GitHub:
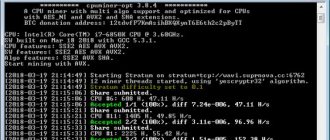
cpuminer-opt is a fork of cpuminer-multi from TPruvot with optimizations imported from other miners developed by Lucas Jones, djm34, Wolf0, pooler, Jeff Garzik, ig0tik3d, elmad, palmd and Optiminer, with additional optimizations by JD.
NoDevFee: cpuminer-opt has no fees, but donations are accepted.
- BTC: 12tdvfF7KmAsihBXQXynT6E6th2c2pByTT
All code is considered open and free. If anyone has a complaint about any of these, please post your case on the cpuminer-opt Bitcoin Talk forum or via email.
cpuminer-opt
Windows source code and binaries are available for download from the links below:
Source code
New in v3.13.0.1
- Issue #262: Fixed xevan AVX2 invalid shares.
New in v3.13.0
- Updated Windows binaries compiled with GCC 9. Included DLLs also updated.
- Icelake build (cpuminer-avx512-sha-vaes.exe) now included in Windows binaries package.
- No source code changes.
Please note that miners are often flagged as malware by antivirus programs. This is not true, they are flagged simply because they are cryptocurrency miners. The source code is open to everyone. If you don't trust the software, don't use it.
Requirements
- A x86_64 architecture CPU with a minimum of SSE2 support. This includes Intel Core2 and newer and AMD equivalents. Further optimizations are available on some algorithms for CPUs with AES, AVX, AVX2, SHA, AVX512 and VAES.
Older CPUs are supported by cpuminer-multi by TPruvot but at reduced performance.
ARM and Aarch64 CPUs are not supported.
- 64 bit Linux or Windows OS. Ubuntu and Fedora based distributions, including Mint and Centos, are known to work and have all dependencies in their repositories. Others may work but may require more effort. Older versions such as Centos 6 don't work due to missing features. 64 bit Windows OS is supported with mingw_w64 and msys or pre-built binaries.
MacOS, OSx and Android are not supported.
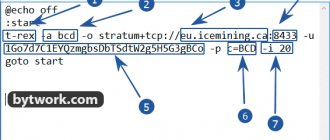
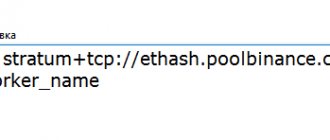
- Stratum pool supporting stratum+tcp:// or stratum+ssl:// protocols or RPC getwork using https:// or https://. GBT is YMMV.
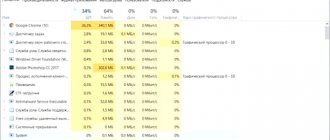
Is it worth removing such viruses?
Naturally, you can use the computer with annoying banners, this is not critical. However, the virus can open the way for other viruses from the manufacturer. Moreover, the viruses themselves are updated and improved. Thus, the malicious program not only displays ads, but can also easily store confidential data: credit cards, social networks, email passwords and other information that you type on a computer with a virus. This is certainly much more serious than browser ads.
Supported Algorithms
allium Garlicoin anime Animecoin argon2 Argon2 coin (AR2) argon2d250 argon2d-crds, Credits (CRDS) argon2d500 argon2d-dyn, Dynamic (DYN) argon2d4096 argon2d-uis, Unitus, (UIS) axiom Shabal-256 MemoHash blake Blake-256 (SFR) blake2b Blake2b 256 blake2s Blake-2 S blakecoin blake256r8 bmw BMW 256 bmw512 BMW 512 c11 Chaincoin decred deep Deepcoin (DCN) dmd-gr Diamond-Groestl groestl Groestl coin hex x16r-hex hmq1725 Espers hodl Hodlcoin jha Jackpotcoin kecca k Maxcoin keccakc Creative coin lbry LBC , LBRY Credits luffa Luffa lyra2h Hppcoin lyra2re lyra2 lyra2rev2 lyra2v2 lyra2rev3 lyrav2v3, Vertcoin lyra2z lyra2z330 Lyra2 330 rows, Zoin (ZOI) m7m Magi (XMG) myr-gr Myriad-Groestl neoscrypt NeoScrypt(128 , 2, 1) nist5 Nist5 pentablake Pentablake phi1612 phi phi2 Luxcoin (LUX) phi2-lux identical to phi2 pluck Pluck:128 (Supcoin) polytimos Ninja power2b MicroBitcoin (MBC) quark Quark qubit Qubit scrypt scrypt(1024, 1, 1) (default) scrypt:N scrypt(N, 1 , 1) sha256d Double SHA-256 sha256q Quad SHA-256, Pyrite (PYE) sha256t Triple SHA-256, Onecoin (OC) sha3d Double keccak256 (BSHA3) shavite3 Shavite3 skein Skein+Sha (Skeincoin) skein2 Double Skein (Woodcoin) skunk Signatum (SIGT) sonoa Sono timetravel Machinecoin (MAC) timetravel10 Bitcore tribus Denarius (DNR) vanilla blake256r8vnl (VCash) veltor (VLT) whirlpool whirlpoolx x11 Dash x11evo Revolvercoin x11gost sib (SibCoin) x12 Galaxie Cash (GCH) x13 X13 x13bc d bcd x13sm3 hsr (Hshare) x14 X14 x15 X15 x16r x16rv2 Ravencoin (RVN) x16rt Gincoin (GIN) x16rt-veil Veil (VEIL) x16s Pigeoncoin (PGN) x17 x21s x22i x25x xevan Bitsend (BSD) yescrypt Globalboost-Y (BSTY) yescryptr8 BitZeny (ZNY ) yescryptr8g Koto (KOTO) yescryptr16 Eli yescryptr32 WAVI yespower Cryply yespowerr16 Yenten (YTN) yespower-b2b generic yespower + blake2b zr5 Ziftr
Many variations of scrypt based algos can be mine by specifying their parameters:
scryptn2: —algo scrypt —param-n 1048576 cpupower: —algo yespower —param-key “CPUpower: The number of CPU working or available for proof-of-work mining” power2b: —algo yespower-b2b —param-n 2048 — param-r 32 —param-key “Now I am become Death, the destroyer of worlds” sugarchain: —algo yespower —param-n 2048 -param-r 32 —param-key “Satoshi Nakamoto 31/Oct/2008 Proof-of -work is essentially one-CPU-one-vote" yespoweriots: -algo yespower -param-n 2048 -param-key "Iots is committed to the development of IOT" yespowerlitb: -algo yespower -param-n 2048 -param-r 32 —param-key “LITBpower: The number of LITB working or available for proof-of-work mini” yespoweric: —algo yespower —param-n 2048 —param-r 32 —param-key “IsotopeC” yespowerurx: —algo yespower —param-n 2048 —param-r 32 —param-key “UraniumX” yespowerltncg: —algo yespower —param-n 2048 —param-r 32 —param-key “LTNCGYES”
Step-by-step instructions for manually removing CPU Miner
We repeat that you carry out this operation at your own peril and risk. Each PC has its own operating system with many differences. Of course, the main registry keys, files, folders are the same, but if, for example, your computer has some program in which the registry key contains the word CPU Miner (a fairly common case), and this program uses certain system services - in most cases after removing them, your system will no longer start because the system registry has become corrupted.
Step 1. Make a restore point.
Be sure to create a restore point. You will not be able to restore the system if a restore point is not created.
- Right-click on “Computer”, then select “Properties”.
- The “System Protection” button, then the last button at the bottom right “Create”.
- enter a name for the recovery point, and then click “Create”.
Step 2. Remove the program from the PC.
- You need to log into “My Computer”, then click on “Delete or change a program” (this menu is located at the top).
- We look for “CPU Miner” in the drop-down list and click delete on the right.
Step 3: Remove browser add-ons and extensions.
Each browser has its own button to open a list of extensions.
Google chrome
Go to the menu, then to Settings, then to Extensions (the menu button is at the top right). In extensions, look for CPU Miner and click Delete.
Internet explorer
Go to Tools - Configure add-ons. Find CPU Miner and remove it.
Mozilla Firefox
Go to the menu (top right), click Add-ons, look for CPU Miner and click Delete
Step 4. Clear the system registry from CPU Miner.
- Press win+R, a line will appear, write regedit in it, the registry will open.
- Then we look for malware. Press Ctrl+F, type CPU Miner and press enter.
- The found key will appear - delete it.
- We search further using the F3 key. Thus, we delete everything that the search gave us, then a message will be displayed that nothing could be found.
We reboot the computer. After reboot, if the system failed to boot:
- When the screen is black, press f8 and f9 as quickly as possible to enter safe mode.
- in the menu, select safe mode and after loading it, we restore the system Start - Accessories - System Tools - System Restore - select the previously created restore point and begin restoring the system.
- Sometimes it happens that safe mode does not start. In this case, you need to select line No. 1 in the menu, then restore the system based on the prompts.
When there is only one virus, these actions may be enough. But viruses are often grouped together: they are able to restore one another if one of them survives. For example, by the time this article was written, the CPU Miner virus had a large number of modifications. We recommend getting rid of swetim automatically with the spyhunter 4 program. Thanks to this utility, you will cure your computer of this virus, as well as others that you may not know about. In addition, the CPU Miner virus, penetrating onto a computer, can collect many similar viruses.
Errata
Old algorithms that are no longer used frequently will not have the latest optimizations.
Cryptonight and variants are no longer supported, use another miner.
Neoscrypt crashes on Windows, use legacy version.
AMD CPUs older than Piledriver, including Athlon x2 and Phenom II x4, are not supported by cpuminer-opt due to an incompatible implementation of SSE2 on these CPUs. Some algos may crash the miner with an invalid instruction. Users are recommended to use an unoptimized miner such as cpuminer-multi.
cpuminer-opt does not work mining Decred algo at Nicehash and produces only “invalid extranonce2 size” rejects.
Benchmark testing does not work for x11evo.
How to remove CPU Miner
Cleaning up CPU Miner involves getting rid of all browser add-ons with the name CPU Miner, all registry keys that are associated with this virus, and every virus file on the computer. Typically, removing an add-on in browsers with the name CPU Miner has an effect either before restarting the browser or before rebooting the system. The virus program repairs itself. You can remove all extensions and add-ons in browsers, remove it using the Add or Remove Programs function, find the program on your computer and get rid of them yourself. The work will be useless. However, only experienced computer users with extensive experience can clean the registry. If you make any mistake in the registry, you will need to reinstall the OS or it will be able to work, but errors will appear on an ongoing basis. Because of this, we advise only fairly experienced users to clean the registry themselves; moreover, you clean the registry at your own peril and risk. For this reason, we recommend automatic removal of CPU Miner using a utility called Spyhunter 4, created by Enigma software.
Remove CPU Miner automatically
Why spyhunter?
- Will clear all add-ons and extensions in the browser called CPU Miner.
- Will delete registry keys that are associated with CPU Miner and destroy only them. Your registry will not be damaged, the OS will work normally.
- This utility will clean CPU Miner virus from your computer.
- It will improve the functioning of the computer, it will start working better.
- Removes other malware and viruses from your computer.
- It will protect your computer from future threats.
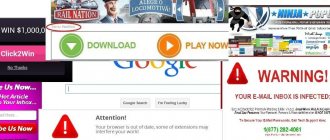
Why are hidden miners dangerous?
The XMRig virus injects itself into trusted processes; security systems and antiviruses will not prevent this from happening. Hidden miners work on websites or directly on a PC. Consuming the user's resources, the attacker converts them into real money using cryptocurrencies. In this case, the load on the components may be excessive, which will lead to rapid failure of the processor, RAM and video card.
Hidden miners can be embedded on websites
If this hidden miner got onto the computer of an inexperienced user, then the only way to get rid of its operation is to reinstall the operating system.
Manual removal
If these manipulations are not enough, you will have to clean the computer manually or reinstall the system. Second phase:
- Erase all the latest programs through a standard Windows service.
- Check the startup menu (msconfig): you are interested in the Services and Startup tab - you need to uncheck all suspicious applications, processes and services.
- Activate self-healing with the command in the sfc /scannow console and wait for completion.
- Go to the registry (regedit). Don't forget to make a copy of the registry just in case.
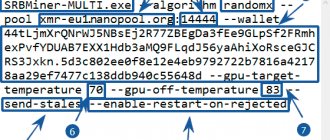
- Calling up the search window (CTRL+F), enter xmrig cpu miner or simply xmrig in it.
- We delete all associated parameters. Reboot the PC.
If this does not help, then you need to restore the system or use a rollback to a successful configuration. If some virus software files are not deleted, then go through Safe Mode. In the same way, you can restore if important system files were erased during deletion. Unfortunately, third-party programs for removing XMRig, such as Unlocker, do not always work, since the malware itself has preventive protection.
Only as a last resort will you need to reinstall Windows. On the other hand, killing Windows may be faster than removing the virus. You decide.