Cryptonite (in English cryptonight) is one of the cryptocurrency mining algorithms. The following coins work on the basis of it:
- Monero. This cryptocurrency is the most popular and expensive of all that work on this algorithm;
- CryptoNoteCoin is a test cryptocurrency that was created to test the cryptonight algorithm. It has no commercial value;
- Bytecoin is a private, decentralized system that provides maximum security when transferring funds;
- Sumokoin. The coin is a fork of Monero;
- Karbovanets is another decentralized system in which the price of a coin depends only on supply and demand.
The main goal of this algorithm is to allocate a larger block of information in the device's RAM with an unexpected sequence.
The main advantages of mining cryptocurrencies based on the cryptonight algorithm:
- Video cards and processors heat up less;
- The profit from mining is greater;
- Falling emission;
- Coins cannot be mined on specialized Asic devices.
So, cryptocurrencies based on the cryptonight algorithm can be mined in three ways:
- On the video card;
- On the processor.
Let's look at each method in more detail.
Mining coins on cryptonight on a processor
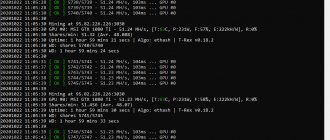
Mining on a processor consumes less electricity than on a video card. The Cryptonight algorithm allows you to mine cryptocurrencies on a processor with great returns, which is rare in 2022. For example, mining the Monero coin on an Intel Core I7 processor provides a stable income of $0.25 per day.
To mine on a processor, you need to download one of the following programs:
- Yam CPU;
- Wolf's CPU miner;
- Claymore CPU Miner.
To properly configure the program on the Windows operating system, you need to launch the miner and enter the following information:
- Yam CPU – “yam -cx -M stratum+tcp://“address wallet”:x“address pool”:“number port”;
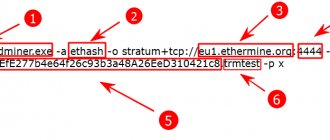
- Wolf's CPU miner – "minerd.exe -a cryptonight -o stratum+tcp://"address pool":"number port" -u "address wallet" -px";
- Claymore CPU Miner – “NsCpuCNMiner64.exe -o stratum+tcp://“address pool”:“number port -u “address wallet” -px”.
Note: instead of words in quotation marks, you must enter addresses and numbers. All quotation marks should also be removed, as they are included for better understanding. Translation:
- address wallet – your wallet address;
- address pool – pool address;
- number port – port number;
- Login and password – your login and password.
If we talk about mining on a processor on the Linux operating system, then it is more economically profitable. Because fine optimization can be done on this OS, making mining more efficient. To configure the function, you need to enter the following command: “Sudo sysctl -w vm.nr_hugepages=Y”, where Y is the number of processor cores. To start the main process, you need to write: “sudo ./minerd -a cryptonight -o stratum+tcp://“address pool”:“number port” -u “address wallet” -px”
Features of CryptoNight
The CryptoNote algorithm is an application protocol that uses the CryptoNight hash function to reduce hardware performance differences and minimize network load. It is even more profitable to mine a cryptocurrency with such an algorithm on a regular processor than to use financially expensive video cards or ASICs for this.
CryptoNight digital coins are considered the most anonymous, lightweight and discreet. This was created using the technology of ring signatures, which hide the sending party, and one-time recipient addresses. The presence of a signature only confirms that the transaction was made by one of the group members, but it is impossible to distinguish them from each other.
Operations that have a ring signature reference a number of other operations included in the blockchain. Moreover, there is no need for all transactions to be addressed to one party. The more links a ring signature has, the more convoluted the chain becomes and the longer the title. To receive coins, one-time addresses are generated, which have part of the real address and part of the random key.
Mining coins on cryptonight on a video card
Mining cryptonight-based cryptocurrencies on a graphics card provides faster speeds, but consumes more electricity.
To mine coins on an AMD video card, you can use Claymore GPU-miner, which charges up to 2.5% commission. To configure this miner, you need to run the file “pool.bat” or “start.bat” and enter the following information: “NsGpuCNMiner.exe -o stratum+tcp://“address pool”:“number port” -u “login and password” "-px"
The following programs are suitable for Nvidea video cards:
- CUDA-miner;
- Сcminer cryptonight nvidia.
To configure them, run the file “pool.bat” or “start.bat” and write the following command for each miner, respectively:
- cudaminer.exe -o stratum+tcp://"address pool":"number port" -u "login and password" -px;
- сcminer cryptonight -o stratum+tcp://"address pool":"number port" -u "login and password" -p x.
If you use a built-in wallet, there will be a bit of difficulty. In this case, to transfer funds to the exchange for exchange, you will need the simplewallet and bitmonerod commands.
Simplewallet commands:
- “Transfer” – transfer funds;
- “Adress” – show the current address for receiving funds;
- “Refresh” – Synchronize Wallet;
- “Balance” – display the current balance.
Bitmonerod Teams:
- “Help” – display help;
- “Save” – save blockchain.bin;
- “Diff” – display the current difficulty;
- “Print-Block” – display the contents of the block.
When sending funds, you must indicate the payment ID that the exchange will issue. Also use the Anonymity feature, which allows you to avoid transaction tracking. To do this, use numbers: from one to ten. The higher the number, the higher the level of security. However, the higher the number, the slower the payment will be.
ALL ABOUT MINING
Get a 3% discount! Use bonus code: HF17TOPBTC3 The CryptoNight algorithm is an implementation of the CryptoNote protocol; 15 digital currencies currently operate on its basis. It is good for its very slight heating of video cards and the central processor and significantly increased mining efficiency in comparison with older and well-known analogues. It operates on the basis of ring signatures, and the fact of mining on it is elevated to an advantage for the cryptographic coin. It is important not to confuse CryptoNight with CryptoNote, because... the first is the name of the hash function in the code of the second.
The author of the crypto-based protocol was the American Daniel Bernstein. He included transaction obfusification in it, and as a result, passive mixing became possible in the system: the anonymity of transactions was ensured, and system participants, if questions arose from third parties, were able to organize plausible deniability.
It is no exaggeration to say that CryptoKnight has a high level of practical efficiency. All its components are focused on effective mining on ordinary computers.
Why CryptoNight with a plus sign?
It works on the “proof-of-work” principle and is good for computing on processors, that is, one of its main tasks is to minimize the gap between miners on a personal computer and owners of specialized ASIC devices.
It is based on the general idea of scrypt about a large table of data where random queries are created. But the author noticed a minus associated with the linear “time”-“memory” compromise. In scrypt, the 2nd layer makes the next block of information based on the previous one. As a result, if you store, for example, every 2nd block out of N, then in half the cases it will be necessary to recalculate it again. There are also N such random requests to the array; in the end, it turns out that saving 50% of memory, you can calculate N + 1/2N = 150% of blocks. In other words, 1.5 times more.
Based on these findings, three fundamental differences were identified:
- Each new block is determined taking into account ALL those already preceding it. Therefore, if you throw out, for example, every 2nd block, then in order to restore the omission, you will have to recalculate all the previous ones, and not just the thrown one.
- Accesses to a data array are both reading and writing. As a result, each element acquires time, and recalculation turns out to be more and more labor-intensive.
- The total number of accesses to the array greatly exceeds the number of its elements, so by the end of the cycle the resulting array changes extremely significantly, almost beyond recognition.
And a couple more technical points:
- 64-bit operations and AES encryption (shuffle function) are used, which refers to modern processors equipped with built-in appropriate instructions.
- The total amount of memory requested by the algorithm is 2 MB, which is comparable to the size of L3-cash per core. For ASIC, this is not exactly unattainable, but the cost level is very high.
Advantages and disadvantages
- Ensuring maximum program anonymity.
- Smoothly decreasing emission. The issue is predictable, and this attracts sellers. For example, the reward for a Bitcoin block, due to its irregularity, is divided in half approximately once every 4 years.
- Small time intervals between created blocks.
- It is not possible to mine coins on an ASIC, so mining them on a personal computer becomes more profitable.
- Using CPU+GPU for increased performance. As a result, heating and load on the system are reduced, which allows you to speed up computing processes and ensure work with large volumes of data.
- Innovations become an advantageous distinction between CryptoNight coins and many altcoins created using outdated algorithms.
- The payback and efficiency of mining is higher than that of many other cryptocurrencies.
There are quite a lot of advantages, including increased stability and security of mining, the ability to mine crypto coins on a par with GPU miners and, of course, saving on electricity.
According to the developers, the algorithm is virtually impossible to hack. If someone tries to do this, they will have to spend a large amount of expensive electricity and PC computing power.
There are significantly fewer disadvantages. Essentially there is only one:
- The profit from production is getting lower. The difficulty of mining is growing because... More and more people want to join the process.
CryptoNight coins
The most popular digital coins mined on the processor include:
- Monero is a digital symbol of XMR, released in 2014. Based on original technology, it is positioned as an untraceable currency. A block is generated in 1 minute.
- ByteCoin is a BCN ticker, released in 2012. It became the first crypto coin launched using this algorithm.
- DashCoin - DSH ticker, released in 2014. The update occurs with minimal development costs and almost zero possibility of errors in the protocols.
- AEONCoin - mines well on weak computers.
Also among the popular mined currencies:
- Boolberry;
- DigitalNote;
- RieCoin.
How to start mining on Cryptonight?
Theoretically, it is possible to mine cryptocurrency using the algorithm both on the central processor and on video cards. However, the most efficient option is the processor, because... GPU chips require more power consumption, although they provide increased speed.
To start mining cryptocoins on a PC, you need to download the program from the following:
If, nevertheless, the choice is made in favor of video cards, then you can choose the closed Claymore GPU-miner, available to owners of AMD cards and requiring up to 2.5% commission payments.
The best pool for mining digital currency on CryptoNight is called MinerGate. Among the advantages of the pool are:
- availability of Russian version;
- non-trivial interface;
- automated selection of a miner for the processor;
- referral system;
- links to the latest versions of miners for video cards.
CryptoNight turns the idea of miners who are confident in the possibility of mining cryptocurrency only if they have their own farm. Thanks to the use of this algorithm, you can receive currency without collecting specialized equipment, but using your own personal computer.
Cryptonight Pools Review
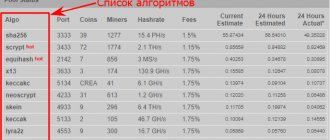
The following is a list of the best cryptocurrency pools based on the cryptonight algorithm:
- Minergate is a Russian-language service. To mine cryptocurrency, you need to download the program from the official website of the pool and configure the system. Funds are available for withdrawal immediately. The service takes a small commission;
- Mining pool hub is a service that was formed quite recently. The pool is perfect for both beginners and professionals;
- monero.miners.pro is another Russian service for mining the Monero coin. When withdrawing funds, a commission of 1.5% is charged;
Mining process
Like other PoW platforms, the CryptoNight network generates tasks for its miners, who receive a reward for each signed block, but in this algorithm the time period of calculations depends more on the speed of access to RAM than on the speed of performing algebraic operations. The development of a new algorithm for confirming completed work was aimed at implementing the principle of egalitarianism: 1 processor = 1 vote.
The CryptoNote algorithm creates large blocks with an unpredictable sequence, which are more convenient to store in PC memory rather than forming permanent requests. Each parallel thread will require an increased amount of memory directly proportional to the number of threads. The new algorithm uses about 2 MB of RAM, which corresponds to the minimum L3 cache size of all modern processors.
It is this principle of protecting internal parallelism that makes it unprofitable to create a powerful computing device. The equality of miners and the minimal complexity of mathematical calculations attracts a large number of participants, but this creates the threat of a massive emergence of bots capable of taking thousands of coins to one wallet.
Owners of the Monero cryptocurrency, for example, will protect the decentralization of their platform by modifying the CryptoNight algorithm twice a year. The same algorithm is used by coins:
- Electroneum (ETN);
- Bytecoin (BCN);
- DigitalNote (XDN);
- Sumokoin (SUMO);
- Karbowanec (KRB) and some others.
CryptoNight-Lite
A modified version of the CryptoNight-Lite algorithm is even less expensive and demanding. This function is used by the AEON coin and can be mined even on the weakest PCs.
The speed of block generation does not depend much on the PoW protocol; in the AEON system, synchronization will occur faster, thanks to the implementation of the dimming or trimming option. Compared to its parent, CryptoNight-Lite has the following characteristics:
- RAM requirement – 1 MB (in Cryptonight – 2 MB);
- number of AES iterations – 500,000 (in Cryptonight – 1,000,000).
The CryptoNight-Lite hash code becomes four times lighter and faster than usual. It is impossible to determine exactly how this change will affect blockchain generation, since different equipment will have different performance characteristics and weak points, but for the processor, a 4x improvement is a good indicator.
What is the CryptoNight algorithm?
Cryptonite is one of the most popular, after SHA256 and Scrypt, algorithms for data encryption. The main difference and advantage of Cryptonight over other algorithms is increased anonymity, which is achieved through the CryptoNote protocol.
This algorithm was first used in the cryptocurrency industry in 2014 by programmer Ricardo Spagni, who created the Bitmonero coin, which later changed its name to Monero (XMR). Thanks to CryptoNight, the XMR cryptocurrency has gained the anonymity function that Bitcoin so lacked.
What we know about the upcoming CryptoNight ASICs:
| Antminer X3 | Baikal Giant-N | PinIdea RR-200 | Halong Mining X1 | Halong Mining X2 | |
| Price: | $3000* | $3600 | $1740 | $1714 | $3115 |
| Min. order: | 1 device** | 6 devices | 5 devices | — | — |
| Hashrate: | 220 KHS | 20 KHS | 27 KHS | 124 KHS | 248 KHS |
| Consumption: | 500 W | 60 W | 350 W | 245 W | 490 W |
* — price for the 3rd batch, which will be sent before May 31. The price for the 4th batch, which will be shipped before July 31, will drop to $1900.
**—maximum number of devices to order for one customer = 1 device.
In the end, Monero developers are unhappy with the fact that the coin can be mined using ASIC miners. They consider this a violation of the kill-switch principle, which will allow them to remotely turn off devices at any time or otherwise influence the coin mining process. This threat could destroy the entire network."
“In a similar way, the government could require miners to have a license to buy and operate ASICs, thereby limiting the use of ASICs to only a certain group of privileged people. Additionally, licensing may ultimately lead to blacklisting of certain transactions, e.g. governments may require miners not to perform certain transactions, where disobedience will result in such miners having their license revoked.” Conversely, introducing licenses for the use of general purpose hardware (CPU, GPU) is probably not feasible.
To prevent centralization of the XMR network, the Monero developers decided to modify their POW algorithm every six months. The changes should be small enough that the CPU and GPU hashrate remains unchanged, but sufficient to ensure that existing CryptoNight ASIC devices at that time will not be able to work with the modified algorithms.
All of the above means that the Monero developers remain true to their original promises, one of which is that Monero is a cryptocurrency protected from ASIC miners and none of these devices will be able to mine XMR. If manufacturers want to release a new batch of ASICs using an already modified algorithm, then such devices will be able to “dig” Monero only until the next modification of the algorithm.
What Riccardo Spagni, lead Monero developer, wrote about Antminer X3 on his Twitter account: