Cryptocurrency algorithms
Each cryptocurrency uses its own encryption algorithm. However, the number of coins greatly exceeds the number of cryptocurrency algorithms, so some cryptocurrencies use the same data hashing algorithm.
Below we will take a closer look at the most popular cryptocurrency encryption algorithms, as well as the coins that work on them.
- What is a cryptocurrency algorithm
- SHA-256 Features
- SHA-256 coins
- Peculiarities
- Peculiarities
- Peculiarities
- X11 coins
- Peculiarities
What is a cryptocurrency algorithm
Cryptocurrency encryption algorithms
Cryptocurrency algorithms
is a set of specific cryptographic mechanisms and rules that encrypt digital currency. Miners use special equipment to decipher the algorithm of a specific cryptocurrency - this process involves searching for a hash.
As soon as the correct hash is found, a new block is generated in the blockchain, which stores information about transactions, the hash of the previous block, the amount of reward received by the miner, etc.
☝️
The process of decryption (coin mining) turns a set of random data into ordered, systematized information, which is subsequently recorded on the blockchain.
Today, there are several dozen cryptocurrency algorithms, but only a few of them are popular.
Among the popular ones are the following: SHA-256, EtHash, Scrypt, X11, CryptoNight, EquiHash, X13, Quark, NeoScrypt.
Below is a summary table of cryptocurrency algorithms for the most popular coins:
Encryption algorithms and cryptocurrencies
Problem solving
The program does not start or closes after some time
Solution:
Make sure you fill out the configuration files and the program .bat file correctly. Even if you missed a comma or parenthesis somewhere, the program may not start. The syntax must be correct as in the examples above.
ERROR : PARSE error: Target length abnormal
The wallet or Payment ID is incorrect. Some pools do not accept Payment ID, so you need to write without it.
Connection to pool lost. Reconnecting in n seconds.
The connection to the server has been lost. Reasons may be:
- on your internet connection
- on the pool side
- you entered the pool address or port incorrectly
Error. Could not login user to pool, trying again.
The worker cannot login to the pool.
It often happens that you have incorrectly specified the digital wallet address and Payment Id, if required.
If you still have difficulties launching, write to us in the comments - we will help!
Equihash
Anonymous cryptocurrency algorithm Equihash
Equihash
is an anonymous cryptocurrency algorithm that was released in 2016. The first cryptocurrency to use Equihash as a base was Zcash. Block creation takes 150 seconds and hashrate is measured in Megahash per second (MH/s). This algorithm is based on a hash function, which is built on the principle of the “Birthday Paradox” - this is a mathematical pattern that is used to calculate probability. The rule says:
If there are 23 people in a room, there is a 50% chance that at least two of them have the same birthday. Based on this pattern, the probability of finding a nonce during the mining process is 2, raised to the power N and divided by 2.
Peculiarities
This cryptocurrency algorithm was developed by Alexander Biryukov and Dmitry Khovratovich, scientists at the University of Luxembourg who are part of the CryptoLUX research group. In 2016, the development was presented to a wide range of people.
☝️
Equihash is demanding on the amount of RAM, and not on the processing speed of mathematical calculations.
This makes mining “AI-resistant” and the network more decentralized. For mining cryptocurrencies running on Equihash, video cards with a minimum memory capacity of 2 GB
. The best results were shown by using NVidia brand GPUs.
However, ASIC devices have also been developed for Equihash mining. Today, the most popular are two models: Antminer Z9 mini from Bitmain and A9 ZMaster from the lesser-known company Innosilicon. Unlike the Monero team, the Zcash developers did not take any action to protect their cryptocurrency from centralized mining, but only expressed their disappointment.
We recommend an interesting video about mining using the Equihash algorithm:
Mining using the Equihash algorithm
Equihash Algorithm Coins
Cryptocurrencies of the Equihash algorithm
The most popular cryptocurrencies operating on the Equihash algorithm:
Zcash (ZEC).
Bitcoin Gold (BTG).
Komodo (KMD).
ZClassic (ZCL).
ZenCash (ZEN).
Bitcoin Private (BTCP).
Fine tuning
Setting up each card separately
To manually configure video cards individually, you need to create a "gpu_conf" array in the config.txt files.
Example:
"gpu_conf" : [ { "id" : 0, "intensity" : 50, "worksize" : 4, "threads" : 1}, { "id" : 1, "intensity" : 45, "worksize" : 4, "threads" : 2}, { "id" : 2, "intensity" : 40, "worksize" : 8, "threads" : 2}, { "id" : 3, "intensity" : 55, "worksize" : 8, "threads" : 2} ]
Here we can specify the intensity and other settings for each video card separately.
Important. If you use the settings for each card separately, then you must specify the parameters for each video card. If you specify one line { "id" : 0, "intensity" : 50, "worksize" : 4, "threads" : 1}, then only one video card will work.
To find out the ID of the video card, you need to specify the key -listdevices in the batch file.
Setting the intensity
To get the maximum hashrate in the miner, you need to adjust the intensity and overclocking of each video card separately.
To do this, you need to stop the miner, then increase the intensity by 1 unit, save the configurations and run the program again.
Next, we look at the hashrate indicators. If it has grown and the system works stably for at least 15 minutes, you can try increasing the intensity again.
You can increase the intensity until your hashrate begins to decrease, or the program begins to freeze with an error:
Error CL_INVALID_BUFFER_SIZE when calling clCreateBuffer to create hash scratchpads buffer.
If we get this error, we reduce the intensity by one unit and try to run the program again.
Once we are sure that we have found our maximum for all video cards, we can move on to overclocking the cards.
Pool setup
In this program, pools are configured as in the .bat file, but you can configure them in pools.txt files. Then the batch file contains only a link to the pool configuration file that the program will read.
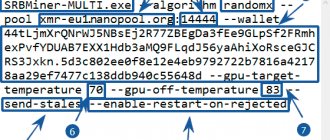
Example:
example of pool setup for Monero
- xmr-eu1.nanopool.org — Pool address
- 14444 - pool port
- 4ALcw9nTAStZSshoWVUJakZ6tLwTDhixhQUQNJkCn4t3fG3MMK19WZM44HnQRvjqmz4LkkA8t565v7iBwQXx2r34HNroSAZ - your digital wallet address
- a1aa5367a9df423eb5ebac05b82db41a192d35b077b44e29a1aa620985146650 — Paiment ID address. Indicated through a dot.
- rig1 — the name of your farm.
The file syntax is as follows: Specify “pool” : “pool address:port”, “wallet” : “wallet.payment-id”, “password” : “password”
It is important to follow the syntax: all colons, quotes and commas.
After the general configuration and the pool configuration are configured, you can proceed to launching the miner via the .bat file.
Scrypt
Scrypt
cryptocurrency blockchain
is a cryptocurrency mining algorithm that used to be of interest to many solo miners due to its resistance to the so-called “hardware attack”. The speed of creating blocks in a blockchain based on Scrypt is about 30 seconds. The hashrate, like Ethash, is measured in Megahash per second (MH/s). Scrypt primarily became popular due to its use in the Litecoin cryptocurrency.
Peculiarities
The history of the creation of this algorithm began with the fact that it soon became clear that Bitcoin mining was very easy to monopolize, due to the fact that the simplicity of the SHA-256 function allows you to automate the mining process.
Therefore, the main task when creating Scrypt was to complicate the block generation mechanism due to increased requirements for resources used for computing operations. In particular, the amount of RAM is critical (as in Ethash), while the power consumption and processing power requirements are much lower than in the case of SHA-256.
Initially, central and graphic processors were used to mine Scrypt-based cryptocurrencies, but the algorithm could not withstand mining corporations and in 2014 the first ASIC for Scrypt coins was created.
In response, crypto enthusiasts created an improved algorithm called Scrypt-N, which was first used in the Vertcoin coin. It differs in that the requirements for RAM are constantly growing.
From the video below you will learn how the Scrypt algorithm came into being:
Scrypt algorithm
Scrypt algorithm coins
The Scrypt mining algorithm is the basis for the operation of the following cryptocurrencies:
Litecoin (LTC).
Dogecoin (DOGE).
Redcoin (RED).
Monacoin (MONA).
Viacoin (VIA).
Syscoin (SYS).
Setting up a miner for Monero
Let's take a step-by-step look at how to set up a program for mining Monero coins. You can download ready-made files at the end of the article.
Setting up via body file
We will launch the program traditionally through a .bat file.
Let's look at setting up the .bat file in more detail:
Example of setting up a batch file
- SRBMiner-CN.exe is the name of the program that will be launched. This file must be in the folder with the program and have exactly this name
- -ccryptonighttype normalv4 — specify the algorithm of the mined coin
- —cpool xmr-eu.dwarfpool.com — after the —cpool key we write the pool address
- 8050 - after the colon we indicate the port
- —cwallet 4ALcw9nTAStZSshoWVUJakZ6tLwTDhixhQUQNJkCn4t3fG3MMK19WZM44HnQRvjqmz4LkkA8t565v7iBwQXx2r34HNroSAZ.5c01d3dd96ac8e1e4de53c736fd42a5f793d 6ede4fb776f2a186a84dba44f3e8 - cwallet - this is the number of your digital wallet. You can specify Payment Id through the dot.
- —config Config\config-normalv4.txt — specify the path to the configuration file. It is located in the Config folder and is named config-normalv4
- .rig1 - we also indicate the farm identifier separated by a dot. This is necessary to track statistics on the pool
This completes the basic setup of the program. But if you want to earn more, then you need to adjust your performance.
Pay close attention to the syntax of the .bat file. No mistakes are allowed. All colons, spaces, hyphens, etc. must be observed.
Don't forget to set a sufficient size of the swap file! How to calculate which paging file is needed?
Windows swap file = number of cards * amount of card memory + 2
Example: 6x RX with 8 GB = 6 * 8 + 2 = 50 - so set it to 50000 min/max
Overclocking options
To mine Monero, we used the following overclocking settings in MSI Afterburner:
Rx570: Core clock: 1230 MHz, Memory: 1950 Rx560: Core clock: 1167 MHz, Memory: 1950 Rx550: Core clock: 1167 MHz, Memory: 1920 Rx Vega56: Core clock: 1408 MHz, Memory: 945
The farm operates stably with these indicators. Doesn't freeze or reboot.
Commands that affect performance:
--setcomputemode sets the calculation mode and disables crossfire - run as administrator
--resetvega disable/enable Vega graphics cards before mining (improves performance)
Stability and watchdog:
--gpuwatchdogdisablemode if enabled, the watchdog will try to disable the failing video card instead of restarting the entire miner
--disablestartupmonitor disable the watchdog timer for the miner startup interval
--disablegpuwatchdog disable the watchdog
--gpuerrorsalert notify when the number of calculation errors for any video card reaches this value
—maxstartuptime value (maximum time to initialize gpu and start mining, minimum - 10 seconds, maximum - 10 minutes, default - 2 minutes)
--maxstartuptimescript "filename" (run this script if maxstartuptime is exceeded)
--forcedshutdown never try to free resources on reboot/shutdown
Working with devices:
--listdevices display a list of available devices
--listdevicesreordered display a list of available devices ordered by busid
--gpureorder order devices by busid
--adldisable disable ADL
--resetfans resets fans to default settings when exiting the program
--enableduplicategpuid allows the same gpu id to be used multiple times in gpu_conf
Changing algorithms:
—usealgoswitching use the miner in algorithm switching mode—the pool must support it
--usealgomapping (value) type of algorithm mappings to use: 1-short, 2-long, low
—algoswitchmintime (value) minimum time for mining using the same algorithm, in seconds, min 3 minutes, def. 10 min. - The pool must support it
--benchmarkalgos test all algorithms installed in algos.txt and save the results
--resetmineronalgoswitch if used, the miner will be restarted every time the algorithm is switched
Connect third-party files:
--startupscript (filename) run a custom batch script before starting mining
--config (filename) use a configuration file other than config.txt
--pools (filename) use a pool file other than pools.txt
--algos (filename) use the algos file except algos.txt
--logfile (filename) enable logging to file
Other settings:
--sendallstales send every expired share to the pool (may increase the number of rejected shares)
--setup run setup mode to create main configuration files
--nocache do not save compiled binaries to disk
Working with the program API:
--apirigrestarturl
--apiminerrestarturl
--apirigshutdownurl
Arguments only BEFORE version 1.7.6:
--runbenchmark compare current settings settings offline
—benchmarkduration duration of test execution in seconds, max — 3 minutes, def — 1 minute.
X11 algorithm
X11
mining algorithm
is an encryption algorithm that uses eleven functions instead of one. This means that this technology can provide a high degree of security, because in order to harm the system, an attacker would have to hack all 11 functions, and this is very unlikely, because the changes made will be visible after hacking the first function, and developers will have plenty of time to protect the system , before the hacker gets to the eleventh function. The X11 cryptocurrency algorithm was created specifically for Dash mining.
Table of the most popular cryptocurrency algorithms
| Algorithm | Cryptocurrency |
| SHA-256 | Bitcoin, Bitcoin Cash, EOS, Steem, Litecoin Cash |
| Ethash | Ethereum, Ethereum Classic |
| Scrypt | Litecoin |
| CryptoNight | Monero, Bytecoin, Electroneum, CryptoNoteCoin, DarkNetCoin |
| X11 | Dash |
| Equihash | Zcash, Bitcoin Gold, Komodo, ZClassic, ZenCash, Bitcoin Private |
| ProgPow | Bitcoin Interest, Veil, Zano, EtherCore, Super Zero, Epic Cash |
| Quark | Quark, Amsterdam Coin, Darknet, BiosCrypto, Dimecoin |
SHA-256 algorithm
Secure Hash Algorithm is a secure hashing algorithm that appeared in 2001. The number indicates the size of the numbers – 256 bits. The US NSA is responsible for developing the algorithm. The original idea was to provide a high level of confidentiality in the TLS, SSL, SSH and PGP protocols. In 2003, scientists Gilbert and Handstuck confirmed the security of the algorithm. Later, in 2008, researchers from India found collisions - different messages with the same hash. In September of the same year, they presented a more secure method for constructing the algorithm.
The NSA's work was used by Satoshi Nakamoto to ensure anonymity in the Bitcoin network, which was launched on January 3, 2009. Since cryptocurrency is open source, it has often been used to create other digital coins. However, the main disadvantage of SHA-256 is that it is slower. Because of this, coins using other algorithms began to appear.
SHA-256 has found application not only in cryptocurrencies. Today it is used:
- OpenLab - password hashes;
- DNSSEC – DNSKEY digests in the DNSSEC protocol;
- X.509, DSA and PGP – creation of an electronic digital signature;
- IPSec – support in ESP and IKE protocols.
Previously, an ordinary personal computer was suitable for efficient mining on SHA-256. However, over time, the network hashrate began to increase rapidly, which is why the profitability of cryptocurrency mining in this way began to fall. The situation got worse with the advent of ASIC - now, due to the peculiarities of the SHA-256 algorithm, it makes sense to mine BTC only using special equipment. From that moment on, an “arms race” began, as new, more powerful models appear almost every year.
Ethash Algorithm
Ethash is an updated version of the Dagger Hashimoto algorithm, which was obtained by combining Hashimoto Thaddeus Dryja and Dagger. The latter was developed by Vitalik Buterin. The developers of the algorithm set themselves the following goals:
- make it more difficult to create ASICs;
- ensure easy client verification;
- provide complete storage of the block chain.
Despite attempts to make ASIC production more difficult, in 2022 Bitmain announced the creation of specialized equipment for Ethereum mining. This situation did not suit the Ethereum developers, and they announced briquetting. The network can be updated at any time, due to which ASIC will stop bringing in money. Later, the developers announced a transition to POS - this will make further ASIC production pointless.
In current conditions, video cards are best suited for mining Ethash-based coins. During mining, a DAG file is loaded into the video card memory. The size of this document is gradually increasing. The file weight has already exceeded 4 GB
.
For mining you must have video cards with a memory capacity of 6 GB
. However, in a few years it will also cease to be profitable.
Another cryptocurrency, Ethereum Classic, also faced the problem of increasing the DAG file. When the document weight approaches 3.96 GB
, the developers decided to update the algorithm and reduce the file size to
2.5 GB
. Otherwise, due to the low popularity of the network, there was a risk that the bulk of the hashrate would go to a small group of individuals.
Scrypt algorithm
Scrypt gained popularity after the emergence of Litecoin. However, the author of the algorithm is not the creator of the cryptocurrency, Charles Lee, but FreeBSD security officer Colin Percival. The developer tried to protect the algorithm from ASIC actions. To compute functions, the algorithm requires a significant amount of random access memory. The end result is that Litecoin is more flexible than Bitcoin.
For mining cryptocurrencies based on Scrypt, a central and graphic processor are suitable. However, it is believed that video cards are better at mining coins due to greater performance. Due to the low cost, most miners prefer cards from AMD. However, despite the attempts of developers to protect cryptocurrency from specialized equipment, there are several effective ASIC options on the market, so mining LTC using video cards has become less profitable.
As a solution to the problem, a modernized variation of the Scrypt-N algorithm appeared. Its difference lies in the constant increase in the required memory, which makes it pointless to create ASICs. This algorithm was first used to create the Vertcoin coin. Despite its uniqueness and difference from Litecoin, it never gained popularity. According to CoinsMarketCap, it ranks 538th in terms of capitalization.
Another variation was NeoScrypt. Initially, the basic algorithm was changed to suit the needs of the Feathercoin cryptocurrency. They also tried to make the algorithm resistant to ASICs. NeoScrypt is used by several coins - VIVO, Phoenixcoin, Innova. Of these, only the first deserves attention. It manages to maintain its position in the top 100 cryptocurrencies according to CoinMarketCap. In terms of its characteristics, VIVO can be compared to Dash - the coin also provides a high level of anonymity.
CryptoNight algorithm
CryptoNight is a popular mining algorithm, the main feature of which is to ensure anonymity through the use of CryptoNote. The American specialist Bernstein was able to implement increased confidentiality. He managed to add darkening of the code in each signature to the algorithm. Minor changes to the source code also made it possible to implement a mixing system - all transactions are mixed together for additional data protection.
Compared to the above algorithms, CryptoNight is the least demanding, due to which cryptocurrency can be mined using a central processor. This approach makes Monero and other coins more accessible to the masses, however, the profitability of mining is still in question due to electricity prices. Among the main advantages of CryptoNight are:
- gradual reduction of emissions;
- high speed of block creation;
- ASIC resistance;
- ability to use CPU and GPU;
- higher level of anonymity than SHA-256 or other algorithms.
Despite being protected from ASIC, manufacturers still managed to create specialized equipment for cryptocurrency mining, for example, monero mining. After this, in 2022, the cryptocurrency developers decided to carry out a hard fork and switch to an improved version of the algorithm – CryptoNight V8. This made it possible to correct some errors and make any ASIC ineffective. However, because of this, the efficiency of cryptocurrency mining on video cards has dropped slightly. The hard fork solved the problem, but a year later the developers faced another problem: centralization of power. Mining blogger ValeraTV shared thoughts about a possible 51% attack.
This time, instead of a banal improvement of the old algorithm, we switched to another one - RandomX. Its peculiarity is the random execution of different parts of the code and loading of device memory. Due to the new algorithm, the GPU and CPU hashrate has decreased slightly, but ASICs will suffer the most - such equipment will cease to be effective, and it will be more profitable for the manufacturers themselves to sharpen the equipment for other coins.
Algorithm X11 and higher
X11 is a mining algorithm that uses 11 functions
for hashing. This approach provides a high degree of security and protection from ASICs. In theory, developers will need a lot of time to create specialized equipment. The algorithm was first used by the Darkcoin cryptocurrency, which appeared in 2014. A year later, it changed its name to Dash. Today dash mining is available on video cards and ASICs with X11 support.
For the first few years, ASIC production was held back, but in 2016, manufacturers were able to find a solution. This gave impetus to the development of updated versions of the algorithm. This is how new versions of the algorithm appeared - X13, X15 and X17. Their basic principle of operation is practically the same, since they only add a number of functions. It is not difficult to guess that the latter option is considered the most protected from ASIC. The X17 algorithm is used by the following cryptocurrencies:
- Verge;
- MKTCoin;
- S.H.I.E.L.D.;
- Bitmark;
- Volvox;
- GlobalToken.
The most popular of them is Verge - it ranks 85th.
by capitalization size (according to CoinMarketCap). Unlike X11, X17 does not yet have a developed ASIC; therefore, CPU and GPU are suitable for mining Verge and similar cryptocurrencies. This has a positive effect on hashrate, but due to the low popularity of most coins, mining may be unprofitable due to high electricity tariffs.
Equihash Algorithm
Equihash is an anonymous algorithm that appeared in 2016. It was used to create the Zcash cryptocurrency. The coin is currently in 32nd place in the CoinMarketCap ranking. The algorithm allows you to publish payments on the blockchain, but at the same time hides the sender, recipient and transfer amount. Its authors are Alexander Biryukov and Dmitry Khovratov, scientists from Luxembourg. At one time, individuals called Zcash the most attractive replacement for Bitcoin due to its true level of anonymity - the origin of the coin cannot be determined through zero-knowledge proof.
Equihash is quite demanding in terms of memory space, while the processing speed of calculations plays a lesser role. This solution also makes the network resistant to ASIC, but over time, manufacturers were able to create a machine for efficient mining - Antminer Z9 mini from Bitmain and A9 ZMaster. The creators of Zcash refused to carry out a hard fork or other methods of combating ASIC. As a result, the value of the cryptocurrency fell sharply - previously Zcash was confidently in the top 10 cryptocurrencies and had a chance to gain a foothold in the list.
As an alternative option, the Zero cryptocurrency appeared. It uses an improved EquihashZero algorithm, which better protects the network from ASICs. So far, manufacturers have not been able to create specialized equipment, so miners use GPUs. However, the Zero coin is practically not traded on exchanges, and its popularity is quickly falling.
ProgPow algorithm
ProgPow appeared in 2022. This is another algorithm that was developed to combat ASICs. It began to be used after the hard fork of the first cryptocurrency - a new coin, Bitcoin Interest, appeared on the market. Ethereum developers, including Vitalik Buterin, drew attention to the new algorithm. Despite the hype around the coin, it quickly fell in price.
For 2 years, not a single manufacturer has introduced an ASIC for mining coins using the ProgPow algorithm, but the reason lies not only in good security. Not a single coin has been able to break into the top 20, which is why many of them enjoy low popularity among both buyers and miners. You can learn more about the tests of the ProgPow algorithm in the video from ValeraTV.
Quark algorithm
The Quark algorithm appeared in 2013. Jean-Philippe Aumasson, Willy Meyer, Maria Naya-Plasenia and Luca Hensen were responsible for its development. The main difference from other algorithms is the parallel use of 6 hash functions: Grostl, Blue Midnight Wish, Keccak, JH, Skein, Blake. The need to create Quark is explained by the ability to use applications with the RFID protocol, which requires lightweight hash functions.
Later, the Quark algorithm found application in cryptocurrencies. It was used to implement both PoW and PoS mining. In the first case, ordinary computers were suitable for cryptocurrencies. At the start of CPU mining was quite efficient, but due to the increase in hashrate, users eventually had to use GPUs. Coins on Quark have not gained wide popularity, so it is more cost-effective to use video cards for mining ether and other coins.
Later, ASIC devices appeared - Baikal miner BK-X and Baikal Giant+ A2000. They give out 900 Mh/s and 2000 Mh/s. For comparison, the GTX 1070 from NVIDIA gives only 25.86 Mh/s. Such a large difference in power completely killed Quark mining on video cards. Now the coin of the same name ranks 1028th, and almost no one is mining it. Cryptocurrency is supported by three small exchanges.
CryptoNight
Mining on CryptoNight
CryptoNight
is an algorithm for anonymous cryptocurrencies, which is based on technologies such as ring signatures and disposable addresses. It became primarily known for its cryptocurrency Monero (XMR). Generating a block takes about 60 seconds.
Peculiarities
Using CryptoNight allows you to create a confidential, secure and fungible digital currency. These properties are achieved through the use of the CryptoNote protocol, which was created in 2012 by a blockchain developer (or group of developers) under the pseudonym Nicholas van Saberhagen. It is still unknown who is hiding behind this name.
The high degree of anonymity of the CryptoNight algorithm is achieved through the use of two technologies:
- Ring signatures (encrypt the sender);
- One-time addresses (encrypt the recipient).
Due to the fact that transactions are completely anonymous, all coins built on the CryptoNight cryptocurrency algorithm are interchangeable.
This means that they do not have a “dark past”, like, for example, Bitcoin, the blockchain of which allows you to track the movement of a certain coin and its participation in “dirty deeds”.
Blockchain Explorer
Another very important feature of this algorithm is that for mining the most effective way is to use a CPU paired with a GPU, although mining only on a central processor also gives positive results. On the contrary, the use of ASIC devices is economically unprofitable.
The secret is that CryptoNight is demanding on RAM (at least 2 GB is needed for proper operation), and not on the speed of mathematical calculations, which is what ASIC miners are strong at.
The process of finding the correct nonce to generate a block is that CryptoNight creates random blocks that are stored in the memory of the computing device, rather than sending continuous frequent calls to the miner in order to perform mathematical operations, as happens in the case of the SHA-256 algorithm (used for Bitcoin).
This allows you to build a more decentralized network and prevent a situation where more than half of the hashrate belongs to one node, and there is a high probability of a 51% attack.
☝️
To effectively mine cryptocurrencies based on CryptoNight, it is worth using Intel Core central processors of the i5 and i7 generations.
The use of Radeon HD brand equipment (new models) also shows good results. In addition, ASIC miners can be used to mine CryptoNight-based cryptocurrencies.
☝️
At the moment, the following models are suitable for this: Antminer X3, Baikal Giant-N, PinIdea RR-200, DragonMint X1/X2.
However, it is worth noting that Monero makes protocol changes every year that help protect the coin from ASIC mining. But other coins running on CryptoNight, for example, Bytecoin, Aeon, are mined without problems using ASIC.
You can learn more about how anonymous coins work by watching the video below:
Anonymous cryptocurrencies
Configuration via configuration files
An alternative startup process is configuration files. They are located in the Config folder. For each algorithm, you need to configure a file corresponding to this algorithm.
Here is a list of currently available algorithms - text configuration files located in the config folder:
- config-alloy.txt
- config-arto.txt
- config-b2n.txt
- config-bittubev2.txt
- config-conceal.txt
- config-dark.txt
- config-fast.txt
- config-fast2.txt
- config-festival.txt
- config-freehaven.txt
- config-gpu.txt
- config-graft.txt
- config-haven.txt
- config-heavy.txt
- config-hospital.txt
- config-hycon.txt
- config-italo.txt
- config-litev7.txt
- config-marketcash.txt
- config-mox.txt
- config-normal.txt
- config-normalv4.txt
- config-normalv4_64.txt
- config-normalv7.txt
- config-normalv8.txt
- config-stellitev4.txt
- config-stellitev8.txt
- config-swap.txt
- config-turtle.txt
- config-upx.txt
- config-webchain.txt
- config-ownero.txt
- config-xcash.txt
- config-zelerius.txt
The config for Monero looks like this:
Decrypting the contents of the config.txt file
config
- “cryptonight_type”: “normalv4” — indicate the type of algorithm. For Xmr this is normalv4. The list of algorithms is presented above.
- “intensity”: 0, — adjust the mining intensity. 0 - automatic.
It is recommended to leave 0 at the first start and look at the top of the miner window to see what intensity the program selected automatically.In our case, on the test RX 570 video cards, the program set the intensity to 55.
Next, this parameter will need to be selected for each card and algorithm individually, gradually increasing it by 1 unit. Valid values are from 0 to 300. More details at the end of the article. In the meantime, let's continue setting up the program for the first launch.
- “double_threads” : true, — enable double thread. For most cards, the true option is suitable (enable)
- “target_temperature”: 85, — the miner will try to maintain this temperature on all found video cards
- “hutdown_temperature”: 90, — if the video cards reach a temperature of 90°, the program will turn off the system
- “giveup_limit”: 2, — the number of attempts to connect to the pool before moving to the next pool from pools.txt. If set to 0, the miner will exit and will not retry the connection
- "retry_time" : 5, - the number of seconds to wait before trying to reconnect to the pool
- "reboot_script_gpu_watchdog" : "reboot-windows.bat", - The name of the batch file in the miner directory, if installed, it disables the miner's built-in reset procedure on gpu failure and runs this reboot script instead. You can also use reboot_script_min_rig_speed."
- "main_pool_reconnect" : 1800, - number of seconds (minimum 3 minutes or 180 seconds), frequency of attempts to reconnect to the main pool. The default is 10 minutes.
This completes the configuration.
Please note that this configuration is balanced and may not be changed for other coins. The only thing that will need to be changed is the algorithm if you mine coins using a different algorithm.
Let's move on to fine tuning.