Today, many online services, especially those related to finance and making money on the Internet, offer to install additional protection for the user account. Even if attackers steal your login information (username and password), using such protection they will still not gain access to your account and data.
In most cases, two-factor authentication (2FA) is used to create this additional account protection. Many users simply ignore it because they don’t even want to understand its features and functions. That’s why I decided to write this article to explain in simple words what two-factor authentication is, how it works, where it is used, and how to configure it in different ways. The information is very important and will be useful to every active Internet user.
Two-factor authentication - what is it and why is it needed?
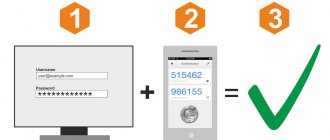
Two-factor authentication (TwoFactor Authentication or 2FA) is the most common type of multi-factor authentication, which is used to protect accounts from unauthorized access or confirm online transactions. Accordingly, in order to log into your account or confirm a certain action, you must go through 2 stages of personal identification:
- the first stage is to enter your account login and password;
- the second stage is an additional way to confirm that it is its owner who is in the account. This is done using one of the types of two-factor authentication, which I will discuss in more detail below.
One of the most important features of two-factor authentication is that the code to confirm a login or transaction is constantly changing. Therefore, every time you will receive new data that will be known only to you.
Why do you need two-factor authentication?
The main task of two-step identity verification is to keep your personal data safe and prevent attackers from gaining access and full control over your accounts in various services.
Imagine that another person will gain access to your social networks or email, allowing them to see your personal communications and files. Or much worse - it will take over the data of your electronic wallet or bank card. This can lead to serious irreversible consequences.
However, by setting up two-step authentication, even knowing your username and password, an attacker will not be able to log into your account. It is almost impossible to find additional code that is constantly changing, so your data will be under reliable protection.
How two-factor authentication works
Two-step authentication works much simpler than it might seem at first glance, and takes no more than 30 seconds. Let me clearly show how this process is carried out:
How two-factor authentication works
- You first connect and configure two-factor authentication to your account. Below in the article I will explain in detail how this task is performed.
- Every time you log into your account or perform a certain action (for example, transferring funds), you first go through the first stage - enter your permanent password.
- To complete the second stage, you need to provide a special two-factor authentication code, which will be sent by the method you choose.
- Automatic synchronization and verification of data occurs and, if the code was entered correctly, you gain access to your account or the operation is performed.
As I already noted, there are several types of multi-factor authentication, and you yourself choose the most suitable and convenient one for use. Let's start looking at them.
Authenticator apps for 2FA
Two-factor using applications is one of the popular and safe methods at the moment. Two-factor authentication apps work very simply. To connect them you will need:
- install the program on your phone.
- synchronize the application with the website using a QR code that can be scanned with your phone. Or enter a special code that will provide an Internet resource.
After starting the program, it will generate new passwords every 30 seconds. Codes are created based on a key that is known only to you and the server. Since both components are the same for both you and the service, the codes are generated synchronously. This algorithm is called OATH TOTP (Time-based One-time Password), and in the vast majority of cases it is used.
Compatibility of 2FA programs
Almost all authentication applications use the same algorithm. Therefore, you can use whichever one you like best. But there are also exceptions. For example, Blizzard Authenticator applications. It is made for Blizzard and cannot be used for other services.
Adobe also released its application called Adobe Authenticator. But this service allows you to use third-party authenticators. It is not clear why it was necessary to reinvent the wheel.
As practice shows, most IT resources allow you to use any 2FA application. And even if for some reason they want to control this process and create their own application, then most often they allow it to protect not only “their” accounts, but also the accounts of third-party services.
So you can choose any authenticator app you like and it will work with most services that support 2FA apps.
Popular two-factor authentication apps
If you start searching for 2FA apps on Google Play or the Apple App Store, you will see a large selection of these programs. And despite the same operating algorithm, preference should be given to those that have additional functions and a user-friendly interface. Below we will look at the most popular options.
Google Authenticator . It's the easiest to use two-factor authentication app out there. It doesn't even have settings. We will talk in more detail about how to work with this application in a separate section.
You can download it here: for Android, for iOS
Microsoft Authenticator. Microsoft also kept it simple and made its authenticator very minimalistic in appearance.
But at the same time, Microsoft Authenticator is noticeably more functional than Google Authenticator. Firstly, although all codes are shown by default, each of the tokens can be separately configured so that the code is hidden when the application is launched. You can download here: for Android, for iOS
Yandex.Key. This is the most successful two-factor authentication application available. On the one hand, it does not require you to register right away - you can start using it with the same ease as Google Authenticator. On the other hand, it has several additional features that are available to those who are not too lazy to go into the settings.
To enter the program, you can enter a PIN code or fingerprint. Create a password-protected backup copy of the tokens in the Yandex cloud (here you need to specify your phone number) and restore it on any of the devices you use. In the same way, it will be possible to transfer tokens to a new device when you need to move.
You can download it here: for Android, for iOS
Duo Mobile. Easy to use and lacks additional settings.
Compared to Google Authenticator, it has one advantage: by default, Duo Mobile hides codes - to see the code, you need to click on a specific token. If you feel uncomfortable every time you open the authenticator and show everyone around you a bunch of codes from all your accounts, then you will probably like this feature of Duo Mobile. You can download it here: for Android, for iOS
FreeOTP. There are four reasons why you might like this authenticator developed by Red Hat.
Firstly, this is your choice if you love open source software. Secondly, this is the smallest application of all reviewed - the iOS version takes up only 750 KB. For comparison: the minimalistic Google Authenticator takes up almost 14 MB, and the Authy application, which we will talk about below, takes up as much as 44 MB. Thirdly, by default the application hides codes and shows them only after touching. Fourth and finally, FreeOTP allows you to configure tokens manually with maximum flexibility if you need it for some reason. Of course, the usual way of creating a token by scanning a QR code is also supported.
You can download it here: for Android, for iOS
Authy .
The most sophisticated of the two-factor authentication applications, the main advantage of which is that all tokens are stored in the cloud. This allows you to access your tokens from any of your devices. At the same time, this simplifies the move to new devices - you don’t have to re-activate 2FA in each service, you can continue to use existing tokens. The main disadvantage of Authy is that the application immediately requires you to create an account linked to your phone number - without this you simply will not be able to start working with it.
You can download here: for Android, for iOS, for Windows, for macOS, for Chrome
What types of two-factor authentication are there?
Today, the following types of two-factor identification are widely used:
- Authentication through an application is one of the most reliable 2FA methods, for which you need to install a special application on your mobile device. For example, Google Authenticator is great. Such applications generate one-time passwords that are valid for only 60 seconds, after which they are replaced with a new one;
- via e - mail - perhaps the most common method of two-step verification. For confirmation, a message with a code will be sent to your email address;
- via SMS message - a secret one-time code is sent to your mobile device to a pre-specified number (linked to your account or bank account);
- using a messenger - as a rule, Telegram is used and secret codes are sent to your attached account (contact);
- additional password, secret question, code word - a rather rarely used method of two-factor authentication. For it, you need to come up with another password in advance, which will be used only in certain situations;
- the key on a physical medium – as a rule, it is a USB flash drive with an access key;
- biometric data – fingerprint, facial recognition, etc.
Important: most of the listed authentication methods are completely free. However, some of them, such as sending an SMS message, may charge small amounts of money.
Often, after registering on a particular site, you will be offered several ways to protect your account by enabling 2-Step Verification. Typically, this process is carried out in the “Security” settings.
On most sites you can often find several options for connecting 2FA, among which two-factor authentication is most often used, implemented through the Google Authenticator application or by sending SMS codes to a mobile phone, as well as entering a password from E-mail, and there is always the opportunity to choose the most convenient option for you.
On some projects it is not necessary to do this at all (optional), and on some sites, enabling two-factor authentication is a mandatory process. Let's look at specific examples of using this function.
One-time codes in a file or on a piece of paper
The simplest replacement for one-time passwords sent via SMS are the same one-time passwords, but prepared in advance. This is not the worst option, especially for those services in which you need to log in relatively rarely. Actually, even for the same Facebook, this method may well be suitable, especially as a backup login method.
It works very simply: upon request, the service generates and displays a dozen one-time codes on the screen, which can later be used to confirm login. Then you simply print or copy these codes onto paper and put them in the safe. Or, even easier, save it in encrypted entries in a password manager.
In general, it doesn't really matter whether you store these codes on warm lamp paper or in soulless digital form - it's important to store them so that they a) don't get lost and b) can't be stolen.
Where is two-factor authentication (2FA) used?
There are a huge number of services and sites where two-step authentication works. You even use many of these projects on a daily basis and may not be aware of the presence of this useful feature. Namely:
- electronic payment systems (wallets);
- social networks and instant messengers;
- email services;
- sites for making money on the Internet;
- financial structures;
- exchanges, including cryptocurrency ones;
- gaming services;
- and many other projects.
In other words, in almost every area and structure where your personal data or funds are stored, additional protection can be installed. I’ll tell you later how to enable two-factor authentication.
How to enable 2FA?
Detailed instructions for activating google authenticator, how the protection scheme works, and what is necessary for its functioning. As an illustrative example, let’s choose the largest and most popular crypto exchange, Binance.
First of all, register on the website https://www.binance.com. In principle, any serious crypto exchange has instructions for setting up two-factor authentication using Google Authenticator, we will simply outline it in general terms so that novice traders are prepared in advance.
To connect and configure 2fa code, you will need a smartphone or tablet with the application installed and access to your account.
Advantages and disadvantages of two-factor authentication
Two Factor Authentication has its own advantages and nuances that are important to know about before use. Let's start with the positive features:
- by connecting one of the types of 2FA, you significantly increase the security of your account and the data on it;
- two-factor authentication is easily activated in a few clicks and is also easy to use in the future;
- in most cases, you do not need to pay money for additional account protection;
- new login and confirmation passwords are unique each time, so they are almost impossible to guess or guess;
- By enabling 2FA on all accounts, you can use the same easy-to-remember password (but despite this, I would still recommend that you always use different passwords for each service).
But two-step authentication also has disadvantages:
- if you often perform the same action during the day (log into your accounts, transfer money, etc.), you will need to enter a secret code each time;
- If you are outside the coverage area of your mobile operator, you will not receive an SMS with the code. But as an option, you can take care of creating backup one-time codes in advance; however, not all services may offer this method of two-step verification.
- If you lose access to 2FA, it will be very difficult for you to regain access to the account itself - you will need to contact support and prove ownership;
- two-step authentication does not protect 100% - experienced attackers can intercept messages, clone SIM cards, etc.
But for the most part, the shortcomings are far-fetched. Therefore, if the ability to connect two-step authentication is available, you should definitely use it.
“Iron” FIDO U2F authenticators: YubiKey and all, all, all
If an application that generates one-time codes seems too ephemeral to you to protect your accounts, and you want something more permanent, reliable and tangible - literally lock your account with a key and put it in your pocket - then I have good news for you: this option also exists. These are hardware tokens of the U2F (Universal 2nd Factor) standard created by the FIDO Alliance.
How FIDO U2F Tokens Work
Hardware U2F tokens are very popular among security specialists, primarily because from the user’s point of view they work very simply. To get started, just connect the U2F token to your device and register it with a compatible service, and this is done in just a couple of clicks.
Subsequently, if you need to confirm your login to this service, you will need to connect the U2F token to the device from which you are logging in and press the button on the token (in some devices, enter the PIN or place your finger on the scanner). That's all - no complicated settings, entering long sequences of random symbols and other dances with a tambourine, which everyone usually imagines when the word “cryptography” is mentioned.
Insert the key and press the button - and that's really it
At the same time, “under the hood” everything is arranged very cleverly and cryptographically secure: when registering a token on the service, a pair of cryptographic keys is created - private and public. The public key is stored on the server, and the private key is stored in the Secure Element secure storage, which is the heart of the U2F token - and this key never leaves the device.
The private key is used to encrypt the login confirmation, which is sent to the server and can be decrypted using the public key. If someone on your behalf tries to transmit a login confirmation encrypted with an incorrect private key, then when decrypted using a public key known to the service, instead of a confirmation it will turn out to be nonsense, and the service will not allow him into the account.
What are U2F devices?
The most famous and widespread example of U2F is the YubiKey, which is manufactured by Yubico. Actually, she was at the origins of this standard, but chose to make it open, which is why the FIDO Alliance was created. And since the standard is open, you are not limited in your choice: U2F-compatible devices are produced and sold by different companies - you can find many different models in online stores.
YubiKey is probably the most popular U2F token
For example, Google recently introduced its hardware authenticator suite, Google Titan Security Keys. In fact, these are keys produced by Feitian Technologies (the second most popular manufacturer of U2F tokens after Yubico), for which Google wrote its own firmware.
Of course, all hardware authenticators compatible with the U2F standard will work equally well with all services that are also compatible with this standard. However, there are several important differences between different models, and the most important of them is the interfaces with which the “dongle” is equipped. This directly determines which devices it can work with:
USB
- for connecting to computers (
Windows, Mac or Linux
- it doesn’t matter, the “keys” work without installing any drivers). In addition to regular USB-A, there are “dongles” with USB-C.
NFC
— required for use with
Android
.
Bluetooth
— will be needed on those mobile devices that do not have NFC. For example, iPhone owners still need a Bluetooth authenticator: although iOS has already allowed apps to use NFC (until 2022, only Apple Pay allowed this), the developers of most U2F-compatible apps have not yet taken advantage of this opportunity. Bluetooth authenticators have a couple of disadvantages: first, they need to be charged, and second, they take much longer to connect.
Basic models of U2F tokens usually only have support for U2F itself - such a key will cost $10–20. There are more expensive devices ($20–50) that can also work as a smart card, generate one-time passwords (including OATH TOTP and HOTP), generate and store PGP encryption keys, and can be used to log into Windows, macOS and Linux and so on.
How to bypass two-step verification?
It is worth understanding that two factors are a good measure of protection, but not a panacea, and there are a number of methods that allow you to get around everything:
- using a phishing site similar to typosquatting;
- by stealing a mobile device or other access factor;
- by duplicating the SIM card;
- using malicious software that will intercept user requests and SMS messages.
Step-by-step instructions for installing and configuring Google Authenticator
You can download and install Google Authenticator using the official links:
- Google Authenticator for iOS (iPhone, iPad) - https://apps.apple.com/
- Google Authenticator for Android (android) - https://play.google.com/
If you have an Android device, open Google Play Market and find google authenticator there, but the lucky owner of an Apple product needs to perform a similar action in the App Store. You can download the apk file (for Android) from another source, but this is not the most reliable option.
The service will display a QR code and a backup key. Open Google Authenticator and click the camera symbol to have the program scan the barcode.
If for some reason a failure occurs, for example, your camera does not work, enter the 16-digit 2FA key in the application interface on your smartphone and click the “ Add ” button. It doesn’t matter whether you added an account automatically or manually, in no case do not forget to save the connection code in a safe place (preferably on paper).