Keccak is a cryptographic function that won a cryptographic algorithm competition in 2012 and was approved as a new US federal information processing standard.
The purpose of the competition, conducted by the US National Bureau of Standards, is to support the innovative and industrial development of the country and increase its competitiveness. Since hash algorithms are constantly under attack, new standards and technologies have to be created to improve not only economic security, but also the overall quality of life of people. And the new Keccak hashing algorithm is one of NIST's initiatives.
SHA-256 hashing algorithm
Before we delve into the specifics of this algorithm, which is the most studied in mining, we will answer a common question: what does “SHA” mean? This stands for "secure hashing algorithm". It is a calculation method designed to ensure that the information in a data set (or digital currency, block of data) does not change from its original form. It is secure because it is encrypted or encrypted and is accessible only to the owners.
The SHA-2 algorithm suite was developed and released in 2001 as a security standard by the US National Security Agency (NSA). SHA-256 is part of the SHA-2 family. This group of algorithms followed SHA-0 (released in 1993) and SHA-1 (released in 1995 as a replacement for its predecessor). This specific algorithm is called SHA-256 because it generates message digests that are 256 bits in size. This means that a specific piece of data (or data that will be technically correct) is converted and encoded into a 256-bit code.
The encrypted data is called a "hash". Processing time for a SHA-256 block is typically six to ten minutes. It is a classic mining algorithm. The process is to select the correct hash, when it is selected, the block is mined. At low power, it is possible to mine on a processor (and even in a column), but in the case of Bitcoin only on special equipment, such as ASIC.
There is also SHA-256-D (this is what is used in BTC). This term is often considered synonymous with SHA-256, which can be said to be a type of algorithm.
D stands for double, that is, doubled. The process runs a second time, encrypting the hash once again. Despite the extra step, the time required to process a block of SHA-256-D data is the same as SHA-256: six to ten minutes.
List of popular SHA-256 cryptocurrencies: Bitcoin, Mastercoin, Namecoin, Blakecoin, Bytecoin. The full list of coins is in the table below.
List of Kecak coins
As we already said, there are not many coins that use this Proof of Work algorithm, but there are some famous coins such as Maxcoin and SmartCash. There are currently only three coins in active development. Do your research and choose your coin wisely before you start mining Keccak coins.
- SmartCash – SMART
- MaxCoin – MAX.
- CreativeCoin – CREA
- Slothcoin (SLOTH) – inactive
- 365Coin (365) – Inactive
- Galleon (GLN) – Inactive
- Helix Coin (HXC) – inactive
- CryptoMeth (METH) – inactive
- BitcointalkCoin (TALK) – Inactive
SmartCash – SMART
SmartCash is a cryptocurrency focused on collaboration, community management and growth. & decentralized economy. This coin has masternodes, as well as smart rewards and instant payment, a feature that allows you to make instant purchases in store and online.
Website: https://smartcash.cc/
Researcher: https://insight.smartcash.cc/
Characteristics of SmartCash:
Maximum number of coins: 5 000 000 000
Block time: 55 seconds
Coin type: PoW / Masternodes
Block size: 1 MB
Algorithm: Kecak (PoW)
Complexity Management: BRNDF
Coins per block: 5000 coins (gradually decreasing according to the equation below)
Reward split: 30% (miners/SmartRewards/SmartNodes) and 70% (SmartHive/HiveTeams)
MaxCoin – MAX.
MaxCoin is an old school (no pre-mine), open source cryptocurrency that uses the next generation SHA-3 hashing algorithm. This coin has no transaction fees and no ICOs, advertising, donations, bounties or airdrops. It is a pure cryptocurrency, community based and focused on organic growth.
Announcement: https://bitcointalk.org/index.php?topic=438150.0
Website: https://www.maxcoinproject.org/
Explorer: https://explorer.maxcoinproject.net/
Technical characteristics of MaxCoin:
Maximum number of coins: 100 million
Block time: 1 minute
Coin type: PoW
ICO / Premine: No
Algorithm: Kecak (SHA-3)
Difficulty retargeting: Every block using Kimoto Gravity Well
Block reward: 8 coins per block / halved every ~4 years
Transaction costs: Zero – no transaction fees (close to zero)
CreativeCoin – CREA
Creative Coin or Creative Network is a decentralized creative community. It is a blockchain platform for multimedia registration and distribution of content that certifies the authorship and license of any work or creation, making it indelible.
Announcement: https://bitcointalk.org/index.php?topic=1809920.0
Website: https://www.creativechain.org/project/
Scrypt
It is a multi-layered algorithm that begins by running data through the SHA-256 hash process. It then uses the elements of the SALSA algorithm to complete the hash generation. The process of guessing a hash is complicated by the fact that the selection of options becomes more complicated: noise is added from randomly generated numbers. Uses a password-based key generation standard. It is difficult for an attacker to get to the code using brute force.
Scrypt takes up much more memory than SHA-256, but its lower energy and computational requirements make it a good choice for miners. At one time, coins could be mined on processors, and there were no ASICs for them due to RAM requirements. Today the devices have already been created. Unlike SHA-256, Shrypt miners can change the hash size to a smaller number. This, plus some other factors, makes it a faster mining algorithm. Scrypt can completely process a block of data in just thirty seconds, although some argue that this speed poses a risk to transaction security until several more generations of blocks have been generated.
Example of coins on Scrypt: Auroracoin, Novacoin, Dogecoin, Litecoin, Smartcoin, Worldcoin, Reddcoin. Programs:
- sgminer
- bfgminer
- cgminer
- cgminer (all for AMD)
- CudaMiner (for Nvidia)
Since the algorithm was unable to deal with ASICs, an improved Scrypt-N algorithm was created, initially in Vertcoin. It uses "Adaptive N-Factor", where N stands for memory used, which is constantly increasing. For example, from 256 kB to 4 GB. This system allows small mining farms to exist.
Programs:
- vertminer
- CudaMiner
Expand SHA-3
SHA-3 has not yet made it into most major platforms. Some platforms (such as MacOS X and iOS) still rely on the libcrypto library, which only supports SHA-1 and SHA-2. One way to deploy SHA-3 on your desired platform is to compile the hashing algorithm as a static library. Then install the new library into the /urs/lib or /usr/share directory, this assumes you have write permissions to those directories. But there is another way to deploy SHA-3. This method can work on Mac OS X and IOS, which is deployed as a framework package.
A framework package is a hierarchical collection of files that together form a dynamic library. Unlike most packages, the framework package is transparent; its contents can be browsed at will, just like the contents of other regular directories. The framework bundle can be located in a shared directory (such as ~/Libray/Framworks), or you can copy the framework bundle into the application bundle and use it as a private resource. Access to the framework package is achieved through the NSBunble class or through a kernel-based batch service.
Figure 4 shows the package structure of the SHA3 framework. At the top are four directory links and a directory called Versions. In the versions directory there is another link to directory and subdirectory A.
Listing 1 shows how to add SHA-3 support to the NSString class. Here, the SHA3String class declares two method prototypes (lines 8–9). The sha3AsCstring class method uses the cStringUsingEncoding: instance method (line 25) to retrieve the original message bytes. It declares standard ASCII as the desired text encoding. This method counts the number of bytes of the message and creates a hash variable tHash (lines 29-30). Then pass the number of bytes, message text, and hash variables to the input function Hash() (line 33). The Hash() function returns the 512-bit hash value of the message, and then sha3AsCstring re-converts the hash value to a constant string (line 36). By the way, BitSequence is a Keccak setting for the char type.
// - File:SHA3Category.h // #import #import #import "KeccakNISTInterface.h" @interface NSString (SHA3String) - (const char *)sha3AsCstring; - (NSData *)sha3AsData; //... @end // - File: SHA3Category.m // @implementation NSString (SHA3String) // Return the SHA-3 hash as a C-string - (const char *)sha3AsCstring { const char *tTemp; const BitSequence *tData; BitSequence *tHash; NSUInteger tLen; // extract the message data tTemp = ; tData = (const BitSequence *)tTemp; // prepare the hash variable tLen = strlen(tTemp); tHash = malloc(sizeof(BitSequence) * 32); // hash the message data Hash(512, tData, tLen, tHash); // return the hash result tTemp = (const char *)tHash; return(tTemp); } // Return the SHA-3 hash as an NSData object — (NSData *)sha3AsData { const char *tHash; NSUInteger tLen; NSData *tData; // generate the SHA-3 hash tHash = ; // prepare the hash object tLen = strlen(tHash); tData = ; // return the hash object return (tData); } //… @end
The sha3AsData class method returns the hash value of the message in the form of an NSData object. It uses sha3AsCstring to process the message bytes (line 48). Then use the dataWithBytes: length: factory method to create this object (lines 52-53).
Listing 2 shows that SHA-3 is a class in singleton mode. Singleton mode provides a public, global access point for accessing the SHA-3 algorithm. It manages its own memory management, so no explicit handling is required.
// - File:SHA3Single.h // #import #import "KeccakNISTInterface.h" // Define the enum constants typedef enum _SHA3_SIZE {SIZE_224 = 224, SIZE_256 = 256, SIZE_384 = 384, SIZE_512 = 512} SHA3_SIZE; // Declare the class interface @interface SHA3Single : NSObject { @private NSUInteger pSize; } @property (readwrite) NSUInteger hashSize; + (id)defaultGenerator; + (id)generatorForSize:(NSUInteger)aSize; — (void)hashMessage:(const char *)aMesg into:(BitSequence *)aHash; — (void)hashObject:(id)aMesg into:(BitSequence *)aHash; @end // — File: SHA3Single.m // // Declare the static global static SHA3Single *gHash; // Define the singleton class @implementation SHA3Single @synthesize hashSize = pSize; // Create the default SHA3 generator + (id)defaultGenerator { @synchronized(self) { // check the static global if (gHash == nil) { // create the instance gHash = [ init]; // set the output hash size gHash.hashSize = SIZE_512; } } // return the singleton instance return (gHash); } // Create a “custom” SHA3 generator + (id)generatorForSize:(NSUInteger)aSize { @synchronized(self) { // check the static global if (gHash == nil) { // create the instance gHash = [ init ]; // set the output hash size gHash.hashSize = aSize; } } // return the singleton instance return (gHash); } — (void)hashMessage:(const char *)aMesg into:(BitSequence *)aHash { NSUInteger tLen; // generate the SHA-3 hash tLen = strlen(aMesg); Hash(self.hashSize, (const BitSequence *)aMesg, tLen , aHash); } — (void)hashObject:(id)aMesg into:(BitSequence *)aHash { const char *tData; NSUInteger tLen; // parameter check if ((aMesg != nil) && (aHash != nil)) { // identify the message object if ([aMesg isKindOfClass:]) // — object:NSString tData = ; else if ([aMesg isKindOfClass:]) { // — object:NSData tLen = ; tData = malloc(tLen * sizeof(char)); ; } else { // handle other Cocoa objects // - RESERVED } // hash the raw message bytes tLen = strlen(tData); Hash(self.hashSize, (const BitSequence *)tData, tLen , aHash); } } @end
The SHA3 singleton class first declares a private property pSize (line 17). This attribute sets the desired hash bit size. This class also declares a hashSize attribute variable and four method prototypes, two of which are factory methods (lines 19–27).
The class then declares a static global variable gHash to reference the singleton instance (line 33). Then define a hashSize variable, two factory methods, and two instance methods. The factory defaultGenerator method detects the global variable gHash (line 45) and generates an instance of the SHA3 singleton (line 48). It also sets the default hash value for the pSize attribute to 512 bits (line 51).
Factory method generatorForSize: takes hash size as input. At the same time, it checks the global variable gHash and creates an instance of SHA3Single. And it updates the pSize attribute to the specified size (line 71).
The hashMessage: into: instance method takes the message text (aMesg) and a hash variable (aHash) as input. It counts the number of bytes of the message and passes the number of bytes of message text and hash variables to the Hash() input function (lines 85-88). The Hash() function then stores the hash value of the message in the variable aHash.
The hashObject instance method: into: takes a shared Cocoa object (aMesg) as one of its inputs. It uses the isKingdOfClass: instance method (lines 101-102, 105-106) to identify this object. Once the type of this object is determined, hashObject: into: uses the correct code to extract the original message text (lines 104, 112). At this time, it also calculates the number of bytes of the message and uses Hash() to generate a hash value of the message (lines 121–124). Then store the resulting hash value in aHash.
To use the SHA-3 singleton model, you must create an instance using the appropriate factory method. The following code snippet creates a 512-bit SHA-3 hash of the message.
SHA3Single *tSHA3; tSHA3 = [SHA3Single defaultGenerator];
Then use the appropriate instance method to process the message. For example, the following code snippet uses the hashMessage: into: method to process NSString objects.
NSString *tMesg; const char *tHash; //… tMesg = ; [tSHA3 hashMessage:tMesg into:(BitSequence *)tHash];
Xcode SHA3 framework project Can be used as a reference.
Scrypt-jane
Also uses N-factor to increase memory. It is believed that such coins are more profitable to mine on a CPU. In 2014, Litecoin (using scrypt) appeared as an alternative for miners when mining on video cards became unprofitable and ASICs began to dominate. The basic algorithm ensured the decentralization of such coins. The following parameters are used:
- Nfactor increases the complexity and memory factor,
- rfactor increases the number of blocks,
- pfactor: increases processor complexity.
Scrypt-n uses SHA256 as a hash function with progressive N. Scrypt-Jane is also with progressive N, but also uses a combination of hash functions (BLAKE256/512, Skein512 and Keccak256/512) or can parametrically change the function it uses.
Coins: YaCoin (YAC), Ultracoin (UTC), Velocitycoin (VEL).
Programs:
- yacminer
- CudaMiner
Algorithm X11/X13 and more
The X11 algorithm was created back in 2014 by Evan Duffield, who is the main developer of the then Darkcoin cryptocurrency (now the Dash coin). Initially, he wanted to develop an algorithm that would make cryptocurrencies resistant to ASICs, which, as you understand, are considered the killers of decentralization. To this end, he combined 11 different hash functions in one algorithm: Blake, Bmw, Groestl, Jh, Keccak, Skein, Luffa, Cubehash, Shavite, Simd, Echo. It is noteworthy that Evan Duffield himself never ruled out the possibility of developing ASIC devices for X11 (and he was not mistaken). In his interviews, he argued that such equipment will be created in any case, but before that, manufacturers will have to work hard. Today, specialized machines for mining X11 coins already exist, but mining using this algorithm is still profitable on GPUs. The main advantages of the X11 algorithm are:
- its safety, since 11 functions increase security by 11 times,
- lower entry threshold because, according to its ideology, it requires less investment in equipment and electricity.
Programs:
- sph-sgminer X11mod,
- ccMiner.
Popular coins with this algorithm are DASH, Monacocoin, SuperCoin,
Today, a number of even more advanced algorithms have been developed, built on a larger number of hash functions. They are called X12, X13, X14, X15, X16, X17, according to the number of functions they use.
There is also a C11 algorithm that connects blake, bmw, groestl, jh, keccak, skein, luffa, cubehash, shavite, simd and echo. It is very similar to X11. The only difference is that these 11 algorithms are related in a different order. You can modify the Antminer D3 ASIC algorithm on C11. Suitable for NVIDIA, this is a good stable algorithm in which the power does not fluctuate much. Additionally, most coins using c11 are new and low difficulty, so if you have a small farm, you can even try solo mining.
Deep into Kecak
At the time of writing, NIST has not released a formal document for SHA-3 (FIPS 180-5). Therefore, the following information is obtained from Keccak reference documents and third parties.
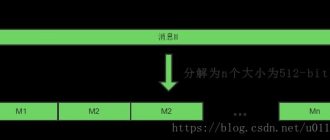
The Keccak algorithm consists of three parts (Figure 1).
Hash() function is used as input function. This requires 4 input parameters: hash bit size (n), message text (M) and its size in bits (N), and hash variable (H). This hash variable should have the following malloc() function Create:
HashReturn E; char *H; n = 224; H = (char *)malloc(sizeof(char) * n / 8); //… E = Hash(n, M, N, H);
The Init() function prepares the internal state (S) for the specified hash size. The Update() function begins to compress or absorb the phase. Here the message text is concatenated according to the internal state and then replaced. The Final() function starts extracting or compressing the phase. This is a hash value extracted and collected from the internal state. The collected hash of the first n bits is then used as the message hash. All four functions return an error result. Returning 0 means the function completes without errors.
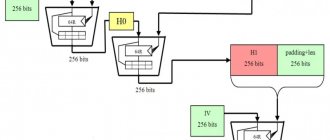
Figure 2 shows the internal state data structure. The C structure named spongeState contains 8 fields, two of which are fixed arrays (marked in red). The state array field stores the real state bytes, and the dataQueue array field stores the message bytes that will be concatenated and converted.
The capacity field is the hash capacity (denoted c). Its value is set to twice the hash size (2 * n). The rate field is the length of the message bits processed in each cycle. It is set to 1600-c. The bitInQueue field is the message length in bits reserved in the dataQueue array field. The fixedOutputlength field is the desired hash size (denoted by n). The compression area is a mode sign. If set to 0, keccak is in compression mode. If set to 1, keccak is in decompression mode. Additionally, filedbitsAvailableForSqueezing stores the length of the status bit combined into the final message hash.
Keccak uses 24 conversion cycles to reduce the message text to a hash value. Each loop calls five modules continuously, as shown in Figure 3.
The θ module converts the internal state into a 5x5 array, each element of which is 64 bits. It calculates the same part of each column and then uses the exclusive OR operator (XOR) to combine them. It then XORs the resulting parity result with each status bit as follows:
S
[j][k] ^= parity(S[0…4][j-1][k]) ^ parity(S[0…4][j+1][k-1]) where i = 0 …4;
j = 0…4; k = 0...63 The ρ module cycles through each 64-bit element according to the triangle number order. But circular motion excludes the element S[0][0]. The φ module converts 64-bit elements. The conversion follows the fixed assignment pattern shown below:
S[j][2*i + 3*j] = S
[j]
The χ module adds nonlinear characteristics to the conversion loop. It uses only three bitwise operators: AND, NOT and XOR to combine string elements. Then write the result to a status array like this:
S
[j][k] ^= ~S[k] & S[k]
Module ι breaks any symmetry created by other modules. It does this by XORing the element in the array with a loop constant. This module has 24 loop constants to choose from. These constants are defined internally by Keccak. However, due to Keccak's source code in C, it is too large to be listed here.
CryptoNight
CryptoNight is a PoW algorithm that was originally used by CryptoNote (more on that below) and Bytecoin. It is aimed, again, at combating privileges from large farms and ASICs, so that all network users can maintain functionality with ordinary devices. That is, not to create an insurmountable gap between those who turn on the miner on their computer and those who order special machines for this. Classically, memory-sensitive algorithms are used to solve this problem. A large block of data is allocated in RAM, which changes unpredictably. The algorithm also prevents internal parallelism, meaning that running N concurrent threads would require N times more memory at the same time. The CryptoNote protocol, unlike Scrypt, makes it so that each new block (64 bytes) depends on all the blocks in the blockchain that came before it. This requires about 2 MB of RAM, which is the minimum cache size of modern processors. And this amount of RAM eliminates the use of ASICs. It is necessary to distinguish between CryptoNote and CryptoNight. The latter is one of the implementations of the general CryptoNote protocol. The CryptoNote protocol has a high level of anonymity. Some part of the community believes that money must be anonymous in order to guarantee a person’s freedom. Details of transfers between the client and the seller should not be shared with third parties. To maintain proper confidentiality, the following properties are necessary: the transaction cannot be tracked, the relationship between payments cannot be traced. CryptoNote offers a scheme that guarantees anonymity for the sender. This protocol uses a ring signature system - someone from the group (it is impossible to determine who) signed the transaction, which means it is legitimate. The CryptoNight algorithm is different in that it can still mine relatively well on a CPU. Of course, it will be ridiculous money, but at least it is possible.
Programs:
- Cast XMR,
- Claymore's CryptoNote,
- SRBMiner CryptoNight,
- XMR-Stak.
A good site for selecting coins with this algorithm is https://minecryptonight.net/. CryptoNight is used in XMR, ETN, KRB and other coins. For mining with this algorithm, AMD is better, especially new models.
It has various options:
- CryptoNight-Lite is less resource-intensive and suitable for mobile devices.
- CryptoNight-Heavy is the exact opposite.
- CryptoNight v1 to combat ASICs, etc.
In general, coins with this algorithm are chosen for mining without developed equipment, and also often for ideological reasons - in support of anonymous cryptocurrencies.
Equihash
Equihash is a proof-of-work algorithm developed by Alex Biryukov and Dmitry Khovratovich. Was introduced in 2016. It is based on the "Birthday Paradox" from computer science and cryptography and the extended Wagner algorithm.
The paradox is that in a group of >23 people, the probability that two random people have the same month and date of birth is above 50%. The probability will reach 100% if the group consists of 367 people (more than days in a year). But in the case of 23 people, such a high chance does not seem likely, because ordinary people lose sight of the fact that there are 253 pairs for comparison.
Equihash has very efficient block validation. This will be important in the future for light clients on limited devices or for implementation within different blockchains. It is memory-oriented, that is, the capabilities are determined by the amount of RAM. Again, it works against ASICs. But Bitmain released a device for mining coins with this algorithm, which caused new forks. Overall, Equihash is a secure, democratic and private option. NVIDIA cards are suitable for it; they work with it more stable and productive. The most popular coins are: Bitcoin Gold, ZCash, Komodo, ZenCash, ZClassic.
Limitations of SHA-1 and SHA-2
One cannot ignore the fact that SHA-1 and SHA-2 use the same processing mechanism. Merkle-Damgard said that successful attacks on SHA-1 would impact the security of SHA-2 when processing message text.
Let's take the example of SHA-1: in theory, a brute force hack requires at least 2 to the 80th power (one cycle of the hashing cycle) to collide and break. However, in February 2005, Wang Xiaoyun (transliteration) and colleagues used differential path attacks to complete the SHA-1 loop collision cycle from only 2 to 69 degrees. In August 2008, Martin used this method. Cochran confirmed.
By 2012, Mark Stevens was using a series of cloud servers to perform an SHA-1 differential path attack. The attack collision was completed at the 58.5th power of 2, and he estimated that after the 61st power-up cycle of 2, it could be formed. A complete library of hash collision passwords.
Regarding SHA-2, attacks on SHA-2 hashes with a limited number of rounds are the only successful category. Attacks against 46 rounds of SHA-2 (512-bit variant) and 41 rounds of SHA-2 (512-bit variant) are most effective. It takes 2253.6 cycles to crack the 256-bit version, and 2511.5 cycles to crack the 512-bit version.
In fact, even if it has not been announced that a full reincarnation of SHA-2 has been successfully cracked, there is no doubt that the attack mechanism is being developed privately. This is one of the reasons why NIST sponsored the SHA-3 competition, which also led to the development and recent implementation of Keccak.
Ethash Dagger-Hashimoto
Etash is a proof-of-work for coins based on Ethereum, which also initially struggled with centralization. Intensively uses device memory. The latest version of Dagger-Hashimoto has changed many of the original features. The algorithm works according to the following principle:
- there is a seed that can be calculated for each block by scanning the block headers up to a certain point,
- from the seed you can calculate a pseudo-random cache of 16 MB. Light clients store cache.
- From this, a 1 GB dataset can be created, with the property that each element in the set depends on a small number of elements from the cache. Full clients and miners store a data set that grows linearly over time.
- Mining involves capturing random pieces of a data set and combining them. The large data set is updated once every 30,000 blocks.
Works well with AMD cards such as RX 470, 480, 570 and 580 and gives good returns. Coins: Ethereum, Ethereum Classic, Musicoin, Ellaism.
How to mine ELLA
Lyra2Z
In early 2022, Zcoin implemented the Lyra2Z algorithm to combat botnets and cloud miners. Zcoin is temporarily using this algorithm until the development of MTP (Merkle Tree Proof) is completed, which will focus more on the CPU. Lyra2z uses Blake256 and Lyra2. Information about it is not particularly widespread, but it was originally designed for both video cards and the processor.
It uses very little electricity, and is a “cool algorithm” that means you don't have to worry about the GPU overheating while mining. Lyra2z was recently added to NiceHash and is still ASIC resistant. But there are FPGAs for Lyra2Z that produce ~20 MHz/s and are equal to 6 x 1080 TI. To mine the Lyra2z algorithm, it is useless to overclock the memory. It also consumes less than 60% power. It runs quieter and cooler on processors.
Lyra2z miners:
- Zcoin official CPU miner,
- JayDDee/cpuminer-opt,
- SGMiner,
- Tourgasm ccminer,
- Nemos Miner.
Popular coins: Zcoin, GINcoin.
There is also Lyra2h. This algorithm is designed for the HPP coin. Power consumption is in line with most other major heavy-duty algorithms. Available for CCminer and SGminer.
Lyra2Rev2 is a VTC and MONA algorithm, best suited for NVIDIA GPUs. Mined on MKXminer, CCminer and SGminer.
Keccak Algorithm (SHA-3)
Keccak is also known as SHA-3 (Secure Hash Algorithm 3). It is the latest generation of secure hashing algorithm released by NIST (National Institutes of Standards and Technology) in 2012. OB integrates the sponge family of cryptographic functions and is designed as an alternative to SHA-256. Compared to the past, it works much faster and safer. You can find a lot of information about him on the Internet. For example, .
Keccak is not 100% ASIC resistant. It is actually ASIC friendly, but as far as we know there is no ASIC currently available for this algorithm. Although there are suspicions that Bitmain is mining SmartCash, it is not yet offering the miner to the public. Maxcoin was the first to use Keccak (SHA-3) as a Proof of Work algorithm, and then several other coins began implementing it. Not CPU compatible, NVIDIA graphics cards work best. Below is a list of Keccak coin mining software.
- CCMiner Alexis is a very fast miner for NVIDIA,
- Claymore miner and SGMiner for AMD,
- If you are using Hive OS or Simple Mining OS (SMOS) mining platforms, then the standard ccminer supports the Keccak PoW algorithm.
Coins: MAX, SLOT, METH, NXS, SMART.
Despite its advantages, Keccak is not that popular among miners. The main reason is that with this algorithm there are only a small number of coins.
Features of the algorithm
The name algorithm is correctly pronounced as “Ket-chak”. It has another name – SHA-3. This is the work of four developers:
- Guido Bertoni;
- Joan Daemen;
- Michael Peters;
- Giles Van Ass.
Keccak uses an innovative "sponge mechanism" to hash the message text. It has an average speed of 12.5 cycles per byte on an Intel Core 2 processor, and its simple design is well suited for hardware implementation.
Keccak can withstand known attacks with a minimum difficulty of 2n, where n is the hash size. It has a large margin of safety. To date, third-party cryptanalysis has not shown serious flaws in Kekcak. However, the creators of Keccak are participating in the Crunchy Crypto Contest, where challenges are set, rules are determined, and the status of the collision and Keccak Crunchy preview image is reported.
There are three parts to the Kecsak algorithm.
The Hash(n, M, N, H) function serves as the input function. It takes four input arguments:
- hash size (n) in bits;
- message text (M);
- message size (N) in bits;
- hash variable (H).
The SHA-3 standard algorithm has the structural design of a sponge, where all input data is first absorbed and summed over node 2 with state invariants, then multi-series permutations are created inside the cryptographic sponge and the encrypted result is “squeezed out” at the output.
To encrypt a string, it should be split into many fragments of a certain size and at each round all the resulting parts should be mixed not into the full 1600-bit state, but only into the upper size (in the picture this is the “r” gap). And this happens at every hashing round. Due to the fact that not the whole state is used, but only a certain part, it is impossible to obtain information about the connection between the input and output data.
HMQ1725/Updated Quark
It is also a rare mining algorithm that works with CPU and GPU. The HMQ1725 algorithm uses Quark, PIVX and ALQO coin algorithm. When Quark became available for ASICs, it became inefficient to mine on cards.
A modified version of this hash function is known as HMQ1725. It stands for "Highly Modified Quark1725", where the numbers 1725 indicate that 17 algorithms are used, which are hashed 25 times in a row. It is not ASIC resistant, but there are currently no ASICs or FPGAs for the HMQ1725 widely available. You can mine on a CPU, but you need to overclock it carefully. Also optimized for GeForce 10 series video cards and not as effective on AMD. Programs:
- CPU Miner: JayDDee/cpuminer-opt, CryptoCoderz/cpuminer-hmq1725,
- NVIDIA Miner: tpruvot/ccminer
- AMD Miner: CryptoCoderz/sgminer_HMQ1725
There are other algorithms, they are listed in the table below.