Bitcoin and other cryptocurrencies traditionally attract increased attention from scammers of various calibers, who not only use them in their illegal activities, but also actively steal them not only from exchanges, but also from ordinary users.
Using advanced technologies, hackers are finding new ways to steal funds, but the basic and time-tested methods remain the same, since new people enter the cryptocurrency space every day, who often do not have an adequate level of knowledge and awareness to counter such attacks.
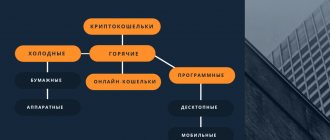
Below are the main tricks and tricks of hackers, knowing about which users can at least secure their coins.
Social engineering and phishing
Social engineering refers to a set of exchange techniques that force users to perform actions on websites or applications that can cause them harm. One of these very popular methods is phishing - the creation of clone sites of well-known resources that force users to disclose their personal data, including passwords, phone numbers, bank card details, and in recent years, private keys to cryptocurrency wallets.
Links to phishing sites can be distributed in different ways - these include advertisements on social networks and emails that copy the appearance of mailings from official projects. All this is done with the sole purpose of forcing an inattentive user to go to a fake site and enter personal data there.
In the cryptocurrency space, phishing remained the most profitable fraudulent method throughout 2017 and 2022, according to Chainalysis. However, while in 2022 it accounted for more than 88% of all fraudulent schemes, in 2022 this method became less effective, and its success rate dropped to 38.7%.
However, the risk of becoming a victim of a phishing attack remains. Among the latest such incidents are attacks on the popular Electrum wallet in December 2022 and April 2022. Often attacks were also carried out on altcoin wallets.
In addition, the Bitfinex and Binance exchanges, the Trezor hardware wallet, the LocalBitcoins platform for buying and selling bitcoins, as well as users of social networks such as Facebook have recently become victims of phishing attacks. In the latter case, attackers copy the pages of popular cryptocurrency communities, after which they use photographs of participants in real communities, tagging them in the post as winners of the platform’s loyalty program.
The importance that industry leaders place on the fight against phishing is illustrated by the fact that in April of this year, Binance Labs, the venture capital arm of the Binance cryptocurrency exchange, invested in PhishFort. This company specializes in solutions to protect against phishing attacks and focuses on high-risk businesses such as Bitcoin exchanges, ICO projects and token issuing platforms.
Recommendations for protecting against phishing attacks are quite simple: increasing general computer literacy, being attentive (manually entering the URL and checking the use of the https protocol), as well as a default distrust of advertisements offering free distribution of cryptocurrencies.
How to secure your account
To protect your e-wallet, you need to use SMS notifications and link your email. In this case, the system will send two different passwords when changing personal data, and notify the owner of any actions in the wallet.
To link mail:
- Go to the wallet website qiwi.com .
- Log in to your personal profile.
- Click on the arrow to enter the menu.
- Go to profile settings.
- Scroll down the page to the item “Personal data” .
- Click on the line "Link email".
- In the menu that opens, indicate all the necessary data and confirm the action.
To complete the activation, you need to go to the specified email address, open the message from Qiwi and follow the link.
Users actively use the Qiwi wallet electronically or using an application on Apple and Android devices. Thanks to modern security systems, you don’t have to worry about the safety of funds in your account. By following certain rules and not falling for the tricks of scammers, the user will save his money and not get into an unpleasant situation.
Trojan viruses
These numerous viruses are a type of malware that enters a computer under the guise of legitimate software.
This category includes programs that perform various actions unconfirmed by the user:
- collecting information about bank cards,
- computer malfunction,
- use of computer resources for mining purposes,
- use of IP for illegal trade, etc.
But the ingenuity of hackers does not stand still. Thus, in 2022, a new version of the notorious Win32.Rakhni Trojan was discovered. This virus has been known since 2013, but if at first it focused exclusively on encrypting devices and demanding a ransom for unlocking, the new version has gone much further.
First, it checks for folders associated with Bitcoin wallets, and if any are found, it encrypts the computer and demands a ransom. However, if no such folders were found, Win32.Rakhni installs malware that steals the computer’s computing power for the purpose of secretly mining cryptocurrencies, and also tries to spread to other devices on the network.
At the same time, as can be seen in the image above, more than 95% of all cases of computer infection with this Trojan were in Russia, with second and third places going to Kazakhstan and Ukraine.
According to Kaspersky Labs, Win32.Rakhni is most often distributed through emails that ask users to open an attached pdf file, but instead launch malware instead of the expected content.
As with phishing attacks, preventing devices from becoming infected requires basic computer hygiene and being extremely careful about the attachments you open.
Precautionary measures
There are three basic rules by following which you can ensure the security of your Visa QIWI Wallet electronic wallet.
- Use the security tools provided by the payment service;
- Follow the basic rules for storing and handling your personal data;
- Develop experience and knowledge of online behavior.
We talked a lot about the last point in the first part of the article, so let's now concentrate on the first two. Let's discuss them in more detail.
Keyloggers
Malicious programs often consist of several components, each of which performs its own task. In essence, they can be compared to Swiss Army knives - with their help, hackers can perform many different actions on the attacked system.
One of the popular attack components is the so-called keyloggers (keyloggers). They are a highly specialized tool that records all keystrokes on devices. With its help, attackers can quietly take possession of all confidential user information, including passwords and keys to cryptocurrency wallets.
Most often, keyloggers penetrate systems containing complex malicious software, but sometimes they can be embedded in completely legal software.
Manufacturers of antivirus solutions, as a rule, add well-known keyloggers to their databases, and the method of protection against them is not much different from the method of protection against any other malicious software. The problem is that there are a huge number of keyloggers, and it is physically very difficult to keep track of them all. For this reason, keyloggers are often not detected by antivirus programs on the first try.
Nevertheless, ordinary computer hygiene and the use of special software can be a good help in combating this type of attack.
Signs of a break-in
There are certain signs that attackers are trying to take over your account:
- WMID receives messages about logging in through a version of Keeper that you do not use;
- Your phone receives codes or authorization confirmation requests when you are not attempting to log in;
- The Keeper tab closes unexpectedly or freezes;
- The computer suddenly starts to slow down very much, and clearing the cache does not help.
In all of the above cases, it is recommended to log into your account, check your accounts, as well as personal data: phone, email. Then you need to change your password. If you know how other people can hack WebMoney, you can protect yourself from trouble.
ATTENTION!
If money has already been withdrawn from your wallet, you must immediately contact technical support to block the attacker’s WMID. A hacked webmoney account will also be blocked from withdrawing funds.
Public Wi-Fi networks
Theft of funds through public Wi-Fi networks has always been and remains one of the most popular tools of attackers.
Most Wi-Fi routers use the WPA (Wi-Fi Protected Access) protocol, which not only encrypts all information on the wireless network, but also ensures that only authorized users have access to it.
However, hackers found a loophole here too: by running a simple KRACK command, they force the victim’s device to reconnect to its own Wi-Fi network, after which they are able to monitor and control all information passing through it, including keys to cryptocurrency wallets.
Regular updates of the router firmware, as well as your own attentiveness, help protect against such an attack: you should never carry out transactions while in public places, such as train stations, airports, hotels, or - which happens quite often among representatives of the Bitcoin community - at blockchain conferences.
Hacking programs
There is more than one program for hacking webmoney, which can be found freely available on the Internet or borrowed from a hacker friend. These are various kinds of viruses, Trojans, scripts. They can have very different names, as well as formats, so it is almost impossible to find them on your computer.
ATTENTION!
In search of information on how to hack money on WebMoney, you yourself can become a victim. When you download a program to hack someone else's PC, you can actually infect your device with a virus. And when transferring funds from a hacked account to your own, there is a risk of exposing your personal data or IP address. Therefore, it is better not to risk your freedom or health!
Slack bots
There are quite a large number of Slack bots that hackers successfully use. As a rule, such bots send a notification to the user that there are problems with his wallet. The ultimate goal is to get the user to click on the notification and enter the private key.
The largest successful hacker attack involving Slack bots was the Enigma incident in August 2022. Then the project was forced to suspend the pre-sale of ECAT tokens after unknown attackers hacked the project website and, having indicated a false ETH address, deprived it of more than $400,000.
In addition, Enigma representatives confirmed that the project’s Slack chat was also compromised:
Recommendations: ignore such messages, send complaints to the bots distributing them, install protection on the Slack channel (for example, Metacert or Webroot security bots).
Authentication via SMS and SIM Swapping
SMS authentication remains a very common method for verifying various operations, including cryptocurrency transactions. However, back in September 2022, cybersecurity company Positive Technologies demonstrated how easy it is to intercept an SMS with a password sent via the Signaling System 7 (SS7) protocol.
The demonstration was carried out using the example of an account on the Coinbase platform, which was linked to Gmail. At first glance, it might seem that we are talking about a vulnerability on the Coinbase side, but in reality, the proprietary tool used by Positive Technologies exploited weaknesses in the cellular network itself.
By redirecting text messages to their own number, the researchers were able to reset and set a new password on the mail, after which they gained full access to the wallet.
In this case, the experiment was carried out for research purposes, and the actual theft of coins did not occur, but its results showed that this method could well be used by real criminals.
In this material, Hacken specialists also listed the main options for intercepting SMS:
- Wiretapping . Interception of SMS by law enforcement officers due to abuse of official authority or misuse of materials from covert investigative actions.
- Duplication (cloning) of a SIM card through a cellular operator using the client’s personal data and further use of the cloned SIM card in illegal activities.
- A false base station to intercept and decrypt all incoming subscriber messages and further use the intercepted data in illegal activities.
- Hacking a subscriber’s “Personal Account” on a mobile operator’s website or application and redirecting all messages to the attacker’s address, as well as further use of the received data in illegal activities.
The second item on this list is also interesting—cloning (replacing) a SIM card. This method is known as SIM Swapping, and in the first high-profile case it was used to steal $14 million worth of cryptocurrency.
We are talking about a case that occurred in 2022, when two hackers were arrested in the United States for convincing a mobile operator to transfer control of a number that had two-factor authentication to the account of the administrator of the Crowd Machine project.
Recommendation: abandon SMS verification in favor of special programs for two-factor authentication (2FA), for example, Google Authenticator.
Is it possible to hack Qiwi wallet?
The QIWI e-wallet is particularly easy to use. To log into your account and pay for a service or product, you only need to spend a few minutes. Despite the high level of security, the system has weaknesses. The only vulnerability is that there is no need to enter a large amount of data when making a transaction.
Attackers take advantage of the shortcomings. Inexperienced users who do not have a sufficient amount of knowledge in their arsenal will not be able to hack. The only option is to play on the inattention of account owners.
Among the easiest options for hacking electronic wallets are:
- Using the terminal.
- Through special programs.
- Using deceptive schemes.
There are no reliable methods that are guaranteed to hack other people's wallets. But when using the most “successful” options, it is possible to find 1-2 not particularly attentive users, who will say goodbye to their savings.
Mobile applications
The victims of hackers most often are owners of Android devices, who use only a login and password instead of 2FA. This happens also because the process of adding applications to the Google Play Store is less strict than that of the App Store. Attackers take advantage of this by hosting their own apps that imitate well-known wallets and exchanges and trick inattentive users into giving away sensitive data.
One of the high-profile stories with fake applications was related to the Poloniex exchange. In November 2022, ESET experts discovered a program on Google Play that pretended to be the official mobile application of this American exchange. The essence of the scam was that users who downloaded the program entered their login and password. This allowed the creators of the virus to independently change settings, perform transactions, and also gain access to users’ mail.
Despite the fact that at that time Poloniex did not have official mobile applications (they were released only in July 2018), two versions of fake applications were installed by more than 5 thousand people. After a warning from ESET, they were removed from Google Play.
Also on Google Play were fake applications MetaMask and Trezor Mobile Wallet.
Users of iOS devices more often become victims of attackers who distribute applications with a built-in hidden mining function. After discovering this problem, Apple was forced to tighten the rules for accepting applications in the App Store. At the same time, the damage from such applications is quite small - they only reduce the performance of the computer without wasting money.
Recommendations: Do not install applications that are not absolutely necessary. Don't forget about two-factor authentication, and also check links to applications on the official websites of projects and platforms to ensure their authenticity.
Encryption methods
Many people underestimate the importance of creating a strong and complex password. Some don’t stretch their imaginations at all and, having come up with one password, set it on all sites. This widespread approach plays into the hands of scammers, as it makes their work as simple as possible.
There are some tips on how to keep your password simple, but at the same time strong.:
- Different layout. Create a password in Russian, and type it in the English layout or in another order (remember that difficulties may arise when logging in from a mobile device).
- Replacing letters with numbers. Instead of "S" write "5", replace "o" with "0".
- A set of Russian words in English letters. Use transliteration like: “Sea” - “More”, “winter” - “winter”.
The safest thing to do is to combine several methods and complement your tactics.