. Blocking of mining scripts is carried out automatically and does not affect the operation of the site. To view the load of Yandex browser processes, you need to press Shift+Esc and see the processor load. In this window, you can analyze each site, extensions and tabs for CPU load.
- Google protection. In July 2022, Google banned the hosting of mining programs. The Chrome browser from Google allows you to protect yourself from mining in the browser by using add-ons, as well as by activating the “Protect your device from dangerous sites” item and in the additional settings menu “Find and remove malware”. To detect mining while the Chrome browser is open, you also need to press Shift+ESC and analyze which processes consume the most resources.