Cryptosystems have become especially popular over the past few years. And the more users are interested in something, the more options there are for fraud.
There is a “black money” scheme called “hidden mining”. It began to be used in 2011, but then these were isolated cases, but now it is a serious problem.
To protect your equipment, you need to understand what hidden mining on a computer is, how to find such a program, how to understand that there is a miner on your computer, how to remove a miner from your computer and prevent attempts to create miner viruses. We will also provide you with examples of programs for removing mining viruses.
What is a miner and how does it work?
A miner is a virus program that uses PC resources to produce (mine) cryptocurrency. Infection occurs through:
- messages;
- downloaded files;
- spam mailing.
The malware is automatically installed on the computer without the user's knowledge.
Most often, viruses are contained in files that are downloaded from unverified sources. They can masquerade as books or music content. Plus, many viruses are contained in spam messages that come, for example, by email.
A person may accidentally open such a message and click on the link, as a result of which the miner will penetrate the computer, or a utility will be downloaded to automatically download it from the Internet.
If this happens, your PC will become a link in a large chain whose power is used by the botnet owner to mine cryptocurrency. Several thousand computers united in a single network will cope with the task more efficiently than one, and all electricity costs will be borne by unsuspecting victims of fraud.
The situation is complicated by the fact that a person can voluntarily and knowingly install a miner program on his computer in order to mine cryptocurrency. In this case, it will be very difficult to distinguish a legitimate program from a malicious one. The only difference between them is that one was installed illegally, secretly, and its work is hidden in every possible way.
They first started talking about hidden mining in 2011, but then few people were involved in it. At the beginning of 2022, the problem of viruses that facilitate the illegal production of cryptocurrency became one of the leading ones. It is complicated by the fact that many people do not know about the existence of such malicious programs and how to recognize a miner on a computer.
Who was affected by the mining virus?
The Crackonosh virus, according to reports from Avast Threat Labs, infected just over 220 thousand computers and brought cybercriminals at least $2 million. The statistics are approximate and do not reflect the entire situation in the world, because the studies carried out only concern PCs protected by Avast (Free Antivirus and Premium Security) and do not affect systems with third-party antiviruses.
The virus is found mainly in North and South America (USA, Brazil, Mexico are leaders in the number of infected computers), Europe (Poland, Italy), Great Britain, the Philippines and India . Crackonosh the Russian Federation - statistics say only 500-1000 PCs are susceptible to hidden mining.
Why is a miner dangerous?
The Trojan miner virus causes irreparable harm to the computer. It is dangerous because:
1. Reduces the service life of components.
When mining, the PC operates in maximum mode for a long time. This shortens the service life:
- processor;
- video cards;
- RAM;
- cooling systems.
2. Limits productivity.
A computer infected with a virus transfers most of its power to a malicious program. Only a small part of the productivity is left to solve the user's problems.
3. Provides access to personal data.
Since the miner is a Trojan virus, it can detect the user’s personal information and transfer it to criminals. Theft of passwords from electronic wallets or personal accounts has become commonplace. As a result of the virus, attackers gain not only access to the power of the victim’s computer, but also to confidential information.
As a rule, the actions of a miner on a PC are controlled by a special service that can hide or disguise a malicious object, making it invisible to the user.
For example, the service will stop the virus if a person runs a heavy program or a shooter. Thanks to this, the computer’s power will be freed up and devoted to the game, and the user will not notice a drop in speed. After closing the shooter, the virus will start working again.
The same service controls the activation of system activity scanners in order to immediately remove the malicious object from the list of running processes when the scan begins. The most powerful and dangerous viruses can disable monitoring programs. In this case, no matter how hard the user tries to detect the miner on the computer, it will be difficult to do so.
What is the danger of hidden mining?
Infection can occur in several ways:
- through opening spam messages received by email;
- through the installation of malicious files;
- through the opening of various archives;
- after going to sites infected with miners.
What is the danger of hidden mining:
- The service life of computer equipment that is infected is reduced. There is an extra load on the processor and video card, and the cooling system speed increases. Equipment wears out quickly. The same goes for hard drives.
- The performance of the infected system is limited. You will not be able to work with applications because the resources are consumed by the miner;
- Hidden miners can access and steal your personal information.
How to detect a hidden miner on your computer: preparation for scanning
Before you start scanning your computer, you need to install an antivirus on it, if it doesn’t already exist. The best option is if such a program was initially available on the PC, even if it was just a free version available for public use.
The following products may be helpful:
- Kaspersky Rescue Disk or Live Disk from Dr.Web are emergency boot disks with a built-in anti-virus scanner. The advantage of such devices is that when information is downloaded from them, all existing malware becomes deactivated, making them easy to remove.
- Dr.Web Cureit is a functional program for searching and destroying all viruses on a PC, including miners and Trojans.
- Malwarebytes Anti-Malware has more capabilities than regular antiviruses. When scanning your computer, it can identify threats that other programs cannot.
- Adwcleaner will cope with any infection on your PC.
- CCleaner organizes the work of Windows: it cleans, removes junk and corrects registry entries. You can start scanning your computer only after all utilities have been installed.
Before you think about how to detect a miner on your computer and start the monitoring process, you need to make sure that all situations are excluded in which the system will not show the presence of viruses. To do this, you need to close all running programs. The fewer of them open, the better for scanning.
Why is this happening? Because the miner likes to disguise itself as other programs. If there are no open applications on the PC, then the virus has nowhere to hide. Only Windows Update and antivirus can be left enabled.
Video: How to connect and configure ASIC antminer s9 in 2021!
subscribe
To batch configure multiple devices, follow these steps:
- Launch APMinerTool, click “IP Configuration”.
- On the ASIC, press and hold the “IP report” button for 1 second until the signal light comes on.
- Wait for feedback with IP address information.
- Confirm the IP address you need to configure.
- Follow the same procedure to find the IP address for more devices.
- Select the required IPs and click “Apply Changes”.
How to detect a miner virus on your computer using the task manager
As a rule, it is easy to notice changes in the operation of the PC. Just yesterday everything was fine, but suddenly, for no apparent reason, the equipment begins to heat up and slow down greatly. This PC behavior is a signal that it’s time to run a scan of all systems. Simple viruses are easy to detect and remove, but cunning and well-disguised ones will require some work.
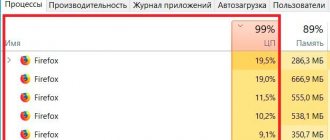
You can find secret miners by regularly monitoring the Task Manager. On Windows, it is opened through the menu or by pressing Ctrl + Alt + Del or Ctrl + Shift + Esc. Close all programs, open the “Task Manager” and, with complete inactivity, when even mouse movements are excluded, observe the processes for 10-15 minutes.
If you notice any activity, then this is a reason to be wary. It is possible that the virus continues to load the computer's power when all other programs are closed. The source of activity can be clarified on the “Details” tab.
There are miners that do not use a central processor, but are hidden in a video card. You cannot see them in the Task Manager in older versions of Windows. How to detect such miners on a computer? Special applications will help, for example, AnVir Task Manager or Process Explorer. Not a single malicious object can hide from them.
There are miners that can stop the Task Manager a few minutes after it starts. This should also alert the user.
In addition to those listed, there are also web miners that connect to a computer through a specific website. If you see excessive browser activity in the Task Manager, you should urgently check your device for hidden threats.
Games with a virus for mining
A little later, experts from the Avast laboratory, after conducting research, immediately identified a list of five computer blockbusters containing a virus and tools for hidden mining:
- NBA 2K19,
- Grand Theft Auto V,
- Far Cry 5,
- The Sims 4
- Fallout 4 GOTY.
We are talking mainly about pirated assemblies (Repack) with unofficial content, published on international torrent trackers with free access and without mandatory registration requirements.
A couple of weeks later, the starting list expanded even more - mention of other projects appeared:
- Pro Evolution Soccer,
- Jurassic World Evolution,
- Euro Truck Simulator 2
- We Happy Few.
Part of the choice of scammers is obvious - many games are demanding on the system - especially video cards and processors - and therefore are downloaded by owners of fairly powerful computers with equipment suitable for mining. Accordingly, laptops and old – by modern standards – PCs are automatically eliminated.
How to detect a miner on a computer and remove it using a special program
When answering the question “how to detect a miner on a computer,” a set of the most popular antiviruses immediately comes to mind. However, unfortunately, everything is not so simple. Modern viruses may not be identified as threats. When monitoring, protection can classify them as potentially dangerous, but nothing more.
If a powerful antivirus is not installed on your computer, then healing utilities are suitable for searching for miners. One of the most popular is Dr.Web CureIt!, you can download it completely free.
You can also do without special software and try to remove the virus manually. In order not to erase anything useful, you need to be sure that it is the miner that was found. If there is no doubt, then you need to open the registry by entering the query “regedit” into the Windows search and then press Ctrl + F to launch an internal search.
In the line that appears, write the name of the program from the “Task Manager” that you think is malicious. All detected objects will have to be deleted using the menu. Then you need to restart the device and check through the Task Manager to see if its performance has improved.
But how to detect a miner on a computer if the virus is skillfully disguised? In such a situation, simple ways to get rid of the problem will be powerless. However, there are at least two solutions to this problem:
- Using Task Manager
Step 1. Open sequentially “Control Panel” - “Management” - “Task Manager” - “Details”.Step 2 . We read the list of tasks, looking for oddities. Typically, a botnet is distinguished from others by its unrelated set of characters.
Step 3 . On the “Actions” page, look for launching the file with the name from Step 2.
Step 4 . The miner can masquerade as a system update. To check, you can write the name of the file in a search engine and see what it launches.
Step 5 . Using a search in the registry, we first find all matches, then delete the files.
Step 6 . Reboot the computer.
- Using AnVir Task Manager program
The multifunctional process manager AnVir will help you detect a hidden virus.Step 1 . Download and install the multifunctional process manager AnVir.
Step 2 . Open the utility and use it to examine all active processes. If any of them seems suspicious, hover your cursor over it to display information about the program.
Remember: some viruses can masquerade as a system application, but they do not fake the details. Next RMB → “Detailed information” → “Performance”.
Step 3 . Select “1 day” and look at the PC performance for this period.
Step 4 . If the system was heavily loaded with some process, then hover the cursor over it and write down its name and path.
Step 5 . Click RMB → “End process”.
Step 6 . We write “regedit” in the Windows search bar and go to the registry.
Step 7 . Next, perform the actions “Edit” → “Find”. We write the name of the suspicious file and delete all matches.
Step 8 . We remove the program itself.
Step 9 . We check the system with an antivirus. If threats are found, they need to be removed.
Step 10 . We reboot the PC.
If at first glance it seems that it is very difficult to detect a miner on your computer, then think about the fact that it steals not only your electricity, but also your personal data. If a person often downloads pirated content or unverified files from the Internet, then he regularly needs to conduct a serious PC scan, otherwise he may be left without savings in his bank account.
Of course, a computer can slow down for objective reasons, but it is considered a sign of a threat if this happens during idle time or when performing simple tasks when the operating system is not even loaded. Listen to the operation of the cooling equipment. It should not make noise when there is no load.
If there are signs of intruders interfering with the operation of your PC, then they need to be dealt with immediately. How you do this is up to you.
Find and remove the virus manually
We open the process manager window and there we find files with unfamiliar names and pay attention to resource consumption:
Run the Run command via Win+R, and write regedit to open the registry editor:
The question of how to find a miner virus in the registry will not arise, since this is done in the same way as a regular search for a piece of text in Word, Excel, or on websites. Combination Ctrl+F, process name, Enter:
We delete all related records using Delete. All you have to do is restart your PC, and the job is complete. We recommend using special applications, since it is not always possible to recognize the miner on your own. Some Trojans can disguise themselves as soon as you press ctrl+alt+del, which is why they simply won’t appear. And special antiviruses know how to find malware, so they will work more efficiently than a human.
How to protect yourself from installing hidden miners in the future
Unfortunately, it is impossible to completely prevent viruses from entering your computer, especially if a person regularly downloads unverified content and visits dubious sites. We cannot ignore the constant war waged between the creators of viruses and the authors of security programs.
But the weakest link is still man. Sometimes, for the sake of wanting to download a movie or book for free, he puts the security of his PC, and with it his personal data, in a dangerous position.
To reduce the risk of viruses, carefully watch what files you download and install on your computer. If your browser warns that a site may contain threats, then you should not visit it.
If the system suddenly starts to slow down, check through the Task Manager to see why this is happening. It is safer to remove dubious programs.
Keep your antivirus updated. Remember that if you are thinking about how to recognize a miner on your computer, then attackers are working in the opposite direction and are constantly improving their malware.
How the Trojan gets in
There are many possibilities for this:
- Visiting sites with hacked software, pirated audio and video, etc.
- Installing .exe files from unverified sources.
- By transferring an infected file or game to a flash drive.
Even an ordinary picture downloaded from the Internet can turn out to be a Trojan that will happily use your power. Everything freezes, it’s impossible to work, and then the question arises - how to find mining on a computer.
There is another type of online miner that starts when you visit the site. When you browse forums and pages on the Internet, you may find that the browser and the entire OS have slowed down. In the task manager, details and confirmation of this can be found in the tab with system loading - it will be almost 100%.