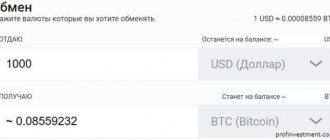
Bitcoin Core is the official open source software of the Bitcoin network, combining the functions of a Bitcoin wallet and a full node with which network participants can maintain its functionality.
A private key is a code tied to virtual coins in a Bitcoin wallet and confirms ownership of the cryptocurrency.
The private key of a Bitcoin wallet, such as Bitcoin Core, is a secret set of characters that allows the owner to use the coins in the account. Each cryptocurrency storage uses one or more private (private) keys stored in a special file. The peculiarity of the code is its direct connection with public cryptocurrency addresses.
Using a private key, Bitcoin is transferred from one wallet to another. At the same time, importing such code without conducting a transaction is a risky undertaking; it is not recommended even for experienced cryptocurrency holders. This is because BTC can be stolen from the wallet that imported the private key.
What is a private key?
A private key (also called a private key) is a special combination of symbols that provides access to the cryptocurrencies stored in the account. Only the person who knows the key can move and spend coins.
In the simplest case (more on this below), the system itself generates a private key, after which a public (open) key is created on its basis. The public and private key are alphanumeric combinations that are linked to each other. Moreover, this is a unidirectional connection - knowing the private key, you can find out the public one, but knowing the public key, you can’t find out the private one.
A private key is a complex cryptogram created by applying an encryption algorithm; it also serves as a kind of signature when sending transactions.
The video below clearly shows how private and public keys work:
4—QR code reconstruction
It is clear that we have to restore a QR code measuring 41x41 pixels. We decided to use a Google spreadsheet (it's easy to draw, highlight and mask the QR code).
The following steps went through:
- We drew each pattern included in the standard (search patterns, alignment pattern (in Version 6 there is only one), synchronization bars and indents (frame) as shown in Fig. No. 12)
- Added bits from the formatting information string found in the previous step.
- We filled out the remaining blocks of the QR code according to our screenshot (Fig. No. 11).
Now let's try to squeeze some more information out of the screenshots where the top and left parts of the QR code are visible. They show very little, but every bit can come in handy at this stage.
#16 - Here we have collected some more bits from the top rows #17 - Do the same with the left side of the QR code (rotated 90°)
Below is the QR code that we managed to reconstruct. The next step is to determine the sequence of bits and identify the codewords and error correction codewords.
#18 – Step-by-step reconstruction of a QR code
What does a private key look like?
Let's look at the example of Bitcoin to see what a private key looks like. Bitcoin is based on the SHA-256 encryption algorithm, which creates a 256-bit number consisting of zero and one.
However, using such a long dial is very inconvenient and, moreover, the key must be encrypted. Therefore, the private key for a Bitcoin account is created as a 32-byte number, which consists of 64 characters. For each character there are two values (zero or one) from the above 256-bit number. Numbers from 1 to 9 and alphabetic characters from A to F are used.
Example of a private key:
B4653223363AA61F20BD08FC233AC37262
It is almost impossible to guess or brute force a private key. Essentially it represents a number in the range from 1 to 10 to the 77th power. If we imagine that a person has the ability to sort through one trillion numbers per second, then finding one private key would take at least a million ages of the existence of planet Earth.
But some researchers believe that with the development and improvement of quantum technologies, there will be ways to hack the blockchain.
It is also worth saying that with the development of the cryptosphere, different formats for storing private keys have appeared. These are alternative formats called the "Wallet Import Format". There are three of them:
- Hex: 1E99674A4CA27608A45A1813ABB0E9E52CFA330AC563EDBB32C8AAC6A964AECA.
- WIF: 5J3nBbAG58CuQ346RNLpPUA
- WIF-compressed: KxFC1jnghCoACiATWZ3oXa748VN6ac3TYzGkd7YbsqGLY
These formats store the same key. Each format can be easily converted to any other.
7 - Error correction code
At this stage, we are still far from being able to completely reproduce the private key. But soon we will find out whether the collected data is enough for us to restore it using an error correction code (ECC).
ECC is a coding technique that allows reliable communication over unreliable channels. With their help, you can reconstruct the source data by identifying and correcting errors and unreadable areas.
QR codes use Reed-Solomon codes (a subtype of the Bose-Chaudhury-Hocquengham codes that we saw when we deciphered the formatting data chain in step #3).
We will not explain in detail how to use Reed-Solomon codes. Much has been written about this in detail on many resources. In short:
The Reed-Solomon encoder produces RCC codewords. They are the remainder of the polynomial representing the message and the irreducible polynomial generator.
No. 29 - irreducible polynomial generator for 28 correction codewords
The Reed-Solomon decoder is a little more complex because there are many different ways to decode a message. There are various decoding algorithms for this. More details about the decoding process here: https://en.wikiversity.org/wiki/Reed%E2%80%93Solomon_codes_for_coders
The Reed-Solomon decoder is capable of simultaneously correcting unreadable data and errors. But there is a limit to his capabilities - the Singleton limit.
In our case, the risk was falling outside this limit of the maximum possible code power. Reed-Solomon is an optimal forward error correction system and is "vulnerable" to this threshold effect. This means that if you exceed the maximum code power, you cannot apply correction codes. That is, the time has come for brute force selection.
The code power limit (the number of errors and omissions that can be corrected) is determined by the formula below, as stated on page 33 of the ISO standard:
e + 2*t ≤ d - p
Where:
- e: number of gaps (unreadable data);
- t: number of errors;
- d: number of error correction codewords;
- p : number of codewords protecting against incorrect decoding (0 in our case: 6-H).
This formula means that you can correct up to 14 errors or 28 omissions per block (or a combination of errors and omissions for a total of no more than 28). We took advantage of the fact that we knew where there were gaps in the QR codes to apply the highest level of correction (28 codewords per block).
Let's see if the code power limit is exceeded in each block:
- Block 1: Data contains 6 gaps, KCO contains 22 gaps;
- Block 2: Data contains 12 gaps, ECC contains 21 gaps;
- Block 3: Data contains 10 gaps, ECC contains 18 gaps;
- Block 4: Data contains 6 gaps, ECC contains 21 gaps.
With 28 passes, blocks 1 and 3 are not exceeding the capacity limit and will be fully restored. The same is true for block 4, where there are only 27 gaps.
The only block exceeding the code power limit is block 2 with 33 passes. We will have to select it using brute force. Fortunately, we have already reduced the number of combinations to a minimum.
What is a private key for?
The private key performs two main functions. The first is the secure storage of cryptocurrency, since only those who know the private key can conduct transactions with these assets. That is why you need to be extremely careful when creating a key, and under no circumstances show it to third parties, and also not store it on the Internet, and ideally even on computers that are connected to the Internet.
The second function is transaction signing. The private key is also a digital signature. As mentioned above, each private key has a unique public key or address associated with it.
When sending a BTC transaction to the network, nodes verify that the sender's address matches its public key, while information about the private key remains secret to everyone, even validators. Once the required number of confirmations are received, the transaction will be delivered to the recipient.
Public key
The public key is described as follows in the Ethereum yellow paper.
"Where pu is the public key, assumed to be a byte array of size 64 (formed from the concatenation of two positive integers each <2256), and pr is the private key, a byte array of size 32 (or one positive integer in the specified range)."
This is achieved using the elliptic curve group operation in cryptography.
To obtain the public key, the private key is multiplied by G. The multiplication used to obtain the public key is an elliptic curve multiplication, which is completely different from the normal multiplication for which we are going to use the JS library.
G is called the generator point, which is one of the key parameters of elliptic curve cryptography. G has a fixed value for ecp256k1 which is recommended by experts. You can read more here.
var EC = require('elliptic').ec; var BN = require('bn.js'); var ec = new EC('secp256k1'); var G = ec.g; // Generator point var pk = new BN('1'); // private key as big number var pubPoint=G.mul(pk); // EC multiplication to determine public point var x = pubPoint.getX().toBuffer(); //32 bit x co-ordinate of public point var y = pubPoint.getY().toBuffer(); //32 bit y co-ordinate of public point var publicKey =Buffer.concat([x,y]) console.log(“pub key::”+publicKey.toString('hex'))
How to create a secure private key?
Now let's talk about one of the most important points - how to create such a key so that it ensures reliable storage of cryptocurrency assets. You can generate a private key using several services.
Paper wallets
The advantage of this method is that the keys are stored offline. One of the proven services, with the help of which even a beginner can create a private key, is the bitaddress.org service. You need to follow three simple steps:
Step 1: Follow the link above. A window will appear on the screen with a set of random alphabetic and numeric characters. Move the mouse around the screen until the randomness percentage reaches 100%:
Step 2. When the indicator reaches 100%, a QR code and a hash of the private key will appear on the screen:
Step 3. Print out the newly created keys or you can also copy the key onto paper.
Desktop wallets
The key generation process in desktop wallets is very simple. The most popular are the Exodus, Electrum, Jaxx wallet. The key will be created fully automatically.
Let's look at this process using the Exodus wallet as an example:
- Go to the developer menu and select create a Bitcoin wallet.
- Select the "Export" section. The system will display a warning that when copying and exporting a private key there is a risk of it being lost and used by third parties. Agree with export.
- The private key will be saved in a folder on your desktop.
To be safe, copy the key file to a medium to which there is no Internet access, for example, a flash drive. You can also copy the key onto a piece of paper.
Online wallets
Online cryptocurrency wallets also allow you to create a private key. In some it is generated automatically, and in others you can create it yourself.
It is very important to familiarize yourself with the terms and conditions of a particular wallet. It is recommended to choose those that store the keys not on the server, but on the user’s side.
For example, such a service is Bitcoin Wallet Blockchain.
Previously, it was possible to obtain keys automatically in this service, but this option has recently been removed. This can now be done by creating a mnemonic phrase. A mnemonic phrase is a special list of words that are subsequently converted into a hash of the private key. In the Blockchain wallet, the mnemonic phrase consists of 12 words.
To get a private key, you need to do the following:
- Go to the section “Storage - Settings - Security - Create a backup phrase.”
- The system will offer you to select 12 words from a random set in several stages. You need to choose and remember. To be safe, you can write down these words on a piece of paper, which is recommended to be stored in a safe place that is not accessible to third parties.
- The wallet offers to check how well you remember the selected words - you need to enter any four of the twelve.
- Next, follow the link iancoleman.io/bip39/. Please make sure that the link looks exactly like this, otherwise you risk becoming a victim of a phishing attack.
- The next step is very important: disconnect from the network to ensure maximum security.
- Having gone to the site, you need to select the language of the mnemonic phrase, the number of words, and enter the words themselves. Double-check that you entered the words correctly - if you misspell one letter, you could lose all your crypto assets!
The system will generate a private key, which you will find at the bottom of the window in the “Derivation Path” section.
Brain Wallet (“brain wallet”)
This method is considered more reliable, since the user himself is the creator of his own key. However, it is suitable for more advanced users.
This method is called Brain Wallet, i.e. “brain wallet”, since the key is generated by the brain efforts of the owner of the future key, and consists in the fact that the user must come up with any phrase or number and encrypt it using the SHA-256 algorithm.
When creating a key in this way, you need to remember only one rule: the more complex the phrase/number, the more reliable the private key will be.
Of course, you can also use the number 1 as a key. And you will laugh, but there are users who did just that.
The hash of the number 1 in the SHA-256 system is the following value:
- 1EHNa6Q4Jz2uvNExL497mE43ikXhwF6kZm
If you follow the link, you will see that over the past few years this key has been used in more than 1,200 transactions and almost 5 BTC have been transacted on it:
A similar situation can be observed when using the well-known phrase “To be or not to be” as a private key:
- 1J3m4nneGFppRjx6qv92qyz7EsMVdLfr8R
See for yourself:
These examples show that choosing a reliable private key is a step that needs to be taken very seriously.
Some services provide the option of creating a “brain wallet,” for example, bitaddress.org.
To use this function, you need to go to the “Smart Wallet” tab:
Next, you need to enter a phrase (note that it should be impossible or at least difficult to guess), confirm again and click on the “View” button. The site will generate a private key, which can be printed or written down on paper:
The advantage of this method is that even if you lose your private address, you can restore it if you convert it using the standard SHA-256 algorithm - such converters are easy to find on the Internet, for example, this one.
You don’t have to write down the private key at all if you are sure that you remember the phrase, but you need to write down the address so that you can transfer bitcoins to it.
But if you are still very afraid that someone will be able to find out your even super-complex key, then there is another way to create a private key that will provide 1000% security. Take a coin, toss it 160 times in a row and write down “0” if it lands on tails and “1” if it lands on heads. After this, the resulting number can be converted into the SHA-256 algorithm, and you will get a very reliable private key, since it is unlikely that anyone will be able to flip a coin the same way as you.
3 — QR code design standard. Part 1
An important task was to understand how QR codes work and how much it is possible to repair a damaged QR code using an error correction code.
The Wikipedia article gave basic information, but the ISO/IEC 18004 standard was really useful (a free version of its first edition is available on Swisseduc). We also found this gem online.
No. 11 The correction area and mask for the QR code were taken from this screenshot.
Before we start reconstructing the QR code, let's see what we can learn from this picture using the ISO standard and the description of the QR code structure.
No. 12 Picture from Wikimedia Commons
We were interested in the blue column (x:8, y:22–28).
This is part of the formatting data string (15-bit sequence. 5 data bits and 10 bits of the BCH correction code). The bits located at coordinates (x:8, y:22–28) are bits of the line from 8 to 14. We only had 7 of the 15 bits, but they were enough to find the necessary information.
The formatting data string encodes the level of correction and mask pattern applied to the QR code. There are 4 possible levels of error correction (L, M, Q, H) and 8 possible mask patterns => 32 possible lines of formatting information.
More details about creating information lines can be found on page 76 of the standard (Appendix C - Format Information). A list of 32 possible options can be found here.
Let's use the standard to figure out what bits we have.
No. 13 Picture from Wikimedia Commons
From top to bottom, we have bits 8 through 14 of the information line. Bit 14 is the most important. With its help, we can now read screenshot No. 11.
0011001XXXXXXXX
Let's look at the table of formatting data strings. The only matching combination is with correction level code: H and mask pattern: 3
No. 14 – Picture from Wikimedia Commons
We also needed to find a QR code encoding format. There are 5 types of encoding formats (each uses a special method of converting text into bits):
- Digital (0–9)
- Alphanumeric (0–9; A-Z; nine other characters: space $ % * +- . / : )
- 8-bit byte (JIS [Japanese Industrial Standard] 8-bit character set. JIS X 0201 Japanese version of ISO 646 standard)
- Kanji (Shift JIS [Japanese encoding] characters can encode each Kanji character into 2 bytes)
- ECI (Extended Channel Interpretation, when you require special/customized encoding)
The encoding format for our QR code is 8-bit byte. Numeric and alphanumeric formats do not support lowercase letters used in private keys. Kanji encodes on 2 bytes (we only need one), and such a complex format as ECI is clearly overkill in our case.
We are almost ready to start reconstructing the QR code. The last thing we need to know is its size.
There are 40 different QR code sizes (called versions). They range in size from 21x21 pixels (Version 1) to 177 x 177 pixels (Version 40). As the version number increases, the code size increases by 4x4 pixels. Each version has a maximum capacity depending on the encoding format and error correction level. For more details, see page 28 of the ISO standard.
We knew that our QR code should contain 52 characters (416 bits) with an error correction level of H.
No. 15 - V6 is the smallest version, capable of accommodating a 416-bit key with correction level H. V5 is too small, V7 is too large
The size of Version 6 of the QR code is 41x41 pixels. Now we have all the information we need to reconstruct the QR code.
How to properly store private keys?
It is important not only to create a reliable key, but also to store it correctly. In general, there are three options for storing keys:
- on paper (metal),
- on electronic media,
- in mind.
However, no matter which method you choose, it is important to remember that only you should have access to the private key.
Now let’s tell you what storage options are available:
- On paper or metal . This method is most relevant for paper wallets, but this way you can store a private key created by any method - you just need to rewrite it. However, such storage is not safe: you may lose the sheet, it may burn or get wet. For greater strength, it can be laminated or made from metal.
- On a flash drive . This is one of the most reliable methods. You need to use a separate flash drive (preferably new and checked for viruses) and perform all operations offline. There are several storage options: as a text document, a screenshot, or an original file in wallet.dat format. You also need to put a password on the flash drive.
- On the computer . This is also a fairly reliable storage option if the device is not connected to the Internet and is working properly. Otherwise, he may either become a victim of attackers, or “fly”. It is also recommended to set a strong password on the key file itself and on the computer.
- In mind . This is perhaps the most secure way to store a private key. However, it will only work if you used a mnemonic phrase as a private key. Because remembering a set of random numbers and letters is simply unrealistic.
6 - Decoding the QR code
The next step is to read the QR code and fill it with as many data and correction code words as possible from the table shown in step No. 5.
The first step is to remove the mask from the QR code. We used a Google spreadsheet to create the mask and the BITXOR function to apply it.
№°23 - When a mask is applied to a QR code, each green module of the mask changes the color of the module to the opposite one
The result of applying the mask is a readable QR code. Where to start reading a QR code and how to read it? The ISO standard explains how codewords are displayed on a QR code and provides rules for reading them (page 46: Codeword placement in the matrix).
Let's transfer the code words to our QR code.
No. 24—Positions of data and correction codewords. Regular and irregular shaped symbols are visible
Let's read them. Each character must be read differently depending on its shape and direction of writing, as shown below and as explained on page 47 of the ISO standard.
No. 25 - picture from Wikimedia Commons
The picture below shows an element-by-bit (bit-by-bit) diagram of a readable QR code. Each “X” is an unknown bit.
No. 26 - Decoding a QR code “manually”, bit by bit. Fun, right?
Now we read and fill out the tables of data codes and corrections from stage No. 4.
No. 27 —After reading the QR code and filling in the protocol bits, we add the data that we extracted when analyzing screenshots to the data code words
Codewords #1 and #2 are known because they are part of the protocol (Mode Indicator + Character Number Indicator).
Code words #3, #4, #6 and #7 are known from the analysis of screenshots at stage #2 (“ KyUzsR ”)
Codewords #54 to #60 are also known because they are part of the protocol (Terminator + Filler Bits).
Each “X” found increases the chances of successfully completing the error correction phase and halves the number of options for brute force selection, which we will use at the end of the journey.
You have probably already asked yourself the question: why did we set every fifth bit of the code words carrying the message/data to “0”? This is done because we know the alphabet of the private key (Base58Check) and all characters of this alphabet start with “0” if encoded in 8-bit format (the 5th bit of each codeword becomes the first bit of each letter of the message as a result of the shift that occurred from -for the bits of the first 12 protocols).
#28 - Table of error correction code words after we read the QR code. There is nothing we can do here, since they are all determined by the Reed-Solomon encoder
Now let's use the battle magic of the error correction code to recover as much data as possible.
Cryptography Security
Not all users consider Bitcoin private keys to be reliable protection for a public address. In reality, the likelihood of guessing such a complex password is less 0,000001%
.
Cashh App developer Danny Diekroeger is convinced that under similar circumstances, finding a private key could take 100 years
.
Even if you manage to guess the password, the probability that there will be bitcoins in your wallet is 0.000000000000000000000000000000000000000000000001%
. Therefore, it becomes economically unprofitable to use computing power to find the key.
That's a massive overestimation. I calculated the actual odds. Even at 1,000,000,000 times the current computer power he has, running for 100 years, the odds he finds any private key with a balance are:
0.0000000000000000000000000000000000000000000001%
— Danny Diekroeger (@dannydiekroeger) May 25, 2020