One of the main topics of this year is undoubtedly cryptocurrency and its mining. “What is cryptocurrency?”, “How to mine Bitcoin?” — the number of these search queries has increased significantly, especially against the backdrop of a significant increase in the cost of the most famous digital currency, Bitcoin, in a very short time. Buying bitcoins and waiting for the rate to rise is risky; mining cryptocurrency is too expensive and often unprofitable. There remains one more way to make a profit, which is too arrogant and vile - to use the resources of Internet users for mining. Of the latter, the so-called browser mining is now widely known.
Subscribe to our Zen
How to remove all viruses on your computer?
Removing a computer virus from a Windows computer
- Step 1: Download and install an antivirus scanner...
- Step 2: Disconnect from the Internet...
- Step 3: Restart your computer in Safe Mode...
- Step 4: Delete all temporary files...
- Step 5: Run a virus scan...
- Step 6: Remove the virus or quarantine it
Interesting materials:
Is it possible to walk at VDNKh? Is it possible to walk with a child up to 40 days? Is it possible to walk with a child at minus 20? Is it possible to walk with a puppy in your arms without vaccinations? Can foreigners enter Ukraine? Is it possible to invest with 1000 rubles? Can earplugs be reused? Can I use cast iron cookware on an induction cooker? Can I use homemade whipping cream? Can I use a flash drive for Xbox 360?
What is the danger of hidden mining?
Such software uses the resources of your hardware to mine cryptocurrencies. I will not delve into the topic of Bitcoin and analogues. Because there is a lot of information about this on the Internet.
Infection can occur in several ways:
- through opening spam messages received by email;
- through the installation of malicious files;
- through the opening of various archives;
- after going to sites infected with miners.
Not so long ago, such phenomena were very rare. The first mentions of hidden mining appeared in early 2010, but these days there are more and more such cases, as evidenced by numerous articles on the Internet.
What is the danger of hidden mining?
- Firstly, the service life of your computer equipment decreases, as the processor and video card are loaded, and the cooling system speed increases. All this leads to rapid wear. The same goes for hard drives. Therefore, your hardware will last less than the period stated by the manufacturer;
- Secondly, it limits the performance of your system. You cannot work with the applications that you need because the resources are maximally consumed by the miner;
- In addition, hidden “extortionists” can gain access to your personal information, and this is no longer a joke, since passwords to various sites and bank details can be stored on the computer. Attackers can not only overload your PC, but also steal valuable data, thus causing double damage.
What are miner viruses and what threats do they pose?
In 2022, there was a real boom in cryptocurrencies in Russia. The increased rate of Bitcoin and its analogues attracted the attention of scammers and hackers to the topic, who began to mine virtual coins in a dishonest way: mining viruses appeared on the Internet, turning infected computers into a network of mining farms. One by one, the result is a giant mining farm with enormous productivity, bringing in tens of thousands of dollars monthly.
The deception scheme is simple and reliable: hackers launch viruses onto the Internet that spread through email attachments or sites that source downloaded content. Virtual “black miners” take over the power of the infected computer: virtual coins are poured into the hackers, and electricity bills are poured into the victim.
Fortunately, miner viruses do not corrupt files on your computer or steal data. Their task is to use the computing power of the system for their needs. But this is still bad, especially if the network of an entire enterprise is infected.
Signs of a miner virus
High computer load
Modern computers are very good at managing power and preventing all of their processing power from being wasted. This is especially true for laptops: while viewing websites, videos, or idle, their fans are barely audible.
Remember how noisy the cooling system is under heavy load like gaming? If the computer begins to constantly hum and heat up, the system slows down terribly and freezes, which means that someone is absorbing its resources. And most likely, this is a miner virus.
Loading during periods of inactivity
There are variants of miners that turn on only when the user is inactive. Let's say you left the computer on, but walked away from it. After a few minutes, the fans begin to howl, and the miner gets down to its dirty work and stops working as soon as you pick up the mouse again. This method of parasitic existence allows the virus to remain undetected for a long time.
How to find a web miner
If you feel that attackers are mining through your favorite browser, you must first identify the malicious application. In the main menu of Chrome, select “More tools”, then “Task Manager” (you can also use the short key combination “Shift + Esc”).
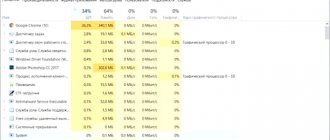
If the website opened in the browser has a built-in miner, we will see something like this picture of the processor load:
Chrome Task Manager shows the following information:
- Currently running processes;
- What tabs are currently open in Chrome;
- Active plugins;
- Current memory consumption;
- CPU load.
If in the Manager you see approximately the same picture as in our screenshot, select the tab with the web miner with your mouse and click “End process”.
Standard "Task Manager"
It is worth noting that there is also such a thing as Internet mining. That is, in this case, you do not download applications, but are at risk by browsing sites on which malicious scripts are installed. There are a lot of such resources on the Internet. Basically, these are pages with an audience of thousands (torrents, pirated online cinemas). While visiting such pages, your PC may be heavily loaded.
To block, I advise you to use the Google Chrome extension – No Coin
Therefore, it is worth opening the task manager using the keyboard shortcut Ctrl + Esc + Shift, and immediately pay attention to the browser. If you have several tabs open, but the load on the processor, RAM, and disk reaches 80-100%, then try closing all sites and see how this affects the load. If the situation immediately changes for the better, it means that the problem was a malicious resource that contains a mining script.
I talked about this phenomenon and methods of combating it in a video on the IT Technician channel:
If the browser is not running, but the load is still high, open the task manager and watch for processes that behave unusually (consume a lot of resources). At the same time, try not to do anything (move the cursor, open/close windows, etc.). Perhaps these are system tasks, for example, updating Windows, which will cease to be active in 5-10 minutes. But if you don’t know the name of the process, first I advise you to use the Google or Yandex search engine to find out more. It is likely that you are dealing with a hidden miner.
Another important point: some miner viruses are able to affect the task manager, closing it 30 seconds or one minute after launch, or even blocking its opening. If this happens, then there is a 99.9 percent chance that you are being mined.
- In such situations, I advise you to go to the “Details” tab, find the required element in the first column and write down its name, view the description;
- Then go to the registry editor by calling the “Run” console (using the Win+R key combination) and entering the command:
regedit
- In the window that opens, go to the main menu “Edit” and click on the “Find...” item. Enter the desired name of the malicious element into the form:
- When the results are displayed on the right side of the editor, you should delete them one by one. But you should do this only if you are 100% confident in your actions. Otherwise, I recommend seeking help from specialists who know their business:
How to protect yourself from browser mining
So, we come to the main question. If you often play browser games, watch movies and TV series online, spend a long time on large resources and at the same time notice how your computer begins to slow down, it is likely that it is currently mining cryptocurrency for someone. There are several ways to protect yourself from this.
By disabling JavaScript
The easiest way is to disable JavaScript on sites in your browser settings. On the other hand, this method may cause problems in running scripts on pages, and some sites may not open at all.
Using browser extensions
It is much more convenient to use extensions that can selectively block scripts, for example NoScript (Firefox), ScriptBlock or ScriptSafe (Chrome).
You can also combat mining scripts using ad blockers. The popular extensions AdBlock Plus and UBlock have already added servers accessed by hidden miners to the list of filters. If the script nevertheless changed the domain and stopped blocking, you will have to make the appropriate changes manually.
Special extensions for browsers have also appeared - anti-miners. Among them are NoCoin, Antiminer and MinerBlock. All of them perfectly block the already well-known Coinhive miner. The developers promise to quickly update the list of prohibited scripts that use computer resources to mine cryptocurrency.
By editing the hosts
Another effective way to protect yourself from a hidden miner is to add its domain to the hosts file so that it is redirected to localhost. For example, to block
Coinhive on Windows OS, open the hosts file in notepad, which is located at: Windows\System32\drivers\etc
.
Add the line 0.0.0.0 coin-hive.com
and save the changes.
On Linux, this file can be opened by typing the command in the terminal: sudo nano /etc/hosts
, on Mac OS X -
sudo nano /private/etc/hosts
. You need to do the same with other miners, only if you know their domains.
Using the Anti-WebMiner utility
In principle, the small Anti-WebMiner utility can do the same job of editing the hosts file for you. This is a program for Windows OS that blocks various web mining scenarios. It redirects the domains that the scripts access. At the same time, the utility allows you to delete entries that were made by it, thus returning the hosts file to its original state. Anti-WebMiner is suitable for those users who do not know what hosts are and what they are needed for.
Hacker ways to infect a virus
Options for downloading malware onto an unsuspecting user's computer include:
- Injection of malicious code through a malicious website that disguises itself as a useful resource or a platform for downloading popular programs. In this case, there is a risk of infection through a script. The user doesn't even need to download anything.
- Using social networks or file sharing services, where, for one reason or another, downloading of various infected files is encouraged.
A little theory
It would be wrong to say that such a phenomenon has only appeared now. Back in 2011, Symantec announced that mining could be launched in a botnet, and Kaspersky Lab discovered malware that connected infected computers to a mining pool. These were special Trojans that literally destroyed even powerful computers. Over the next few years, this problem was returned to more than once. The most famous case is that in March 2015, the developers of the famous torrent client μTorrent built into the program (version 3.4.2 build 28913) a hidden EpicScale module, which used computer resources for calculations during idle time. After widespread user outrage, the developers had to remove it from the installation file.
A completely logical question arises: why didn’t anyone think of doing hidden mining in a browser before? After all, this method does not require special equipment, and the audience of many sites exceeds tens of millions of visitors. It turned out that everything is very simple. A few years ago, the extraction of digital currency was a specific activity; mainly only bitcoins were mined, which required, and still requires, the presence of ASIC processors and certain video cards. With the popularization of mining, new cryptocurrencies began to appear, for example, Feathercoin, Litecoin and Monero, the mining of which, thanks to special hashing algorithms, does not require such power.
What's causing all the fuss
Browser mining emerged amid a massive craze for cryptocurrencies and their mining. Some see this as an alternative to advertising on websites, while others see it as a cunning way of making money at the expense of visitors to web resources. But both of them are not yet ready to play by the rules. The process of mining in the browser can be characterized by the proverb “both the wolves are fed and the sheep are safe.” If earlier for such purposes hackers used Trojans that infected the computer, now it is enough to add a special code to the website page and while the user is on this page, his computer mines cryptocurrency. Moreover, it doesn’t matter where this code is written, you can even insert it into an advertising banner. All that is required from the “victim” is a browser with JavaScript enabled.
A loud scandal that outraged the entire Internet community was the recent case of the largest torrent resource The Pirate Bay using a hidden miner on its web pages. After the exposure, the site's owners admitted that they simply wanted to experiment with mining as a new monetization method. In the code of some pages of The Pirate Bay, users found lines with the Coinhive script, which generates the Monero cryptocurrency.
By the way, on the Coinhive website they openly offer their services for embedding a JavaScript miner into web pages - anyone can do this. At the same time, the developers themselves position their miner as an alternative to advertising and oppose its hidden embedding without warning users. Last month, the authors of the Coinhive miner reported a record simultaneous connection of more than 2.2 million users in the first week of its existence. The total power was 13.5 megahashes per second, which is approximately 5% of the entire Monero network.
The new trend began to quickly gain momentum, and information has already appeared on the network about the first extension for the Chrome browser with hidden code, which forced users’ computers to mine the Monero cryptocurrency. The SafeBrowse extension used the same Coinhive script.
Experts from the antivirus company ESET identify miners hidden in the page code as malware and classify them as malvertising (malicious advertising). They conducted a study in which they found that sites with such scripts are mainly located in Russia, Ukraine and Belarus.
In truth, Coinhive is far from the only service of its kind. There are other sites that sell ready-made scripts for mining in the browser. This suggests that such services are in demand.