A virus miner (miner, Bitcoin miner) is malicious software whose main purpose is mining - earning cryptocurrency using the resources of the victim’s computer. Ideally, such software should operate as secretly as possible, have high survivability and a low probability of detection by antivirus programs. A “high-quality” virus miner is hardly noticeable, almost does not interfere with the user’s work, and is difficult to detect by anti-virus software. The main external manifestation of a virus infection is increased consumption of computer resources and, as a result, additional heating and increased noise from the cooling system fans. In the case of a “low-quality” miner virus, in addition to the listed symptoms, there is a decrease in the overall performance of the computer, short-term freezes or even the inability of some programs.
How does the Bitcoin Miner virus get into your computer?
The Bitcoin Miner virus was invented by people who wanted to make a profit from mining cryptocurrencies without using their own computing power. They developed a program that quietly penetrates the system and connects the user to mining. Accordingly, even if you use only 10-20% of the entire PC performance, the CPU and memory load can be 90% or higher.
For the first time, the Bitcoin Miner virus was noticed by specialists. They discovered a strange Trojan spreading through Skype. Today, the number of ways through which a “mining worm” can get into your computer is enormous. You can load a game, download music, open messages, and at this time attackers are already gaining access to your PC’s computing resources.
What is mining?
The word “mining” comes from the English “mining”, which means “mineral development”. Mining is nothing more than the process of creating new units of cryptocurrency (cryptocoins) using a special algorithm. Today, there are about a thousand varieties of cryptocurrencies, although they all use the algorithms and protocols of the most famous newcomer - Bitcoin
.
The mining process is a solution to complex resource-intensive problems to obtain a unique set of data confirming the authenticity of payment transactions. The speed of finding and the number of cryptocurrency units received as rewards are different in different currency systems, but in any case they require significant computing resources. Mining hardware power is usually measured in megahashes (MHash) and gigahashes (GHash). Since the complexity of mining the most expensive cryptocurrencies has long been unattainable on a single computer, special farms
, which are powerful industrial-level computing systems and
pools
- computer networks in which the mining process is distributed among all network participants. Mining in a common pool is the only way for an ordinary user to participate in receiving at least a small profit from the process of creating crypto coins. Pools offer a variety of profit distribution models, including the power of client equipment. Well, it is quite clear that by driving tens, hundreds and even thousands of computers infected with the miner into a pool, the attackers receive a certain profit from the exploitation of other people’s computer equipment.
Mining viruses are aimed at long-term use of the victim’s computer and, when infected, usually install auxiliary software that restores the main mining program if it is damaged, deleted by an antivirus, or crashes for some reason. Naturally, the main program is configured in such a way that the mining results are tied to the accounts of the attackers in the pool used. The main program uses legal mining software, which is downloaded from official cryptocurrency websites or special pool resources and, in fact, is not malicious software (virus, viral software - software). You can download and install the same software yourself on your own computer, without causing any special suspicion to the antivirus used on your system. And this does not indicate the low quality of anti-virus software, but rather the opposite - the absence of false alarm events, because the whole difference between mining that is useful for the user and mining that is useful for the attacker lies in who will own its results, i.e. from an account in the pool.
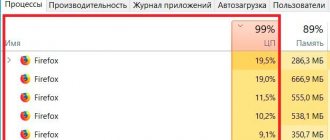
As already mentioned, the main sign of a system being infected by a miner is the intensive use of resources by some program, accompanied by an increase in the noise level of the system unit, as well as the temperature of the components. Moreover, in a multitasking environment, as a rule, the virus works with the lowest priority, using system resources only when the computer is idle. The picture looks like this: the computer is not busy with anything, it is idle, and its temperature of components and the noise emitted by the ventilation are reminiscent of the game mode in some very demanding computer shooter. But, in practice, there have been cases when the priority of mining programs was set to the standard value, which led to a sharp drop in useful performance. The computer began to “slow down” terribly and it was almost impossible to use it.
How to identify Bitcoin Miner virus?
Of course, the primary sign of the presence of a mining virus on your PC is high system load. To make sure you have picked up Bitcoin Miner, there are a few simple steps you need to follow:
- Open the task manager on your PC.
- Using the manager, close all open applications.
Now pay attention to the download that is indicated in the window. If its indicator is 20-40%, then you don’t have to worry. Most likely, you do not have Bitcoin Miner on your PC. If the indicator fluctuates between 80% and above, then you can be sure that the miner is already in the system.
What is a hidden miner and how to detect it on a PC
A hidden miner is not an ordinary virus, but a complex program that uses your computer to mine cryptocurrencies.
Black or hidden mining refers to the extraction of digital currency by third parties through the use of the power of other people's PCs. To do this, virus miners are introduced into computers, and we will now tell you what they are.
Equipment is infected through downloading and installing files, unauthorized remote access, and sometimes through direct injection. Next, the PC is connected to the scammer’s mining farm, and the earned coins are sent to his wallet.
Spyware is installed in silent mode, and crypto mining is disguised as the operation of an OS service or does not show itself at all. The new generation of virus miners have the ability to remain unnoticed: when the load increases, they turn off so as not to slow down the computer and not reveal their presence.
At first glance, such software does not cause any particular harm to either the computer or its owner (with the exception of increased electricity bills). In fact, the presence of a shadow miner harms the operating system, “eats” the power of the PC, affects productivity, and most importantly, it can open access to personal data, including information about payment transactions and e-wallet passwords.
The most common hidden miner is Bitcoin miner, developed as a single tool for mining various cryptocurrencies on other people's computers. It consists of an unlimited number of nodes and loads the equipment at 90-100%. The mining process is accompanied by noticeable noise from the video card cooler. Bitcoin miner is simple in technical terms, cannot disguise itself and can be easily detected in the task manager, but there are also more “cunning” mining viruses:
- Bad Miner;
- Epic Scale
- Miner Gate.
How to remove Bitcoin Miner virus manually?
There is a way to remove the Bitcoin miner manually. To do this, you need to open the task manager and disable the following processes there:
%AppDatabtc.exe
%System%miner.exe
After that, go to the register and delete the following line there:
[HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun] btc = "%AppData%btc.exe"
Lastly, look for the following files in the system and delete them:
%AppDatabtc.exe
%System%miner.exe
After this, it is advisable to check the system again with an antivirus with the latest updates.
Removing a miner using a rollback to a restore point
The easiest way to get rid of unwanted software is to return Windows to a previous state using restore points, often called a system rollback. This requires that there be a restore point created at a point in time when the infection had not yet occurred. To launch the recovery tool, you can use the key combination Win+r and type the command rstrui.exe
in the input field that opens. Or use the main menu – “Programs – Accessories – System Tools – System Restore”. Next, select the desired restore point and roll back to it. With a successful rollback, in most cases, it is possible to get rid of the virus without much effort. If there is no suitable recovery point or the rollback did not neutralize the virus, you will have to look for more complex ways to resolve this problem. In this case, you can use standard operating system tools or specialized programs that allow you to search and terminate processes, obtain information about their properties, view and modify program startup points, check digital signatures of publishers, etc. Such work requires certain user qualifications and skills in using the command line, registry editor and other utility utilities. Using several anti-virus scanners from different manufacturers, programs to clean the system and remove unwanted software may not give a positive result, and in the case of a miner, it usually does not.
How to remove Bitcoin Miner virus?
First of all, you need to go into the Bios of your PC. Login is carried out differently, depending on what motherboard you have. There we find the item Safe Mode with Networking (safe mode). After that, turn on your PC and download the anti-spyware program. There are many options here - today many antivirus developers have already taken into account the trend and began to release products that are capable of detecting mining viruses. One of these is the Reimage program, which you can download on the official website by typing its name into a search engine.
After downloading, launch the program and begin scanning the system. During the process, she herself will be able to identify the virus and offer to remove it.
Now you know several ways to remove the Bitcoin Miner virus, but the best way to get rid of it is to prevent it from occurring. Do not download unverified files, always keep your antivirus updated and periodically conduct a full system scan.
How could I get infected?
Trojan.Bitcoinminer is distributed through dozens of discreet methods and schemes. The parasite usually disguises itself as a useful application, and on shady websites. It is also often included as an additional attachment to useful files of third-party programs. It covers torrents, spam and fake updates. You can also catch the infection by visiting an infected website. As you can see, Trojan.Bitcoinminer is resourceful. However, it wouldn’t be infected on your computer if you were vigilant. Of course, you should stay away from questionable websites. The Internet is a dangerous place. If you don't change your habits, another virus may infect your device. Avoid using torrents. Download software only from reliable sources. When you begin the installation process, pay close attention to the fine print. If you are offered the Advanced installation option, all means, select it. We also have to mention good old spam. Yes, you know how dangerous an attached file can be. However, did you know that spam can contain corrupted links? Hyperlinks can also harm your computer. A malicious link may be downloaded by a virus or redirect you to an infected website. Either way, you will end up with an infection. When you receive a message from an unexpected sender, take the time to check the sender. You can simply go to the dubious email address in a search engine. If it was used for shady business, someone would complain online. If the questionable email was sent from an organization, go to their website and compare the email addresses listed here with the one you received the email from. If the addresses match, you won’t remove the impostor.
Alternative method
All mining software penetrates the computer and receives administrator rights in order to make changes on the specified device on behalf of the admin. You can check the presence of such a “guest” through the “User Account Control” menu. And in order to find and remove hidden miners from your PC, you need to perform the following manipulations:
- Go to the local drive “C”, to the “Windows” folder, to the “system32” folder, to the “drivers” directory and to the final folder called “etc”.
- Run the file named “hosts” in a standard text editor – Notepad.
- The file is hidden, so you may need to display hidden folders through the already familiar “Explorer” (“View”, “Options” option).
- Usually, the hidden miner writes the path to the mining farm in the “hosts” file: to remove the Bitcoin miner virus, you can try to manually clean all suspicious IP addresses (for example, “102.54.94.9 rhino.b-coinggg.com”).
- Since the provider records log files when the user views certain Internet resources, there is a possibility that “malware” will be returned to the PC based on these logs.
- Therefore, when surfing the web, it is recommended to use a VPN program without recording logs.
The best free VPN browser extensions are:
- TunnelBear VPN;
- Hotspot Shield;
- Hola VPN;
- Touch VPN;
- ZenMate VPN.
The most common hidden mining programs
Be careful when installing suspicious software on your PC.
The most common shadow cryptocurrency mining program is Bitcoin-Miner. This virus was developed in order to create a single resource that allows you to mine coins from other people's computers and consists of an unlimited number of devices. With such “joy” entering the system, the computer is loaded to the maximum, which becomes noticeable by the noise of the video card cooler. Fraudsters do not hesitate to squeeze everything possible out of the victim’s device, so it works at 80, and sometimes at 100% power, instead of the usual 20%. However, the activity of such a program is detected through the “Task Manager”, because it reflects any fluctuations in the operation of the computer.
There are other programs created for hidden cryptocurrency mining. For example, BadMiner, MinerGate or EpicScale, which, even when the main materials are deleted, saves files on the system that can restore the program.
How to secure your PC?
To avoid having to remove miners from your computer in the future, just check the links for downloading data from the Internet in one of the available online virus and malware scanners, for example, VirusTotal, 2IP.ru.
To check a particular link in Virus Total, you must perform the following manipulations:
- Copy the link to the site you are checking with media content.
- Go to the “Virus Total” portal and go to the “URL” tab.
- In the “Search or scan a URL” field, paste the copied link, then tap on the icon in the form of a magnifying glass.
- A tab will open with detailed analytics of the resource: the user will be able to make an informed decision about the advisability of downloading data.
To protect your computer from viruses, just follow these simple instructions:
- do not download media content from unverified sources;
- visit only secure sites;
- avoid logs - use reliable VPN services;
- install an antivirus on your PC and use it on an ongoing basis, not forgetting to promptly update the program.
Miner - where does it come from?
Oh, well, everything is simple here too. Let's think - what does a miner need? Powerful hardware, first of all, it is desirable to have a powerful video card. They can use either a CPU or a video card for mining, but it is more efficient to mine on a video card. But how can you ensure that PCs with a powerful video card and processor are infected with a virus? That's right - the virus needs to be on gaming sites.
As a result, we have the following picture:
- You want to play with a cool new toy.
- But of course I have no desire to buy it.
- You go and download it from a torrent.
- The game is already activated, can be with mods and optimized to run faster. In general, this type of game or program is called repack.
- You install it, and often the really necessary components can be installed with it, for example Microsoft Visual C++, DirectX, some patches and additions.
- Along with the necessary components, fraudulent software can easily be installed, as well as viruses, or more precisely, miners. Believe me, this is a very common situation. As a result, then the questions arise: where do the viruses come from on the PC?
This is the most popular and frequent method of getting all kinds of viruses onto a PC. Not all torrent portals implement a security policy, so to speak, files are often not checked, and you understand the consequences.
Why is a miner bot dangerous for a computer?
It would seem that the program mines cryptocurrency for itself through someone else’s device, what’s wrong with that? It's a shame, of course, but not critical. And yet, like any virus software, a hidden miner poses a danger to your PC. First of all, the presence of such a program on a computer inevitably harms the OS. After all, it belongs to the category of Trojans. In addition, this program “eats” the working power of the processor and video card, which affects the productivity of the PC. And, perhaps, the most unpleasant thing: the spy gives the fraudster access to your personal data, including financial information and the ability to obtain passwords to wallets and cards.
Other features of miner bots include:
- Non-standard way to launch the program;
- Having two processes restart each other if you tried to terminate one of them;
- Rebooting the device when trying to access program files or remove them from startup;
- Processes that prevent the antivirus from working properly.
Why is this happening?
It was mentioned above that the malware connects to the pool registered in it.
With the growing popularity of cryptocurrencies, pools began to actively compete for clients in order to minimize the number of unaccepted blocks and increase the profitability of all clients and their commissions.
As a result, the capacity requirements for participants were minimized; in addition, there was no need to in any way confirm the ownership of the capacity being put into operation, since the provision of personal information contradicts the anonymity and decentralization of the industry as such.
In order to partially protect the pools from the machinations of scammers, the owners raised the minimum payout of mined coins.
This step made hidden mining on a small number of PCs almost useless, since in some cases it did not come to the point of withdrawing profits.
On the other hand, such restrictions were not implemented by all key services, which in some way concentrated attackers using virus mining on several platforms.
Separately, it is necessary to say about the qualitative growth of those who did not refuse to make a profit at the expense of others.
The first step in “survival” was to reduce the amount of resources used so that the bot would work longer, because if it doesn’t interfere, then they won’t look for it.
Distribution methods have also improved, hidden links began to be hidden in double and triple archives, redirects and advertising platforms in order to create a full-fledged mining network of several hundred/thousands of computers, giving a few percent of their power to the scammers.
Much wiser hidden mining programs can evaluate the overall performance of the infected PC, as well as the percentage of involvement.
In a situation where the user loads the equipment with his tasks, the miner turns off. In order not to arouse suspicion, when the load subsides, work continues.
One of the anti-virus laboratories in their report notified clients that a number of malicious virus miners determine the user’s activity on the PC and if the equipment is left turned on overnight, the percentage of used capacity increases to 50%.
go
How does virus mining occur?
While traveling on the Internet, the user performs some action that can be disguised as downloading a file/image or clicking on an external link on a social network, resulting in a malicious program being downloaded to the computer.
It is activated, automatically connects to the pool specified by the developer and begins mining.
The main coins that are mined illegally, so to speak, are Monero and ZCash.
One of the reasons is the high anonymity of operations in these networks. Office computers suffer greatly from such activity, as they are massively infected from one source through internal networks.
Separately, it should be noted that not all programs are limited to mining.
Many are given the function of searching and copying wallet addresses of various crypto-services, registration data of exchanges, secret phrases and keys, which are stored by many here on the PC.
Antivirus programs are disguised as official miner programs, for which many set exceptions in the protection system.
An independent search through the list of installed programs or by examining the contents of the “Program Files” is also not always effective, since most users simply do not know what to look for.
During the period of active development of this industry, a number of malicious programs were able to be identified and removed due to the fact that they activated all unused PC resources, which often led to overheating and simply interfered with work.
Modern virus miners have become more modest and occupy from 2 to 5% of free resources, without particularly loading the equipment and without interfering with the user’s ability to work quietly.
go
How to disable system interrupts?
We will not be able to remove the task to complete it. This feature is not supported at the software level. It is important to identify the “troublemaker” - the component that causes the CPU to load almost 100%.
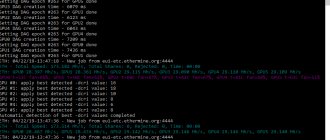
I recommend downloading the portable utility Latency Checker, which analyzes the operation of the equipment in real time and shows when the indicators begin to go off scale.
DPC Latency Checker
At the time of writing this article, I “captured” the following picture:
The situation is normal. But if red splashes begin to appear, the program advises launching the “device manager” and disabling the modules one by one.
- Right-click on “Start” Windows 10 and select the desired option:
In previous versions of Windows, you can get to the specified location through the control panel.
- In the window that appears, we try to deactivate the elements, starting with the most harmless ones - Wifi module, Ethernet network adapter, audio, video. The main thing is to avoid “System devices”, “Processors” and “Computer”, otherwise there will be a crash, reboot and unpredictable consequences:
- We disable it as follows: open a specific category by clicking on the arrow to the left of the name, then we see a nested list of modules (there may be one or more). Right-click and select the “Disable…” operation:
After each deactivation, be sure to look at the load of Latency Checker, the task manager. When “System Interrupts” stop eating up CPU resources, you need to understand which hardware is causing the problem. Next, try updating its drivers manually or automatically using IOBit Driver Booster software. Here are the instructions: