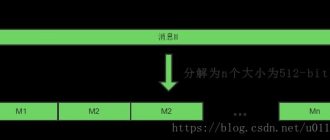
Mining algorithm, or hashing algorithm necessary to decrypt data in the cryptocurrency network and determine its reliability. The development of algorithms is carried out by cryptographer specialists. The scheme is based on processing a "hash" - this is a number encrypted from the content string. It is impossible to encrypt two strings to produce the same hash.
The basic idea of Bitcoin mining is that miners put a group of fresh transactions into a single block, and then perform a hashing operation many times until one of them finds the right number. After this, transactions can be considered confirmed.
Cryptocurrency mining algorithm: what is it and why is it needed?
In cryptography, there is the concept of a hash function; it is responsible for encrypting data, which is subsequently decrypted by the cryptocurrency mining algorithm. The hash function is designed in such a way that there is no “easy way” to get the desired result - you can only select values over and over again until you find one that works.
In Bitcoin, a successful hash is one that begins with a certain number of zeros. The difficulty of finding increases exponentially. Currently, a number must have 17 consecutive zeros in order for it to be considered valid. Thus, only one out of 1.4x1020 numbers will result in a successful result. Finding hash is even more difficult than finding one grain of sand that exists on Earth.
Watch a video that explains what a hashing algorithm is (include subtitles and Russian translation):
Scrypt
Cryptocurrency developers do not like ASICs; they negatively affect the system and scare away miners. Cryptocurrency needs miners because they are the ones who ensure its functioning. With the advent of ASIC, miners who do not want to invest a lot of money in equipment leave the crypt, leaving only industrial giants. This leads to centralization and destroys the very idea of blockchain technology.
The developers are trying in every possible way to delay the appearance of ASICs. This is achieved through the development and use of fundamentally new algorithms for cryptocurrencies. One of these was Scrypt. It appeared after Bitcoin and formed the basis of Litecoin and Doge coins. The design of Scrypt was to use a large amount of memory. It is used to store pseudo-random sequences that are generated at the beginning of the algorithm. The inability to save this data significantly lengthens the calculation process.
When Scrypt first appeared, ASICs for SHA256 were not suitable for it, because they worked on a different principle. Soon similar devices were developed for Scrypt.
Mining algorithm for top cryptocurrencies
List of popular and promising cryptocurrencies available for mining and their hashing algorithms:
| Cryptocurrency | Ticker | Algorithm |
| Bitcoin | BTC | SHA256 |
| Ethereum | ETH | Ethash |
| XRP | XRP | XRP Ledger Consensus Protocol |
| Litecoin | LTC | Scrypt |
| Bitcoin Cash | BCH | SHA256 |
| EOS | EOS | DPoS |
| Bitcoin SV | BSV | SHA256 |
| Cardano | ADA | DPoS |
| TRON | TRX | DPoS |
| Monero | XMR | CryptoNight |
| Dash | DASH | X11 |
| Cosmos | ATOM | PoS |
| NEO | NEO | PoS |
| Tezos | XTZ | DPoS |
| Ethereum Classic | ETC | Ethash |
| NEM | XEM | Proof-Of-Bible-Hash (POBH) |
| Ontology | ONT | PoS |
| Zcash | ZEC | Equihash |
| Bitcoin Gold | BTG | Equihash |
| Ravencoin | RVN | X16R |
| Beam | BEAM | Equihash |
| Grin | GRIN | Cuckoo Cycle |
| Waves | WAVES | PoS |
| Harmony | ONE | PoS |
| Libra Facebook | LIBRA | LibraBFT |
| Algorand | ALGO | PoS |
| Elrond | ERD | PoS |
| Decred | DCR | Blake (14r) |
Ethash
If you choose a mining method, take a closer look at the algorithm that Ethereum runs on. Initially, it was called DaggerHashimoto and was very similar to Scrypt in principle of operation. Just like Scrypt, it has large memory requirements, but, unlike it, it built a large acyclic graph of sequential nodes. Such a system complicated the decryption process and protected it from random selection.
Then the algorithm changed the filling and name. It began to be called Ethash, which is more associated with the name of the main coin that operates on it. It now hashes the metadata of the last block of the system using the Nonce key. The key is a regular binary number. Ethash has become even more protected from accidentally selecting the correct value. Selecting a hash is only possible by searching through all possible options.
The Etherium network is second only to Bitcoin in popularity, but Ether is still mined on video cards. This makes it one of the best mining algorithms available. He especially loves AMD cards with at least 4 GB of RAM. As network complexity increases, memory requirements increase. Nvidia cards from the Pascal line also show good results.
Of course, attempts are being made to develop ASICs for Ethash, because Ethereum is one of the most expensive coins, and the development of a truly powerful device would make the creator rich. All ASICs offered today are GPU farms packaged in a case. There are rumors that the Chinese ASIC manufacturer Bitmain is preparing a full-fledged device for Ethash, but there has been no official information from the manufacturer yet.
Basic cryptocurrency mining algorithms
Let's look at the most common mining algorithms today.
SHA-256
The acronym SHA stands for Secure Hash Computation.
This computational method ensures that the information in a cryptographic data set is immutable. The information is encrypted, or coded, so it is secure and can only be accessed by people who have the code. In 2001, the US National Security Agency developed the SHA-2 algorithm. SHA-256 is a variation of it. The name comes from the fact that it works with 256-bit numbers. In other words, a particular bit of data is encoded and transformed into a code of 256 fragments. Code processing time in SHA-256 takes 6-10 minutes.
Scrypt
The Scrypt hashing algorithm uses 11 logical protocols for proof of work (PoW).
The biggest benefit of using Scrypt is efficiency, as it uses 30% less power and requires less cooling. Multi-level computation begins by loading information using the SHA-256 hash process. At this time, an analysis of the link structure is calculated, without which it is impossible to complete the hashing. Compared to SHA-256, Scrypt consumes less power but significantly more memory. Also in Scrypt it is possible to reduce the hash size, which makes the calculation faster.
Ethash
Ethash was developed specifically for Ethereum in order to reduce vulnerability to ASIC miners.
The algorithm is based on data mining. Previously, Ethereum used an algorithm called Dagger-Hashimoto, and Ethash is essentially an updated and improved version of it. There was a strong emphasis on protection against ASICs, but this did not help for long - the interest of ASIC manufacturers in Ethereum increased, and soon such devices were released onto the market, which caused outrage in the community. It was even proposed to “ban” overly powerful devices connected to the network.
X11
The X11 algorithm was developed in 2014 and, like Ethash, was needed to counter ASIC miners and maintain the competitiveness of owners of video cards and processors. X11 works with 11 different hash functions simultaneously. First, the first function creates a hash, then passes the baton to the second, and so on.
All eleven algorithms included in X11 were commissioned by the US National Institute of Standards and Technology to develop a new SHA-3 function with improved security compared to its predecessors. There were 64 candidates, only 11 passed the competition.
CryptoNight
CryptoNight is a mining algorithm designed for use on ordinary processors. The algorithm is initially coded in the CryptoNote code base. Cryptonight takes 2MB of information, extracts the base data, mixes it with the sequential data and produces a perfect output.
The main advantage of the protocol is the possibility of additional mixing. Transactions thus become more confidential. CryptoNight is used by many cryptocurrencies, of which Monero is the most famous.
Equihash
This cryptocurrency mining algorithm is an asymmetric Proof-of-Work system that is primarily memory oriented. The amount of work that a device can produce when running this algorithm is determined mainly by the amount of RAM it is equipped with.
The Equihash algorithm is called resistant to ASIC miners. Memory is an expensive computing resource, and therefore its optimization on an ASIC chip will be an expensive and unprofitable process for the user. As a result, the ASIC mining process will become less efficient and powerful.
Decred
Decred cryptocurrency uses a hybrid consensus mechanism that combines the principles of PoS and PoW. Such a system ensures that the development of the project cannot be subject to the control of strong interest groups, and changes cannot be made to the blockchain without the consent of the community.
PoW in Decred implies a reward of 30 coins per mined block, which are divided between miners, voters and the project development fund. Voters can then cast their votes for or against proposed adjustments to the chain. For the fact that they protect the network by storing their bets, they are given 30% of the income from each generated block.
Quark
Quark is a cryptocurrency mining algorithm based on a hash function with nine levels of encryption. The algorithm does not require a large amount of RAM, and also contains built-in protection against high-level hacker attacks (64 bits). Features low energy consumption. Quark was developed in 2013 and implemented six encryption functions: Grostl, Blake, Keccak, etc.
The Quark algorithm is used in PoS and PoW consensus mechanisms to make maintaining the working state of a cryptocurrency system more certain and secure. Compared to the SHA-256 used in Bitcoin, Quark is resistant to SPOF (single point of failure), which can cause the entire system to fail.
X15
X15 is based on X11, but instead of using 11 hashing functions, it uses 15. Due to this move, resistance to hacker attacks is significantly increased. If a hacker breaks one of the fifteen functions, the developers will immediately improve it so that the system continues to remain secure. An attacker who wants to hack the entire system will need to go through all 15 functions one by one, and do it quickly.
SHA-2
A secure hashing algorithm, based on which at least ten improved options have been developed, including SHA-256. All hash functions used in the family are based on the Merkle-Damgaard structure.
The idea is that the original information is divided into blocks after addition, and then each of the blocks is divided into sixteen words. Next, each message block is passed through a cycle consisting of 80 or 64 rounds of shuffling. At each stage, two words are transformed, and the function of this transformation is specified by the remaining 14 words.
Cuckoo Cycle
Cuckoo Cycle is one of the most promising ASIC-resistant algorithms to date. It was originally invented to protect against spam in email. However, the architecture turned out to be quite suitable for mining cryptocurrencies on GPUs. Focuses primarily on memory usage, so it requires significantly less computational energy than other PoW algorithms. Consequently, cooling costs are also reduced.
Proof of Burn - “proof of burning”
Many experts consider this algorithm for mining and storing coins to be not entirely correct. Nevertheless, it has the right to life and in some cases is used quite effectively. Its essence is as follows. The user sends a certain number of cryptocurrency coins to the account established by the system. Such an action allows a participant in the system to “mine” new coins under exactly the same conditions as other users who have paid a fee. By the way, you won’t be able to withdraw or spend money from your commuting account. It makes sense to talk about a fixed fee for the right to work. So, at one time, gold miners bought up plots. And just like in our days, someone was lucky and “hit the jackpot,” while others remained losers.
Other algorithms
The following types of cryptocurrency mining algorithms are also found:
- SHA-3 (Keccak). The protocol is based on the Sponge design. To obtain a hash, the original information is taken and then expanded to a length that is a multiple of R. A byte is added to the message, a number of zeros and a trailing byte with the value 0x. Then, to obtain the desired number, a hash function is repeatedly applied to the received data.
- Blake. It consists of three main components - an internal structure that guarantees protection against collisions, an iteration mode that counteracts external attacks, and a compression algorithm. The result is a carefully analyzed safe function.
- Lyra2RE. It was developed as a replacement for the outdated Scrypt-N algo for the Vertcoin cryptocurrency. The main goal is to reduce energy consumption in the process of token mining. The algorithm was successfully changed in mid-2014.
CryptoNight
Became famous thanks to the popular coin Monero. CryptoNight is similar to Scrypt and was also created to avoid ASICs. It also uses memory and requires a large amount of RAM to store data used in calculations.
All predecessors - Bitcoin, Litecoin, Dash - became victims of ASICs. The Monero developers decided to try to avoid this, which is where they have had the greatest success. They promised to make adjustments to the mining algorithm every six months, making planned hard forks. For an ordinary miner, these changes will be invisible, and ASICs after such an update will become unsuitable for mining. The calculation is based on the fact that purchasing an ASIC is quite expensive. If devices become obsolete every six months, it will be unprofitable for miners with specialized equipment.
Monero is based on a good algorithm, for whose developers the fight against ASIC is not an empty phrase. The only threat to decentralization remains from mining bots. Hackers distribute malware that, using the equipment of unsuspecting users, mines cryptocurrency into their wallets.
Lyra2Z
In early 2022, Zcoin implemented the Lyra2Z algorithm to combat botnets and cloud miners. Zcoin is temporarily using this algorithm until the development of MTP (Merkle Tree Proof) is completed, which will focus more on the CPU. Lyra2z uses Blake256 and Lyra2. Information about it is not particularly widespread, but it was originally designed for both video cards and the processor.
It uses very little electricity, and is a “cool algorithm” that means you don't have to worry about the GPU overheating while mining. Lyra2z was recently added to NiceHash and is still ASIC resistant. But there are FPGAs for Lyra2Z that produce ~20 MHz/s and are equal to 6 x 1080 TI. To mine the Lyra2z algorithm, it is useless to overclock the memory. It also consumes less than 60% power. It runs quieter and cooler on processors.
Lyra2z miners:
- Zcoin official CPU miner,
- JayDDee/cpuminer-opt,
- SGMiner,
- Tourgasm ccminer,
- Nemos Miner.
Popular coins: Zcoin, GINcoin.
There is also Lyra2h. This algorithm is designed for the HPP coin. Power consumption is in line with most other major heavy-duty algorithms. Available for CCminer and SGminer.
Lyra2Rev2 is a VTC and MONA algorithm, best suited for NVIDIA GPUs. Mined on MKXminer, CCminer and SGminer.
Equihash
The principle of operation is very similar to Ethash. Developed by Dmitry Khovratovich and Alexander Biryukov on the basis of the University of Luxembourg for the ability to carry out mining on a home computer. The only thing it is very demanding on is RAM. The algorithm design is based on a cryptographic concept called the Generalized Birthday Problem.
Although the Ethash and Equihash mining algorithms are still resistant to ASICs, video cards are also not cheap. Due to the great popularity of Etherium, Ethash became difficult to mine, and users began to migrate to Equihash. Equihash is powered by Zcash and Bitcoin Gold.
In most cases, the development of cryptocurrency occurs according to this scenario: before the network has time to work, ASICs immediately appear. The competitive nature of mining and the high cost of coins encourage people to look for ways to mine more efficiently.
ASICs destroy the very principle of decentralization, surviving small miners and leaving only those who are able to buy powerful equipment. Many believed that with the advent of ASICs, the era of mining on processors and video cards had passed, because the owners of these devices now cannot even recoup electricity, not to mention profit. But the experience of ASIC-resistant coins suggests the opposite.
The choice of mining algorithm depends on your equipment and how much you are willing to invest in its support and modernization. Of course, mining on video cards does not bring as much profit as on ASIC, but due to the rise in prices of coins such as Ethereum, zcash and monero, this gap is closing. In addition, the device is only suitable for mining, and you can use video cards for any purpose.
How to assemble a mining farm - choosing an operating system
We will not dwell in detail on the hardware, because now all modern motherboards support mining on four or more video cards (most 8 or more video cards using cheap port expanders).
We will be primarily interested in the operation of operating systems. Here, the vast majority of miners are clearly divided into two groups - working on Windows and working on Linux, and the vast majority of the latter do not use Linux in its pure form, but ready-made mining operating systems like RaveOS.