- Which cryptocurrency wallet to choose?
- Where is the best place to create a Bitcoin wallet?
- How to register and use a Bitcoin wallet?
Typically, such questions arise from a person who has just decided to create his first storage facility for digital coins.
Obviously, the choice of a wallet for storing bitcoins must be approached with all responsibility, because cryptocurrency still does not have a legal status, and accordingly, all risks associated with the theft of funds stored in a cryptocurrency wallet fall entirely on the shoulders of its owner.
This post will help you figure out how to create a simple and at the same time reliable Bitcoin wallet.
What Bitcoin wallets are there?
All Bitcoin wallets are conventionally divided into two types: “hot” - requiring a constant connection to the network and “cold” - not requiring such a connection. In addition, cold ones are divided into “thick” and “thin” .
Naturally, the safest are cold wallets, due to the fact that it is physically impossible to steal cryptocurrency from them, due to the lack of an Internet connection.
The following are used as cold ones:
Paper wallets - they are created using special generator sites, such as: WalletGenerator.net, myetherwallet.com, bitaddress.org. These sites are needed in order to generate two keys to the wallet: a private one (you can use it to withdraw and transfer coins) and a public one - a Bitcoin address (used to receive funds). Both keys are then printed and stored in paper form.
Here is an example of a Bitcoin paper wallet.
Software (desktop) wallets are a program that must be downloaded and installed on your computer. Further, with its help, the entire blockchain chain that has existed since the advent of Bitcoin (in case these are thick wallets) is downloaded from the network. Their main disadvantage is that they are very demanding on resources, for example, installing a Bitcoin Core wallet requires up to 200 GB. However, there are also thin “clients”, for example Electrum, when using which only part of the blockchain is loaded, therefore they are not very resource-demanding, but work much faster than their older brothers. In my opinion, such wallets are the best solution for storing your bitcoins and other cryptocurrencies.
Hardware wallets are specially designed devices designed to securely store digital coins. They are distinguished by their small size, usually slightly larger than a flash drive, and high storage reliability. All transactions take place within the wallet architecture and, in addition to the keys, are confirmed by the additional introduction of a PIN code, which allows them to be used even on an unprotected computer. The most popular hardware wallets: Trezor, Keep Key, Cool Wallet, Ledger Nano S, BitFreezer. You can buy them on the website walletz.ru - this is the official reseller of cryptocurrency wallet manufacturers in Russia. Today, prices for the cheapest devices start at 3,500 rubles.
Despite all the advantages of cold wallets, they are not as convenient to use as hot ones. Therefore, they are usually used for storing large amounts, and for daily management of digital assets, so-called hot crypto wallets are more suitable.
These include:
Web wallets (browser wallets) are special services that specialize in working with digital assets, for example, cryptocurrency exchanges, payment systems, exchangers. The most popular online wallets: Xapo, Webmoney (bitcoin wallet WMX), CoinBase.com, Blockchain.info, Exmo.com, Bter.com. You can create a wallet after logging into the selected service, following the instructions.
Mobile wallets are smartphone apps that are very similar to online banking platforms. Some companies, such as Sirin Labs, even produce special blockchain smartphones that will allow you to make transactions and mine virtual currencies. Most people prefer mobile applications for daily use of cryptocurrency.
The original software for most crypto wallets can be downloaded from the popular resource bitcoin.org.
It is enough to indicate the operating system and select any one you like from the list. Brief characteristics located to the right of each wallet in the form of icons will help you make your choice.
Bitcoin pseudo-random number generator vulnerability
Private Bitcoin keys are an integer value from 1 to 115792089237316195423570985008687907852837564279074904382605163141518161494337 or in HEX 1 to 0xffffffffffffffffffffffff fffffebaaedce6af48a03bbfd25e8cd0364141. On the main Bitcoin network there are addresses starting with 1: compressed, uncompressed; addresses with 3: SigScript and backward compatible with SegWit, as well as native SegWit addresses starting with bc1. In addition, there are already about seventy forks that have different prefixes, but the same roots as the main Bitcoin. Bitcoin addresses are calculated by the ECDSA cryptographic signature function ( ) based on an elliptic curve. So, let's consider generating a Bitcoin address from a private key.
Private key d is a number. Public key Q is a point on an elliptic curve equal to dG, where G is the base point of the curve.
- A random number k is selected for the signature, in the range [1, n-1].
- The curve point (x1,y1) = k*G is calculated
- Calculate r = x1 mod N, where N is the order of the curve.
- Calculate s = k-1(H(m)+rd) mod N, where k-1 is the inverse mod N of k.
- H(m) is the hash of the message being signed.
The signature is the pair (r,s).
The “k” variable is random and is obtained in the ECDSA algorithm from standard operating system libraries.
Thus, in the entire function, only this variable can be affected. Which gives two attack vectors:
- embedded vulnerability in a pseudo-random number
- and universal luck in which a random number appears twice
Pseudo-random number generator attack
Nils Schneider was the first to research and publish this problem on January 28, 2013 on his personal page.
But the problem persisted and, moreover, acquired a new scale. A software attack on a PRNG is divided into three types: Direct cryptographic attack based on analysis of the algorithm's output data.
Input-based attacks can be classified into known input attacks, reproducible input attacks, and selected input attacks.
Attacks based on opening the internal state in which the attacker knows the initial or initial state of the generator.
This also includes bookmarks in the software, in which the creator of the algorithm knows any of the hashed pseudo-random numbers and subsequent ones in the chain. Such an algorithm is difficult to determine from the outside, since the numbers appear evenly distributed over the entire range.
Software vulnerabilities also include weak generation of pseudorandom numbers in certain libraries. Such as SSL, OpenSSL, some Java libraries, JavaScript, etc. Detailed materials were repeatedly described in periodicals on hacking and over time became examples in cryptography textbooks.
What is the scale of the threat to Bitcoin?
Having a full Bitcoin node, you can compare and group all transactions in the network.
It is enough to compare the “k” variable in all transactions for each address and find duplicates. The first time we did a reconciliation was at the end of 2016, then the database consisted of more than 210 million addresses, transactions with a total of more than 170 million addresses, and 447 million signatures. Scanning vulnerable addresses in ten threads took a week.
As a result, 1327 vulnerable addresses with the same signatures were found! A list of addresses can be found at the end of the article.
This means that a private key can be calculated for these addresses, which means gaining control over the money.
The largest leak occurred in the summer of 2015. The JavaScript of the Blockchain.info wallet was producing the same value for the “k” variable for several hours. Which led to the theft of about 200 Bitcoins!
If you remove the human factor of software vulnerabilities, the probability of a coincidence is approximately 0.000296868%. Not a lot at all, but I really wouldn’t want to become such a “lucky guy” and lose my money.
How to deal with this?
As we described above, this vulnerability only works when sending payments and generating the same “K” variable in at least two transactions.
Therefore, if you do not create outgoing transactions or reduce their number to a minimum, then there is no threat. This idea has long been implemented in the Bitcoin protocol BIP 32 (Hierarchical Deterministic Wallets, HD wallet). Its idea is that a private key is used from which you can get an endless chain of Bitcoin addresses. A one-time address can be used to accept each individual transaction. In this case, the sum of the HD wallet balance is the sum of all balances in the address chain. And during an outgoing transaction, coins are collected from these addresses, making one outgoing transaction for each Bitcoin address. The change will be sent to a new Bitcoin address from the address chain.
This scheme of work significantly increases the security and anonymity of the wallet.
Links:
[1] ECDSA - Application and Implementation Failures, Markus Schmid, UC SANTA BARBARA, CS 290G, FALL 2015.
[2] Nils Schneider: Recovering Bitcoin private keys using weak signatures from the blockchain, Blog entry, 28 January 2013.
[3] Private Key Recovery Combination Attacks
[4] List of vulnerable addresses and total balance
How to open a Bitcoin wallet - step-by-step instructions
Installing a Bitcoin wallet
As an example for registration, I chose one of the most reliable and easy to use - Electrum .
Step 1. To download the distribution, go to the official website https://electrum.org and click on the “Download” .
Note! The developers of the ELECTRUM wallet, starting from version 3.3.4, advise downloading the software only from their official website!
Step 2. Select a download option from the list, in our case “Windows Installer” .
Step 3. We start the wallet installation process, having first disconnected the computer from the Internet for greater security.
Step 4. Next, select “Automatic connection”
Step 5. Specify the name and select the type of wallet.
Step 6. Select the type of seed phrase; the type of wallet will depend on this. I recommend choosing “Sigwit”, as it has a number of advantages:
- Signature time optimization;
- Reduce commission fees by up to 50%.
Step 7. We write down the generated seed phrase on paper or in another safe place, which will help restore the wallet in case of problems with the computer.
Step 8. Next, you will be asked to confirm the seed phrase to make sure that you wrote it down correctly.
Step 9. Create a password.
Step 10. That's it, the wallet is installed and ready to go!
The English interface is initially installed. To Russify it, you need to click on the tool icon and select Russian in the “General” tab. After which you need to re-authorize.
Is it possible to make money on Bitcoin generators?
Making money on a bitcoin generator
In general, the answer to this question is clear - yes, you can really make money on bitcoin generators. This is confirmed by thousands of users, but they all have one thing in common - only those who have a lot of free time can get cryptocurrency without investments. It will be needed both to study all the subtle points and to test such sites.
The big disadvantage is also that out of 100 sites calling themselves bitcoin generators, 90, if not more, will turn out to be fraudulent. Only market newcomers are in pursuit of free BTC, and after getting acquainted with the false service, they completely discourage themselves from continuing to use cryptocurrency.
You will find useful tips for earning bitcoins in the video below:
Tips for earning bitcoins
How to work with Electrum wallet
Let's look at the basic elements of wallet management:
The History tab displays all wallet transactions.
“Sending” is responsible for sending bitcoins. Not only the recipient's address is indicated here, but also the amount of the transaction fee is indicated.
Using the Receive tab, you can request payment by entering a receiving address with a QR code.
In the “Addresses” tab, all addresses associated with the Bitcoin wallet are stored.
By the way , do not forget to export private keys immediately after installing the wallet. A private key is essentially access to your wallet, like a PIN code from a bank card, and if it falls into the wrong hands, you can lose all the bitcoins stored in it. You can export private keys by going to the tabs: Wallet ⇒ Private keys ⇒ Export.
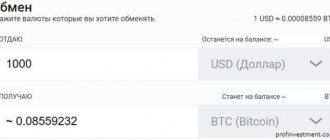
top up the balance of your Electrum Bitcoin wallet using specialized exchanges. You can use them to buy and sell not only bitcoins, but also other cryptocurrencies.
The most popular exchanges include:
- EXMO;
- Binance;
- BiteBox;
- YoBit;
- LocalBitcoins;
- C-Cex.
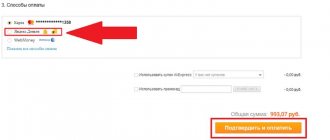
You can also use exchangers, for example: 60sec, Kassa, Xchange, 24PayBank, Ychanger. Working with them is much easier than with exchanges.
To choose the best rate, use BestChange exchanger monitoring; it monitors electronic payment exchange offices and, depending on the chosen direction, provides information about the most favorable exchange rates.
SecretScan GPU AMD for joint search of private keys in a pool on AMD video cards.
Planned for development. Please use the "Rent" section.
If your video cards are not supported, then for now it is better to mine another cryptocurrency with them and exchange it for renting suitable video cards. The rental rate is similar to the mining profitability. Reserve for exchange: 160 video cards.
Renting 8 GTX1060 video cards to search for keys costs 0.6 ETH per month: 30 trillion keys per day, 900 trillion keys per month. Half of this amount is the cost of electricity. All funds from rental or mining go to the creation and development of the project.