Cryptocurrency algorithms
Each cryptocurrency uses its own encryption algorithm. However, the number of coins greatly exceeds the number of cryptocurrency algorithms, so some cryptocurrencies use the same data hashing algorithm.
Below we will take a closer look at the most popular cryptocurrency encryption algorithms, as well as the coins that work on them.
- What is a cryptocurrency algorithm
- SHA-256 Features
- SHA-256 coins
- Peculiarities
- Peculiarities
- Peculiarities
- X11 coins
- Peculiarities
What is a cryptocurrency algorithm
Cryptocurrency encryption algorithms
Cryptocurrency algorithms
is a set of specific cryptographic mechanisms and rules that encrypt digital currency. Miners use special equipment to decipher the algorithm of a specific cryptocurrency - this process involves searching for a hash.
As soon as the correct hash is found, a new block is generated in the blockchain, which stores information about transactions, the hash of the previous block, the amount of reward received by the miner, etc.
☝️
The process of decryption (coin mining) turns a set of random data into ordered, systematized information, which is subsequently recorded on the blockchain.
Today, there are several dozen cryptocurrency algorithms, but only a few of them are popular.
Among the popular ones are the following: SHA-256, EtHash, Scrypt, X11, CryptoNight, EquiHash, X13, Quark, NeoScrypt.
Below is a summary table of cryptocurrency algorithms for the most popular coins:
Encryption algorithms and cryptocurrencies
conclusions
Mining on Scrypt is not particularly different from other types of mining. This algorithm is used by a number of altcoins. Of these, Litecoin is the most famous. Other coins have not gained much popularity and, as a result, cannot boast of a high exchange rate.
But with the advent of ASIC devices for Scrypt, even mining LTC looks like a controversial idea. When mining on a video card, the user has little chance of simply getting back the investment. You can make money with ASIC, but the amount will be much lower than Bitcoin and Ethereum.
Using cloud mining is also not a good idea. Litecoin mining contracts are not available on HashFlare and Genesis Mining. In the case of Nicehash, everything depends on the order. Of course, you can mine not only LTC, but also other coins. But their rate often does not exceed $0.10, which turns mining into an expensive hobby.
Equihash
Anonymous cryptocurrency algorithm Equihash
Equihash
is an anonymous cryptocurrency algorithm that was released in 2016. The first cryptocurrency to use Equihash as a base was Zcash. Block creation takes 150 seconds and hashrate is measured in Megahash per second (MH/s). This algorithm is based on a hash function, which is built on the principle of the “Birthday Paradox” - this is a mathematical pattern that is used to calculate probability. The rule says:
If there are 23 people in a room, there is a 50% chance that at least two of them have the same birthday. Based on this pattern, the probability of finding a nonce during the mining process is 2, raised to the power N and divided by 2.
Peculiarities
This cryptocurrency algorithm was developed by Alexander Biryukov and Dmitry Khovratovich, scientists at the University of Luxembourg who are part of the CryptoLUX research group. In 2016, the development was presented to a wide range of people.
☝️
Equihash is demanding on the amount of RAM, and not on the processing speed of mathematical calculations.
This makes mining “AI-resistant” and the network more decentralized. For mining cryptocurrencies running on Equihash, video cards with a minimum memory capacity of 2 GB
. The best results were shown by using NVidia brand GPUs.
However, ASIC devices have also been developed for Equihash mining. Today, the most popular are two models: Antminer Z9 mini from Bitmain and A9 ZMaster from the lesser-known company Innosilicon. Unlike the Monero team, the Zcash developers did not take any action to protect their cryptocurrency from centralized mining, but only expressed their disappointment.
We recommend an interesting video about mining using the Equihash algorithm:
Mining using the Equihash algorithm
Equihash Algorithm Coins
Cryptocurrencies of the Equihash algorithm
The most popular cryptocurrencies operating on the Equihash algorithm:
Zcash (ZEC).
Bitcoin Gold (BTG).
Komodo (KMD).
ZClassic (ZCL).
ZenCash (ZEN).
Bitcoin Private (BTCP).
How to start mining solo?
First, download the wallet application for the currency we need from the official web resource of the project. Let's activate it. Then we wait until the synchronization process ends. After this, you can safely close it.
Next, you need to follow the path “appdata\name of your cryptocurrency” (for example, in seven: “C:\Users\username\AppData\Roaming\name of currency”). Then you need to create a test file where you need to specify several commands (written depending on the crypto money being mined). Save it and change the name to “selected cryptocurrency.conf” (simply enter conf instead of the txt extension).
Activate the wallet. Again we see the synchronization process. After its completion, we configure the application. If any errors occur, you need to check port 9344. It may be closed and then it should be opened.
If the mining of cryptographic coins has begun, it is normal that there will be no messages about the various shares in the application interface. All that remains is to wait for the block to be generated. Each earned block will be available after 120 confirmations. You can easily control this process in the wallet window. By the way, you cannot close it during mining, otherwise it will simply be interrupted.
When working on other devices, we write the address of the PC with the account as the IP address, which is also the server. To calculate the chance of receiving a block, you need to turn to special platforms. There you need to indicate your power, then it will show you the amount of cryptocurrency per hour.
Scrypt
Scrypt
cryptocurrency blockchain
is a cryptocurrency mining algorithm that used to be of interest to many solo miners due to its resistance to the so-called “hardware attack”. The speed of creating blocks in a blockchain based on Scrypt is about 30 seconds. The hashrate, like Ethash, is measured in Megahash per second (MH/s). Scrypt primarily became popular due to its use in the Litecoin cryptocurrency.
Peculiarities
The history of the creation of this algorithm began with the fact that it soon became clear that Bitcoin mining was very easy to monopolize, due to the fact that the simplicity of the SHA-256 function allows you to automate the mining process.
Therefore, the main task when creating Scrypt was to complicate the block generation mechanism due to increased requirements for resources used for computing operations. In particular, the amount of RAM is critical (as in Ethash), while the power consumption and processing power requirements are much lower than in the case of SHA-256.
Initially, central and graphic processors were used to mine Scrypt-based cryptocurrencies, but the algorithm could not withstand mining corporations and in 2014 the first ASIC for Scrypt coins was created.
In response, crypto enthusiasts created an improved algorithm called Scrypt-N, which was first used in the Vertcoin coin. It differs in that the requirements for RAM are constantly growing.
From the video below you will learn how the Scrypt algorithm came into being:
Scrypt algorithm
Scrypt algorithm coins
The Scrypt mining algorithm is the basis for the operation of the following cryptocurrencies:
Litecoin (LTC).
Dogecoin (DOGE).
Redcoin (RED).
Monacoin (MONA).
Viacoin (VIA).
Syscoin (SYS).
Farm Remote Control Method
In an OS like Windows, it will not be possible to use the remote desktop to monitor and control farms, since it operates with its own virtual video card. Having interrupted the extraction of currency, you will not be able to start it again, because the devices will not be displayed correctly. You need to use specialized applications like TeamViewer. For other operating systems, lightGDM does not allow you to monitor video card parameters through remote commands. Everything works fine with GDM.
X11 algorithm
X11
mining algorithm
is an encryption algorithm that uses eleven functions instead of one. This means that this technology can provide a high degree of security, because in order to harm the system, an attacker would have to hack all 11 functions, and this is very unlikely, because the changes made will be visible after hacking the first function, and developers will have plenty of time to protect the system , before the hacker gets to the eleventh function. The X11 cryptocurrency algorithm was created specifically for Dash mining.
Setting up CGMINER
The current version of the client that supports currency mining using the Scrypt protocol is 3.7.2. It is easy to download on the official website of the developers. After installing the application, you need to activate 2 commands in the operating system console. Then create a batik file in the program folder, adding a specific script there. All that remains is to launch it.
CryptoNight
Mining on CryptoNight
CryptoNight
is an algorithm for anonymous cryptocurrencies, which is based on technologies such as ring signatures and disposable addresses. It became primarily known for its cryptocurrency Monero (XMR). Generating a block takes about 60 seconds.
Peculiarities
Using CryptoNight allows you to create a confidential, secure and fungible digital currency. These properties are achieved through the use of the CryptoNote protocol, which was created in 2012 by a blockchain developer (or group of developers) under the pseudonym Nicholas van Saberhagen. It is still unknown who is hiding behind this name.
The high degree of anonymity of the CryptoNight algorithm is achieved through the use of two technologies:
- Ring signatures (encrypt the sender);
- One-time addresses (encrypt the recipient).
Due to the fact that transactions are completely anonymous, all coins built on the CryptoNight cryptocurrency algorithm are interchangeable.
This means that they do not have a “dark past”, like, for example, Bitcoin, the blockchain of which allows you to track the movement of a certain coin and its participation in “dirty deeds”.
Blockchain Explorer
Another very important feature of this algorithm is that for mining the most effective way is to use a CPU paired with a GPU, although mining only on a central processor also gives positive results. On the contrary, the use of ASIC devices is economically unprofitable.
The secret is that CryptoNight is demanding on RAM (at least 2 GB is needed for proper operation), and not on the speed of mathematical calculations, which is what ASIC miners are strong at.
The process of finding the correct nonce to generate a block is that CryptoNight creates random blocks that are stored in the memory of the computing device, rather than sending continuous frequent calls to the miner in order to perform mathematical operations, as happens in the case of the SHA-256 algorithm (used for Bitcoin).
This allows you to build a more decentralized network and prevent a situation where more than half of the hashrate belongs to one node, and there is a high probability of a 51% attack.
☝️
To effectively mine cryptocurrencies based on CryptoNight, it is worth using Intel Core central processors of the i5 and i7 generations.
The use of Radeon HD brand equipment (new models) also shows good results. In addition, ASIC miners can be used to mine CryptoNight-based cryptocurrencies.
☝️
At the moment, the following models are suitable for this: Antminer X3, Baikal Giant-N, PinIdea RR-200, DragonMint X1/X2.
However, it is worth noting that Monero makes protocol changes every year that help protect the coin from ASIC mining. But other coins running on CryptoNight, for example, Bytecoin, Aeon, are mined without problems using ASIC.
You can learn more about how anonymous coins work by watching the video below:
Anonymous cryptocurrencies
Problem with displaying video cards
There are many reasons why this happens. In some cases, disabling the CrossFireX option helps. Thus, on ancient versions of drivers it was possible to mine only with jumpers that created the appearance of a monitor. If this function has nothing to do with it, you should go to the screen characteristics and enlarge the image on all devices. In a situation where this does not work, you need to try to exclude the video card from the list of equipment, and then allow it to be determined again.
Important! It happens that the card ends up in “hidden devices”, which means that before deleting it, you need to turn on its display. To do this, go to the properties of “My Computer”. There we go to the “Advanced” tab and at the very bottom click “Environment Variables”. Next, depending on the operating system, we enter a number of commands. Finally, launch the device manager, then go to the “View” tab and activate the display of hidden devices.
HMQ1725/Updated Quark
It is also a rare mining algorithm that works with CPU and GPU. The HMQ1725 algorithm uses Quark, PIVX and ALQO coin algorithm. When Quark became available for ASICs, it became inefficient to mine on cards.
A modified version of this hash function is known as HMQ1725. It stands for "Highly Modified Quark1725", where the numbers 1725 indicate that 17 algorithms are used, which are hashed 25 times in a row. It is not ASIC resistant, but there are currently no ASICs or FPGAs for the HMQ1725 widely available. You can mine on a CPU, but you need to overclock it carefully. Also optimized for GeForce 10 series video cards and not as effective on AMD. Programs:
- CPU Miner: JayDDee/cpuminer-opt, CryptoCoderz/cpuminer-hmq1725,
- NVIDIA Miner: tpruvot/ccminer
- AMD Miner: CryptoCoderz/sgminer_HMQ1725
There are other algorithms, they are listed in the table below.
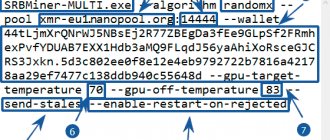
Ethash Dagger-Hashimoto
Etash is a proof-of-work for coins based on Ethereum, which also initially struggled with centralization. Intensively uses device memory. The latest version of Dagger-Hashimoto has changed many of the original features. The algorithm works according to the following principle:
- there is a seed that can be calculated for each block by scanning the block headers up to a certain point,
- from the seed you can calculate a pseudo-random cache of 16 MB. Light clients store cache.
- From this, a 1 GB dataset can be created, with the property that each element in the set depends on a small number of elements from the cache. Full clients and miners store a data set that grows linearly over time.
- Mining involves capturing random pieces of a data set and combining them. The large data set is updated once every 30,000 blocks.
Works well with AMD cards such as RX 470, 480, 570 and 580 and gives good returns. Coins: Ethereum, Ethereum Classic, Musicoin, Ellaism.
How to mine ELLA