Nadezhda Zakharova 04/05/2018
Cryptocurrency mining is carried out in both legal and not entirely legal ways. Today there are so-called hidden miners who mine cryptocurrency using the computing power of others.
At the same time, the owner of a PC or other device may not even know that he has such malware installed.
The article talks about what hidden mining is, what risks it poses for computer owners, and how to detect malware and get rid of it.
What is shadow mining
The essence of this process is the extraction of cryptocurrency from someone else’s computer by a third party using special software.
In order to start extracting cryptocurrency from someone else’s computer, an attacker only needs to install special software there.
By the way, its functionality is rarely limited to mining alone.
Most often, there are related opportunities to steal important information, gain access to electronic wallets, and so on.
How do hidden miners usually get onto PCs?
First of all, through applications downloaded from the Internet or when viewing certain sites.
Most often, we are talking about downloading “warez” software, which also comes with a virus file as a “load”.
It usually unpacks itself and runs without the user's knowledge.
Therefore, the first precaution is to install a modern antivirus with the latest updates, which usually blocks the downloading of malicious files. However, as practice shows, this measure is not enough. But at least with it, the chances of malicious files being introduced are reduced.
Another option is to install the program directly. This is much more difficult to do, since it is necessary to obtain not virtual, but real access to the machine.
Finally, another option is to gain remote access to your PC. There are also certain difficulties here.
go
Eliminate RiskWare.BitCoinMiner from Windows
Remove RiskWare.BitCoinMiner from Windows XP:
- Click on start to open the menu.
- Select Control Panel and go to Installation and removal of programms.
- Select and Remove unwanted programs.
Remove RiskWare.BitCoinMiner from your Windows 7 and Vista:
- Open menu Start and select Control Panel.
- Go to Uninstall a program
- Right-click the unwanted application and select Uninstall .
Erase RiskWare.BitCoinMiner from Windows 8 and 8.1:
- Right click in the lower left corner and select Control Panel.
- Select uninstall a program and right-click on unwanted applications.
- Click the Remove .
How is hidden mining carried out?
To begin with, the attacker connects to one of the mining pools, since it makes no sense to mine cryptocurrency using one PC on your own.
Although some manage to create their own network by installing the software on many machines at the same time.
In this case, the chances of success increase significantly.
The main task of the software is the extraction of cryptocurrencies. All earned funds are transferred to the attacker’s account. At the same time, the virus can remain undetected for a long time, since not all anti-virus programs today are able to recognize such software.
The fact is that such a program, as noted above, usually ends up on the PC along with other files (for example, a downloaded game, movie, music or documents).
Installation is carried out in silent mode without user intervention.
And if this is a “hacked” (activated) program, then most often the user disables the antivirus altogether so that it skips the installation, thereby independently opening full access to his computer, even if temporarily.
go
Why is this dangerous?
The coin mining process is extremely intensive. This drains your computer's resources and leaves you with a sluggish and unresponsive PC. But discomfort is not the problem here. If you check your car now, you will notice that it is emitting heat. And heat is bad for your equipment. If your cooling system is not efficient enough, you will experience frequent system failures. This leads to data loss, Blue Screen of Death, and, in some rare cases, permanent hardware damage. There is one important thing to note here. Trojan.Bitcoinminer relentlessly exploits your CPU at high temperatures. Thus, the Trojan significantly shortens your CPU’s life. The longer this madness continues, the more worn out your processor will be. Also, let's not forget that terrible heat was once electricity. To run its malicious processes, Trojan.Bitcoinminer consumes a huge amount of electrical energy. Given enough time, this Trojan will double, even triple your electricity bill. I'm not kidding. The process of mining coins is only beneficial if you don’t use your own resources. Fraudsters are using yours. They make money into their own account! Beloved won't let this go on a minute longer. Take urgent action against Trojan. Clean up your computer forever!
What dangers does such software pose?
The main risks associated with the operation of such programs are technical. The fact is that an ordinary virus can harm the operating system.
Here the dangers lie primarily in the theft of personal information, as well as access to electronic wallets and other important programs, as well as websites.
As for the hidden miner, in addition to everything listed above, it also significantly loads the system. Especially the video card.
As a result, there are risks of reducing the service life of this board. In addition to the video card, hidden miners can harm other components.
In particular, this applies to the CPU, motherboard and power supply.
The biggest problem is that modern antivirus programs, as noted above, are mostly unable to recognize such software.
Accordingly, the user has to search for it independently. There are certain recommendations for this.
go
Characteristics of Bitcoin mining
“Mine” is an unconventional mine that is located on the Internet and mines electronic assets. Almost all users are familiar with the concepts of Bitcoin, Ethereum, crypto miner, etc.
Mining is the extraction of cryptocurrencies, of which there are now more than 200. The exchange rate of the main digital coins is constantly growing and experts predict the continuation of this trend. The popularity of cryptocurrencies is due to the high demand for virtual currencies.
The first cryptocurrency was Bitcoin. The principle of its extraction is reminiscent of the search for minerals such as gold. The greater the demand for digital coins, the higher their value. Not all miners receive Bitcoin. When there were fewer users on the network, the chances of receiving cryptocurrency increased. When the number of BTC miners began to increase, there were not enough coins for everyone. The fewer participants in the system, the more earnings.
Mining is the process of obtaining virtual gold from the depths of the Internet. The more powerful equipment a miner has with good video cards, the higher the chances of finding Bitcoins. The devices carry out mathematical calculations until one of the devices receives the encrypted BTC code.
To organize a small mining farm, a starting capital of at least 300-500 thousand rubles is required. The expenses will pay off only after 6-10 months.
Sometimes cryptocurrency miners combine their farms to increase their chances of making money. Income is divided equally among all participants.
Mining requires certain knowledge and experience. The equipment operates at maximum capacity. Cryptocurrency mining requires large amounts of electrical energy and time resources. This method of earning money has many nuances and requires large investments.
Bitcoin price is unstable. The rate is constantly rising and falling. This is influenced by members of the crypto community. Rich people have more power, so they can raise and lower the price of BTC.
Pros of Bitcoin
Bitcoin is not subordinate to the dollar, and each type of cryptocurrency is independent of each other. The popularity of Bitcoin is determined by the demand of people who are trying to mine or buy it. The cryptocurrency market is difficult to access, cannot be replicated, and is original.
Pros of Bitcoin:
- Decentralization of digital currency. BTC does not have a bank, so the coin cannot be counterfeited. It is also almost impossible to imitate transactions with the first cryptocurrency. But if you infiltrate the system itself, you will be able to carry out fraudulent schemes.
- Inability to track transactions performed using Bitcoin. A digital coin is an encrypted code, a genuine random set of characters. The cryptocurrency market that operates on this principle is absolutely unique.
Basic ways to detect botnets (hidden miner)
Given that antivirus software is powerless in this matter, users must determine the presence of malicious applications themselves.
This is not as easy to do as it might seem at first glance, but it is possible.
The first recommendation is to check the operation of the device under normal loads. Regular applications or even launching a browser are suitable for this. If there is a significant drop in performance, it is worth checking with an antivirus for the presence of standard viruses. If they are not found, Windows or a driver may require an update.
After this, an in-depth test is carried out with increasing load. This may require a game with high system requirements.
Then you can run AIDA64 to check the load on the video card and CPU before and after closing background programs.
Finally, all indicators are compared and appropriate conclusions are drawn.
Let's look at some points in more detail. One of the easiest ways for users who have discovered the possibility of the presence of a hidden miner is to reinstall the system and format the C drive.
However, this option is not suitable for everyone. There may be other important files stored on this drive that will be lost during formatting.
Although this option is the most reliable and simple . Today, even a novice user can install the same Windows by following the installer’s simple instructions.
Let's take a closer look at working with the AIDA64 application.
After launching the application, you need to enter the OSD and here note such items as the temperature of the video card and processor, their load level and RAM usage.
After applying the selected settings, a widget will appear on your desktop.
If the numbers are too high, you can try disabling everything that loads the CPU and video card and compare. If the readings remain high, a hidden miner is likely installed.
You can also use ProcessExplorer to determine what is loading the video card. Moreover, no additional settings are needed here.
The program works immediately after launch.
Another method is to check drive C for folders that are too large. The fact is that it is in them that the miner can hide. Moreover, the weight of such folders can reach several gigabytes. This is one of the easiest ways to detect this kind of software.
Sometimes you can find recommendations for detecting such a hidden program through the task manager.
However, modern stealth mining malware is configured in such a way that traces of its presence are hidden.
The software can disguise itself as ordinary programs used on a PC. Therefore, finding it is not so easy.
go
Virus miner - what is it? How do virus miners work?
In this article we will understand what a miner virus is (or a Trojan miner - what it is), how it works and what signs it has.
Stealth mining malware ( miner viruses ) refers to a category of malicious code designed to exploit the processing power of an unsuspecting user's device for the purpose of mining cryptocurrency.
The miner virus resembles a Trojan horse. The virus enters the system and begins to consume computer resources, loading the processor or video card up to 100% in order to generate income for the attacker.
Why is he dangerous?
At first glance, the miner seems like a harmless virus. This is a virus that, in fact, does not harm the computer in any way, but only secretly uses its resources.
Someone makes money from you, and it’s as if you yourself are not losing anything from this. But it is not so.
A miner virus that has penetrated a PC places a heavy load on its components and causes overheating, which can damage the components of the computer.
Mining uses hardware components: a processor, RAM and, most importantly, a video card, where all calculations take place. The more these components are loaded, the hotter they become. Excessive load causes overheating, and overheating causes component failure. In the best case, the presence of a miner virus will negatively affect the performance of the computer, for example, it will reduce FPS in games (the number of frames per second).
How hackers hide mining
The easiest way to hide the operation of a mining program is to run it in the background as a service process. Most users will not see that a disguised program has started running on the computer; the problem can only be detected by indirect signs, for example, guessing by the fact that the equipment has begun to slow down and work more slowly.
An advanced program for hidden mining can automatically pause its work when trying to detect it, for example, when starting the task manager in the Windows operating system. Serious programs can adapt the loading of computing resources so that their impact on the overall operation of the computer is not so noticeable, pose as completely legitimate programs from the user’s point of view, embed themselves in frequently used programs, and also use a host of other methods in order not to arouse suspicion.
The main problems in detecting such software
One of the problems is that hidden miners can be embedded not only in sites with pirated software, but also in advertising on YouTube.
Cybersecurity specialist Troy Marsh first spoke about this problem. Many users complained that a special script used up to 80% of their PC power to mine the Monero cryptocurrency.
Another example is favicon creation sites. These small images are used by webmasters to be unique in a browser tab to make it easier for the user to navigate between bookmarks.
In 2022, reports emerged that a hidden miner was in the code of a site that created such pictures. Naturally, all webmasters add them to their sites. Accordingly, miners appear on them.
The main problem is that such resources are trusted by users and the latter are unlikely to suspect that suspicious software could have come from there.
go
Remove RiskWare.BitCoinMiner from your browsers
RiskWare.BitCoinMiner Removal from Internet Explorer
- Click on the gear icon and select Internet Options .
- Go to the tab Additionally and press the button Reset.
- Check, Delete personal settings and click Reset .
- Click Close and click OK .
- Come back to gear icon, choose add-ons → toolbars and extensionsand remove unwanted extensions.
- Go to Search Providers and select your new default search engine
Erase RiskWare.BitCoinMiner from Mozilla Firefox
- In field URL enter "about:addons».
- Go to extensions and remove suspicious browser extensions
- Press menu, press the button with question mark and open Firefox help. Press Firefox Refresh button and select Update Firefox for confirmation.
Stop RiskWare.BitCoinMiner from Chrome
- IN "chrome://extensions» enter in the field URL and press Enter.
- Stop untrusted browser extensions
- Restart Google Chrome.
- Open the Chrome menu, click Settings → Show advanced options, select Reset browser settings, and click Reset (optional).
- Download MalwareBytes
- Download Plumbytes
- Download Spyhunter
Removal
To delete it, it is not enough to simply detect a suspiciously large file or folder.
Therefore, it is better to install anti-virus programs (some experts recommend the portable version, since viruses can block the installation of anti-virus software, which is often the case).
It is best to carry out the cleaning procedure in a safe mode. In this case, the chances that malware will be able to block the operation of the antivirus are minimal.
At this stage, it is important to remove not only and not so much the hidden miner, but the program that installed it. Because if the miner is destroyed, the same application will be able to restore it after some time.
After checking the system with various antiviruses and clearing everything suspicious, you need to pay attention to whether the suspicious processes that were detected earlier continue to work. If we are talking about some strange large folder, you can try rebooting the operating system several times and see if this folder appears again.
The main task at this stage is not only to remove causes and effects, but also to make sure that we are talking about the virus that the miner installed.
The fact is that modern hackers are well aware of exactly what methods users will try to clean their computer.
Accordingly, they strive in every possible way to hide the traces of the miners and the installer.
It is possible that no measure helps. The antivirus cannot detect the malware.
Then it is better to contact specialists, or simply reinstall the system, as mentioned above. If drive C is formatted, the malware along with the miner will be deleted.
In this case, it is important to make sure that there are no important programs or documents left on drive C. Because during the formatting process they will all be deleted.
Behavior of a miner on a computer
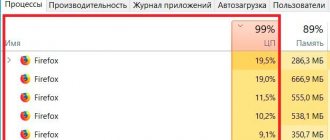
A miner often has basic signs that can be easily identified - most likely there is a virus-miner in the system, so here are the signs:
- You start your PC. Some process begins to load the system, sometimes using a lot of RAM.
- You open the dispatcher. It happens that a process uses a fixed percentage of productivity. But sometimes the load is 100%. And so on continuously until the process is completed.
- And it also happens that you open the dispatcher, but there is no load. The PC is fast. The dispatcher was closed - the computer was slow. Did you guess it? Advanced modifications of miners detect the opening of the dispatcher and immediately complete their work, pranksters)) Autoload analysis will help here to find out where this dirty trick is launched from... places can be: registry, task scheduler, services.
- There was a case of a miner virus in the form of a Google Chrome browser extension. As a result, the browser constantly loaded the computer.
- Miners often have protection. We completed the process and it appeared again. We deleted the process file - after a reboot everything was restored.
But there is also an advantage of miners - they often do not steal any passwords or logins from the PC, they have another goal - to use the power of your computer.
Example of a miner process:
In fact, it may not be a virus, but just mining software. But the mining process is impossible without loading the processor or video card, this is its distinctive feature. Therefore, if the virus is a miner, then it will definitely load the computer mercilessly.
Preventive measures
The arrival of malware with a hidden miner is the first signal that the user should reconsider the sites he visits.
As noted above, most often viruses come precisely in the process of downloading some kind of pirated content (torrents, shares, etc.), as well as when visiting dubious sites (online films, porn, game projects).
The virus can also enter through hacked instant messengers and even social networks. One of the latest trends is to hack a Skype account and send a link through it to all users who are in the contact list.
The latter, in turn, follow the link and receive the virus on their PC.
Antivirus software can be used as a preventive measure. Some hidden miners are launched through standard viruses.
Accordingly, such software will be able to detect and neutralize them, sometimes even at the stage of attempting to write to a PC.
As for downloading content, it is better to refuse it altogether. Especially if you have a Bitcoin wallet installed. If a virus gets in, the data from it, including private keys during transactions, can fall into the hands of an attacker.
It is advisable to store cryptocurrency either on a hardware or paper wallet. Hot ones are not suitable, since private keys are stored directly on the hard drive and similar malicious software can access them.
go
How to start mining cryptocurrencies
You can mine digital coins honestly. To start such an activity, you need to familiarize yourself with some nuances in advance.
You might like this article about setting up a mining rig from scratch
What questions need to be resolved before starting mining:
How much money is available for initial investment (minimum amount is $1,000); What equipment and servers will be used; Approximately how much electricity will be consumed?
It is important to determine in advance what affects the mining speed and what the power is. Speed is determined by power, which is measured by a certain number of hashrate (Hashrate) on a specific algorithm.
Mining on someone else's hump: how attackers use computers
Wherever there are rules, there are those who break them. And the world of cryptocurrencies is no exception. Some miners do not pay for electricity by running a cable to a transformer; others smuggle video cards from China.
But most often, cryptocurrency miners use other people’s computers. In particular, in September of this year, Kaspersky Lab discovered two large networks of computers engaged in cryptocurrency mining. One network has approximately 4,000 units of equipment, the other - 5,000. As it turned out, all of them were infected with a virus, and the owners of the equipment did not even suspect that they were participating in the extraction of digital currency, helping the creators of the virus earn tens of thousands of dollars every month.
Typically, the cryptocurrencies Litecoin, Feathercoin and Monero are mined in the process of black mining. Their extraction does not require high-power equipment, and coins can be mined from ordinary home computers.